Let us quickly recap the features released in Qualys Vulnerability Management, Detection & Response (VMDR) in 2024 and understand their use cases and benefits.
Every quarter, the Qualys Product Management team collaborates with multiple customers worldwide, develops innovative solutions that address pain points experienced by customers’ Vulnerability Management teams, and simplifies some of those manual/repeated use cases.
This blog post will help you understand these use cases and how they can benefit your day-to-day activities.
MITRE ATT&CK Matrix Prioritization
Earlier this year, the Qualys VMDR team launched MITRE ATT&CK matrix prioritization in VMDR.
With this feature, you will be able to see vulnerabilities mapped to MITRE ATT&CK Tactics and Techniques. This gives an attacker-centric view with the top ATT&CK Tactics and Techniques from an attacker’s perspective, which will help you adopt a Threat-Informed Defense to reduce your risk posture.
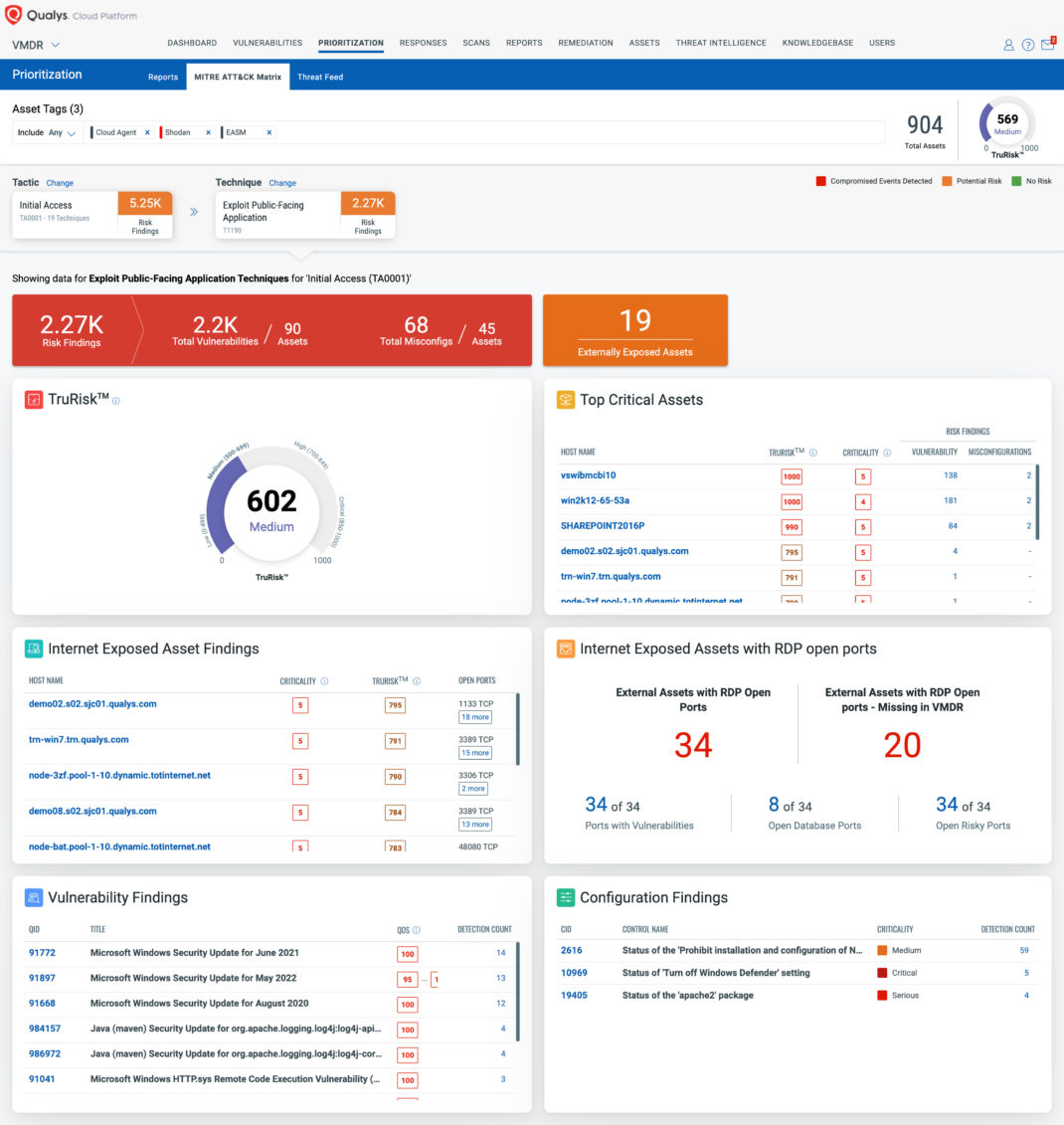
The MITRE ATT&CK Matrix Prioritization is not only specific to vulnerabilities; it also includes misconfigurations from Policy Compliance and Qualys EDR incidents. This enables organizations to predict and identify potential threats in advance, make informed decisions to prioritize and address them promptly, and thus stay one step ahead of attackers.
