| Category | Details |
|---|---|
| Threat Actors | User “solidit-dev-416” on npm; possibly tied to broader campaigns using Quasar RAT. |
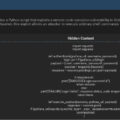
| Campaign Overview | • Malicious npm package (ethereumvulncontracthandler) deploys Quasar RAT to compromise developer systems. |
| Target Regions (Or Victims) | • Developers using npm, especially those involved with Ethereum smart contracts. |
| Methodology | • Disguised as a legitimate npm package. • Obfuscated code retrieves and executes a malicious script. • Deploys Quasar RAT to establish persistence and control. |
| Product Targeted | • Ethereum developers and projects. • GitHub repositories promoting pirating software and cryptocurrency bots. |
| Malware Reference | Quasar RAT (first released on GitHub in 2014). |
| Tools Used | • Malicious npm package. • Obfuscation techniques (Base64, XOR encoding, minification). • PowerShell commands for payload execution. |
| Vulnerabilities Exploited | • Trust in npm registry. • Developers’ reliance on GitHub stars as a quality signal. |
| TTPs | • Avoids sandbox environments. • Executes PowerShell commands to deploy malware. • Contacts C2 server for instructions and exfiltration. |
| Attribution | Not explicitly attributed, but uses Quasar RAT, a known tool for cybercrime and espionage. |
| Recommendations | • Scrutinize npm packages before installation. • Monitor unusual PowerShell activity. • Use endpoint protection to detect and block RATs. • Avoid relying solely on GitHub stars to assess repository trustworthiness. |
| Source | The Hackers News |
Read full article: https://thehackernews.com/2025/01/malicious-obfuscated-npm-package.html
The above summary has been generated by an AI language model



Leave a Reply