BlackCat Ransomware Affiliate TTPs | Huntress
Category Details Threat Actors ALPHV/BlackCat Ransomware group, using Ransomware-as-a-service (RaaS). Campaign Overview Attack targeting healthcare…
Ransomware Deployment Attempts Via TeamViewer | Huntress
Category Details Threat Actors Unknown actor, possibly related to LockBit 3.0 Ransomware campaigns. Campaign Overview…
Top-Ranking Banking Trojan Ramnit out to steal payment card data
Category Details Threat Actors Ramnit Gang Campaign Overview Ongoing campaigns targeting e-commerce brands and hospitality…
Trickbot Rising — Gang doubles down on infection efforts to amass network Footholds
CategoryDetailsThreat ActorsITG23 (TrickBot Gang/Wizard Spider), Hive0105 (BazarCall), Hive0106 (TA551/Shathak/UNC2420), Hive0107Campaign OverviewAggressive malware distribution expansion targeting…
Dissecting Sodinokibi Ransomware Attacks: Bringing Incident Response and Intelligence Together in the Fight
Category Details Threat Actors Sodinokibi (REvil), QakBot operators, Valak operators, ransomware affiliates (e.g., Clop, Ryuk,…
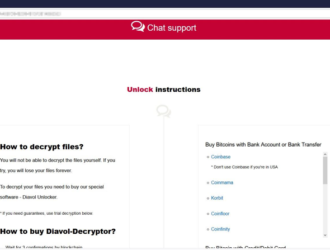
Analysis of Diavol Ransomware reveals possible link to TrickBot gang
Category Details Threat Actors Likely linked to the TrickBot group (ITG23), a well-known cybercrime Syndicate…
-330x250.jpg)