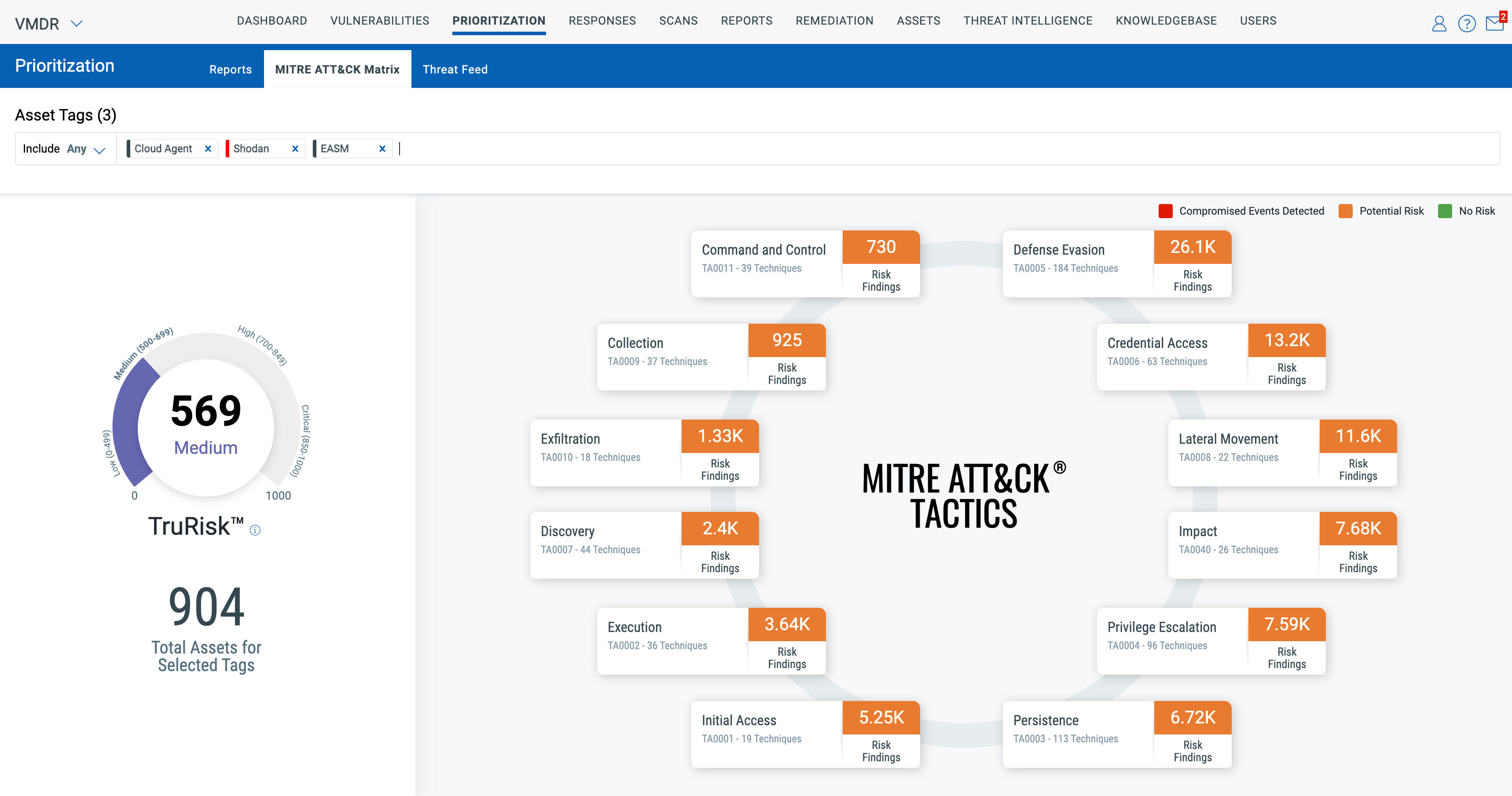
Qualys now stands out as the only enterprise-scale solution to combine TruRisk and MITRE ATT&CK to manage cybersecurity risks proactively and enhance detection and response in a single platform, thus helping you stay one step ahead of attackers.
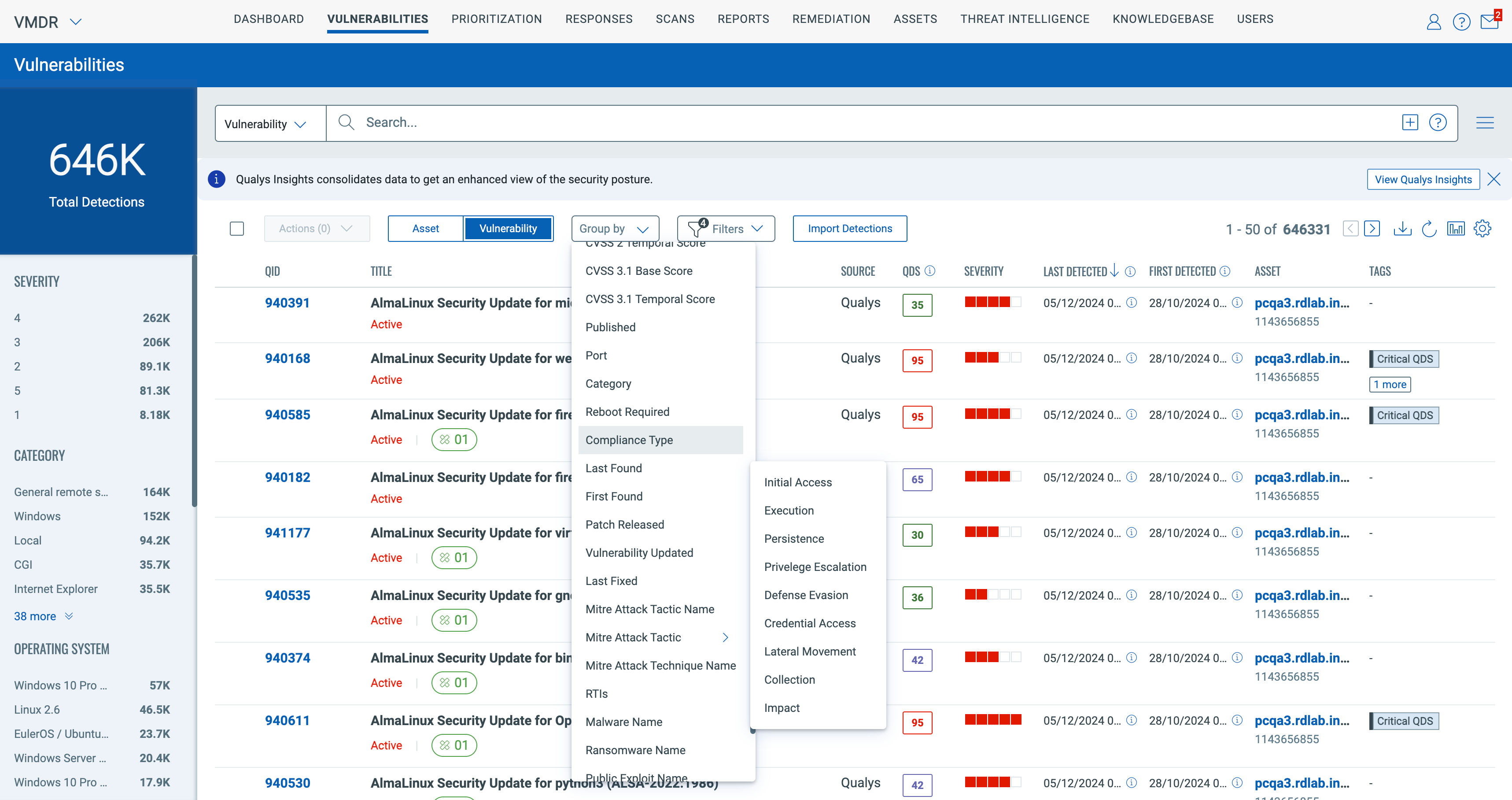
With this feature, from the Qualys VMDR – Vulnerabilities page, you can group vulnerabilities by the MITRE ATT&CK Tactic & Technique; this will give the ability for the vulnerability analyst to know the open vulnerabilities and their mapping to the Tactic and Technique. The same “group by” option is available in the Dashboard to track these with your remediation owners.
Vulnerability Tagging in VMDR
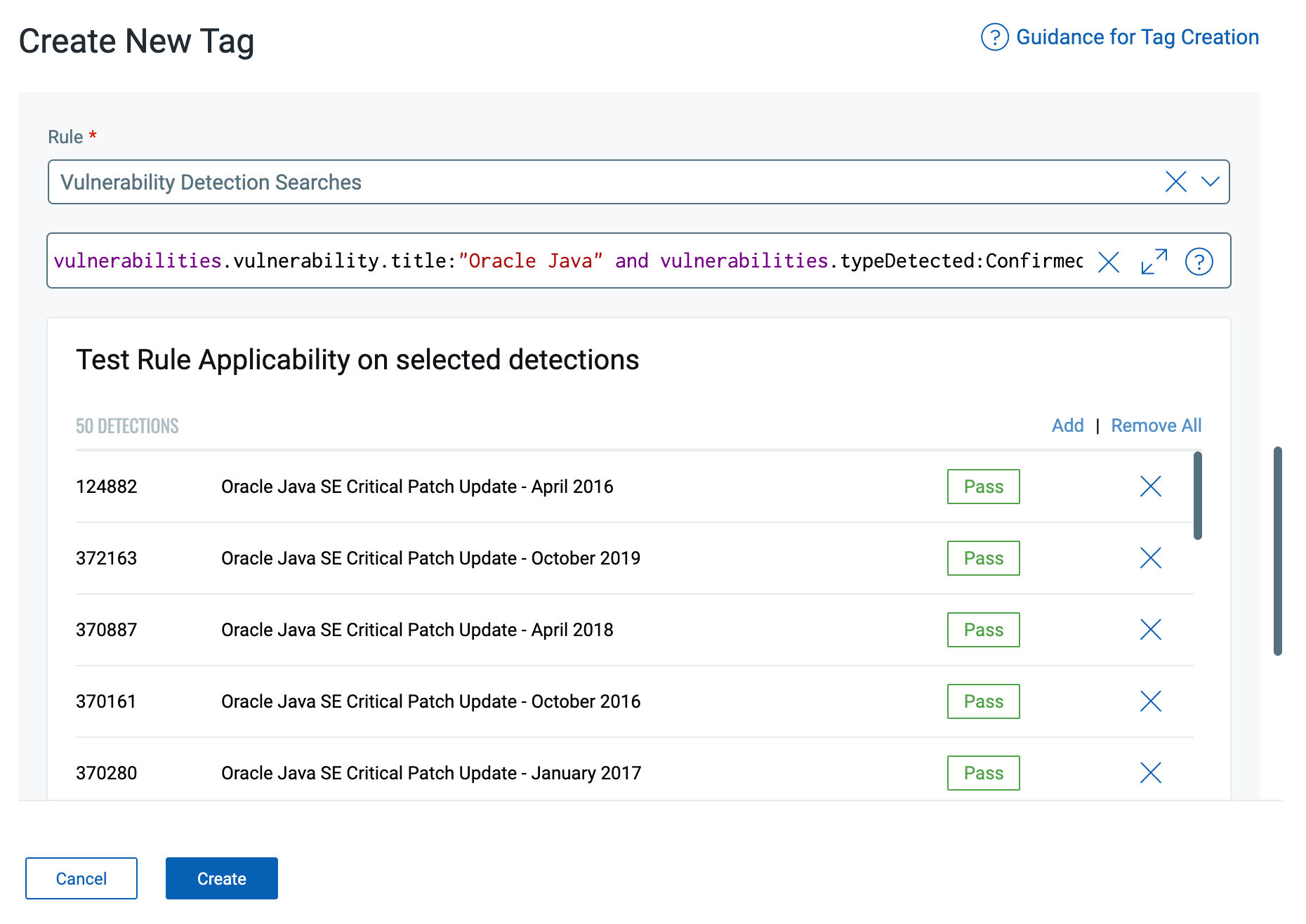
We have extended the asset tagging capability for vulnerability QQL/Tokens. With this, you will be able to tag vulnerability detections using attributes such as Vulnerability Title, QID, Qualys Detection Score, Vulnerability Severity, Status, ThreatIntel RTIs, Vendor or Product Names, and more.
The Vulnerability Tagging rules can be Static or dynamic. Static tagging is limited to the selected vulnerability findings only. With the word Dynamic, based on the upcoming detections matching to the given QQL, the tagging will be reevaluated, and the detections will ensure the tags are always up to date.
Customers can use the dynamic rules to tag vulnerabilities, route them to specific teams based on their attributes, and alert them – for example, route OS vulnerabilities to the IT team and open-source vulnerabilities to the App Team.
These vulnerability tags can be queried or used in the Dashboard Widgets and in the VMDR – Vulnerabilities listing page.
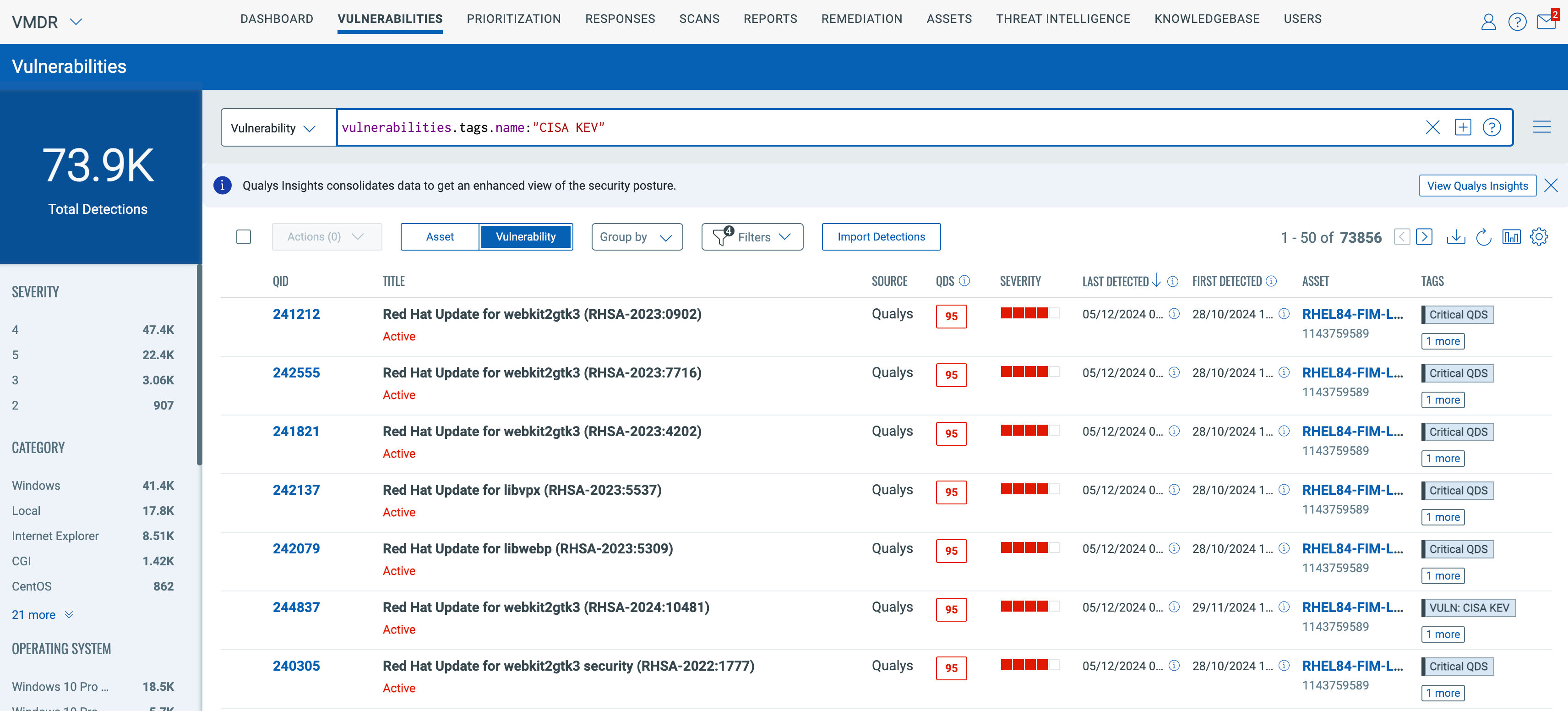
Note: In the upcoming quarters, the same vulnerability tagging will be available in the Report tab and supported by the HLD APIs. The same tag can used for generating vulnerability reports.
Software Composition Analysis (SwCA) in VMDR
Software Composition Analysis (SwCA) is bundled with your VMDR subscription at no additional cost. With this capability, Qualys VMDR will be able to detect any vulnerability related to Open-Source Software (OSS) components.
Most organizations use OSS libraries for their applications’ software packages; such libraries are at the core of modern software development for Java, Go, .NET, Python, Node JS, Rust, Ruby, PHP, and more. A sizable portion of codebases in contemporary applications comprises multiple open-source software packages, and studies have shown that:
- 96% of code bases contained open-source software (OSS), and 48% included high-risk vulns.
- 91% of packages had OSS with no development activity in the last two years.
- The average code base incorporates 56 vulnerable open-source packages per asset, and 41% had an exploitable vulnerability.
SwCA helps you understand the components in your software stack, empowering developers to harness the potential of open-source packages while managing the risk to your organization. At the same time, SwCA ensures organizations remain shielded from avoidable vulnerabilities and legal and compliance concerns.
Qualys has added Runtime Software Composition Analysis capabilities into the Qualys Cloud Agent. This empowers the Cloud Agent to detect, manage, and reduce the risk of software supply chain vulnerabilities in the production environment without introducing new infrastructure, tools, or processes.
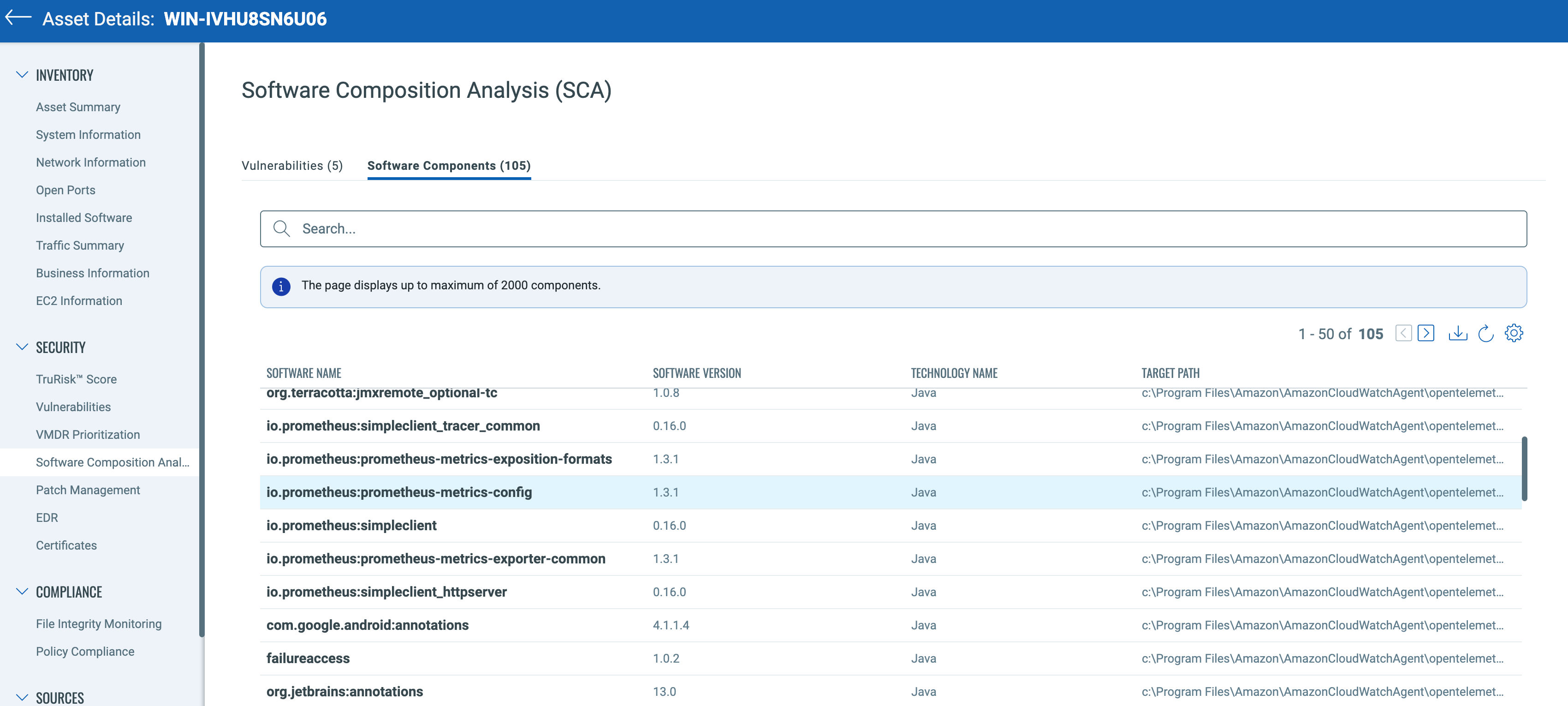
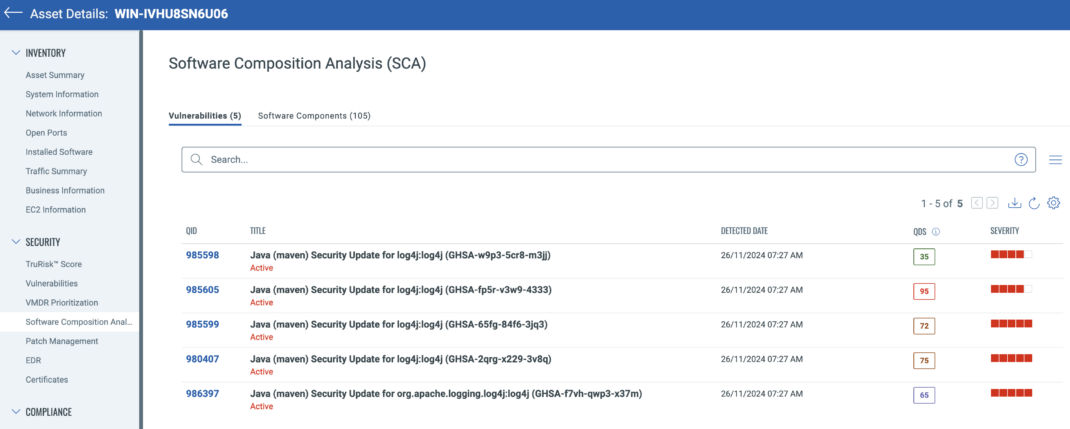
Runtime Software Composition Analysis offers continuous and real-time visibility of deeply embedded open-source packages and commercial software components in producing first-party and third-party applications on Windows and Linux operating systems.
Enriching TruRisk with CISA KEV Due Date & EPSS
Qualys VMDR with TruRiskTM is the most comprehensive way to classify vulnerabilities as risky based on multiple parameters, such as CVSS, CISA KEV, Exploit Core Maturity, Malware, Ransomware, and Threat Actor. It also reports the recent trend of this vulnerability in the threat actor forums.
Qualys has subscribed to more than 25+ Threat Intelligence feeds to classify the highest risky vulnerabilities. This data is further available in VMDR to report the most critical vulnerabilities based on the Qualys vulnerability assessment.
It emphasizes risk-based vulnerability management, offering a more nuanced approach that prioritizes vulnerabilities based on the potential risk they pose to the organization.
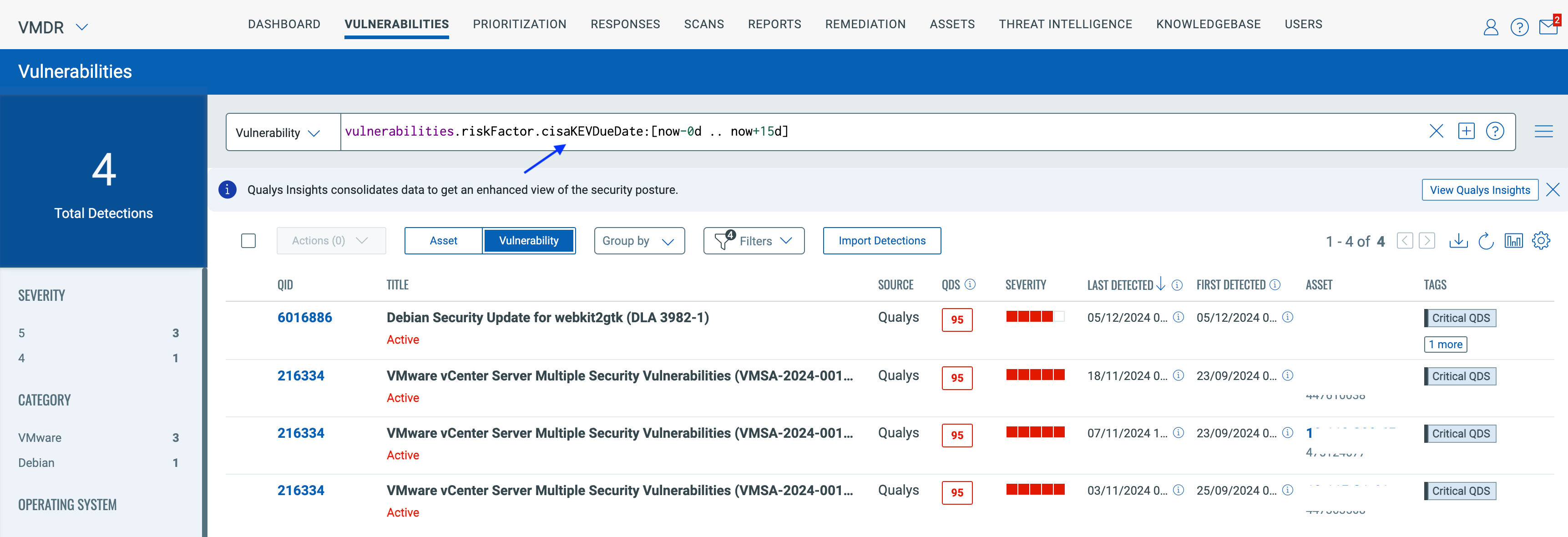
CISA KEV Due Date: The Qualys Detection Score is enriched further by adding the CISA KEV due date, which QQL can use to determine the upcoming due date for these.
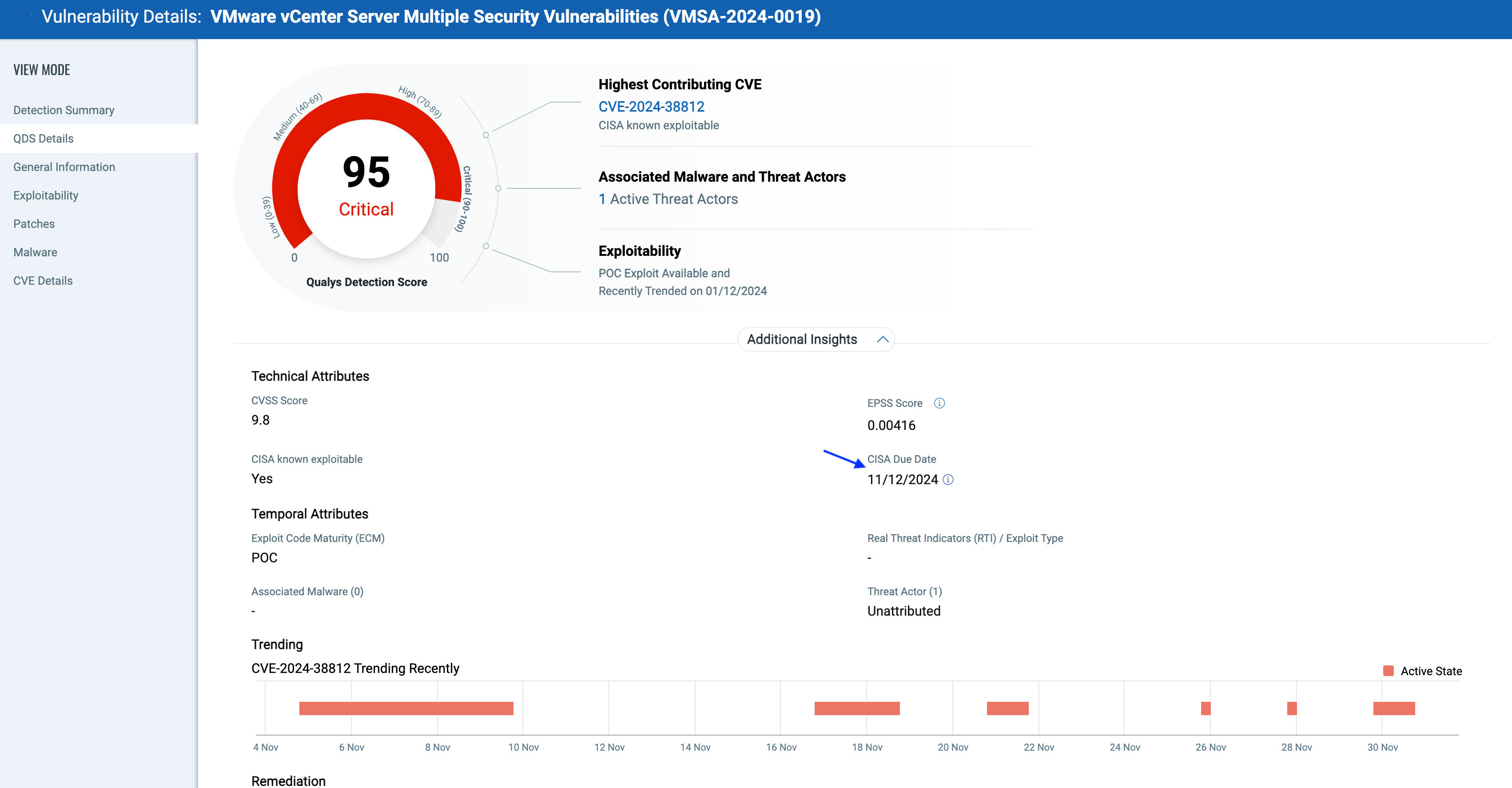
Customers can use the below CISA KEV Due date query to proactively identify upcoming CISA KEV vulnerabilities approaching the due date defined by the CISA and ensure the timely remediation of these vulnerabilities.
Knowing the CISA dates helps teams address vulnerabilities promptly, reducing the exposure window to potential attacks.
CISA date fields offer documented evidence of when vulnerabilities were disclosed and resolved, aiding organizations in meeting compliance obligations.
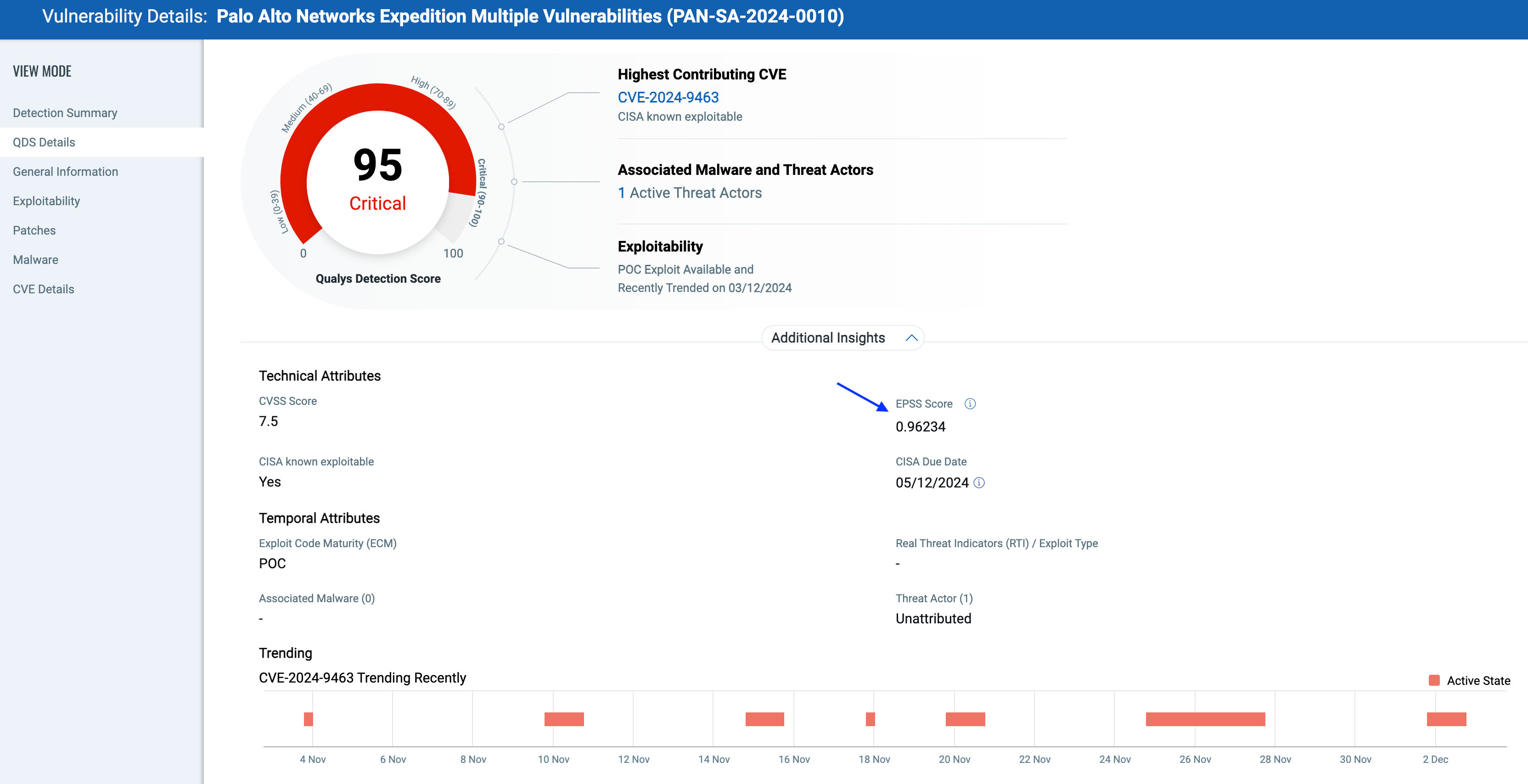
Exploit Prediction Scoring System (EPSS) has been added as a technical attribute factor in QVS/QDS to enhance vulnerability prioritization. The Qualys Detection Score is leveraged to report this in the risk calculations, giving additional visibility into the likelihood of the vulnerability being exploited. It provides the probability a vulnerability will be exploited over the next 30 days.
EPSS helps to analyze the severity of the vulnerability and prioritize its remediation efforts.
Qualys API Support for EPSS: EPSS is added to the Host List Detection API and KnowledgeBase (CVE-centric API) API as a QDS factor. We have made changes to the following APIs:
- Host List Detection /api/2.0/fo/asset/host/vm/detection
- KnowledgeBase QVS Download in JSON Format /api/2.0/fo/knowledge_base/qvs
Recent VMDR BETA Features
The Qualys Product team often releases multiple beta features to its customers before they are Generally Available (GA) to all customers. These features are activated for multiple customers. The Qualys team received very good feedback from multiple customers and is working to enrich these features further.
To activate the beta features mentioned below, please reach out to Qualys Support or your Technical Account Manager.
TruRisk Executive Summary Report
The TruRisk Summary report provides executives with a comprehensive overview of the organization’s security risk landscape based on TruRisk analysis. This report offers unprecedented insights into an organization’s security risk posture and actionable insights, empowering executives to prioritize and address the most critical risks efficiently. Armed with actionable insights, practitioners and managers can present the organization’s security posture to Chief Information Security Officers (CISOs).
Report Insights Overview – The report provides the following insights:
- TruRisk Contributing Factors: A comprehensive overview of various factors contributing to the TruRisk score of the selected asset tags. For example, associated known threat actors, external facing assets, and so on.
- Tags Analysis: Top risky asset tags based on the TruRisk score.
- Asset Landscape: Assess the vulnerable assets landscape based on the TruRisk score contributing factors.
- Assets with Critical TruRisk: Assess the critically vulnerable and external-facing assets landscape.
- Weekly Insights Assets: Snapshot of assets from the last seven days.
- Weekly Insights Vulnerabilities: Vulnerability snapshot from the last seven days.
- Vulnerabilities Landscape: Assess the vulnerability landscape based on critical vulnerability types and patch details.
- CVSS vs. Qualys Detection Score (QDS): Comparison with CVSS, EPPS, and TruRisk.
- Weekly Insights Vulnerabilities: Vulnerability snapshot from the last seven days.
- Risk reduction recommendations, and many more.
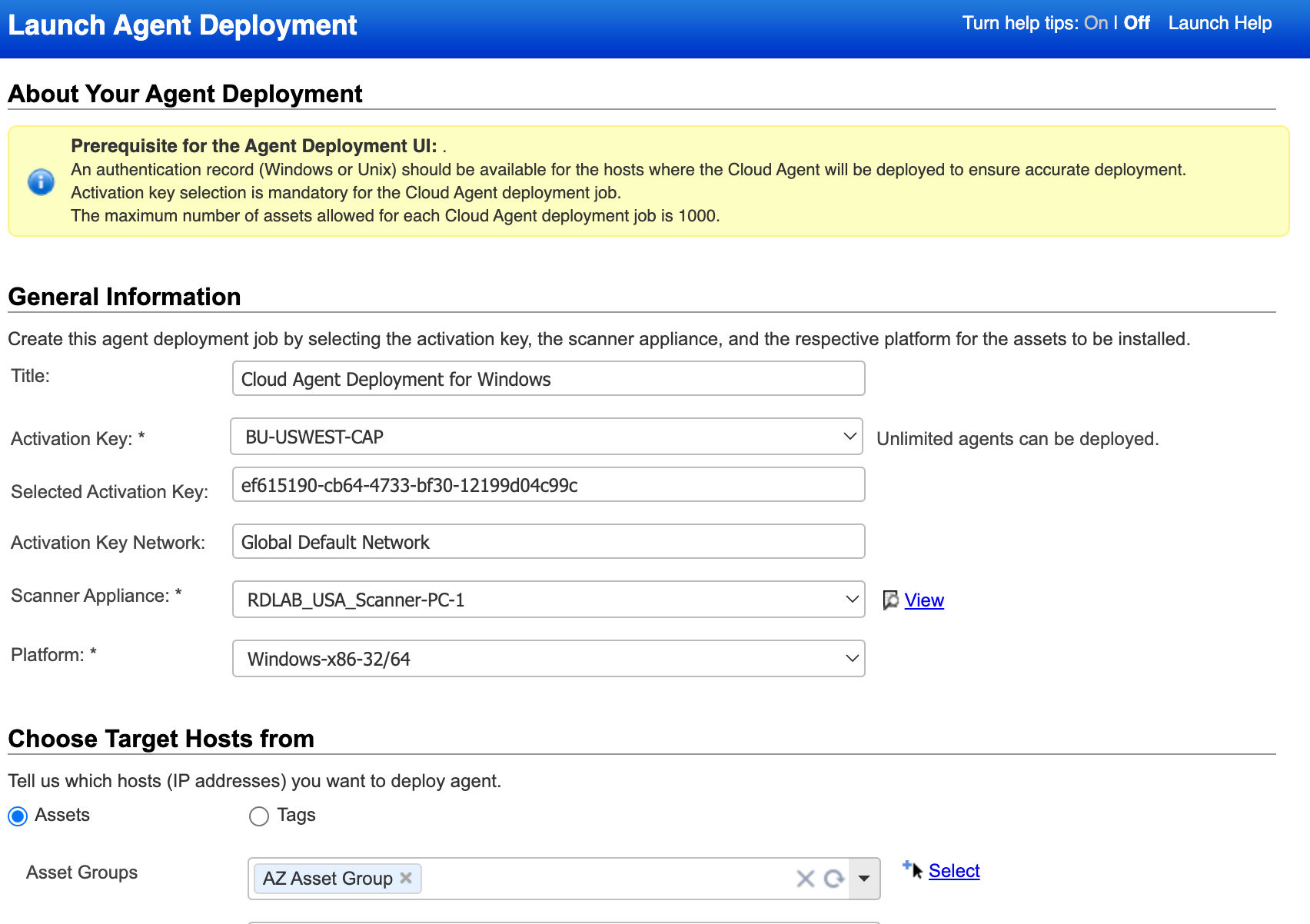
Remote Cloud Agent Deployment using Scanner
Cloud Agent deployment is simplified by leveraging the Virtual/Physical Scanner using your existing Authentication Records. The Cloud Agents can be deployed easily without a dependency on remote software deployment tools or your infrastructure teams.
Assets can be identified without the Cloud Agent and deployed remotely using the Scanner appliance with Authentication to ensure complete coverage.
The deployment of Cloud Agent is supported for Windows/Linux assets; this can:
- Significantly streamline the Cloud Agent installation process.
- Reduce deployment time and effort as there is no need to rely on third-party tools to install Cloud Agents.
- Enhance operational capabilities by simplifying the Cloud Agent deployment workflow that is integrated with the Qualys Cloud Platform.
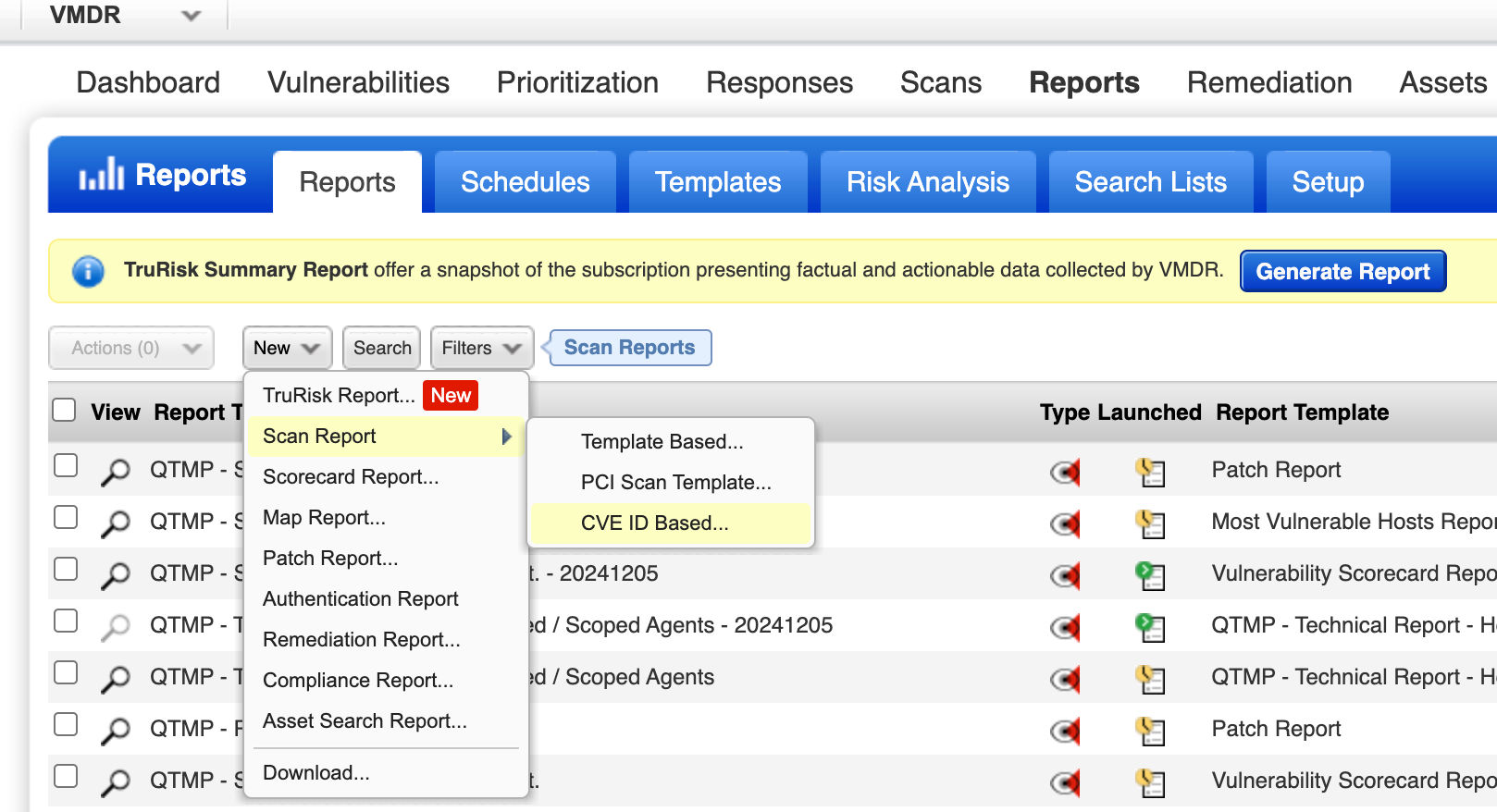
CVE-Based Reporting
Qualys VMDR users can now generate a CVE ID-based report to understand the current vulnerabilities and security risks based on the Qualys Vulnerability Score (QVS). CVE ID-based reports are available in both UI and API. We have also introduced a new API endpoint for this. Additionally, users can create a new CVE ID-based report template to generate reports. Customers will also be able to group vulnerabilities based on the vulnerable CVE.
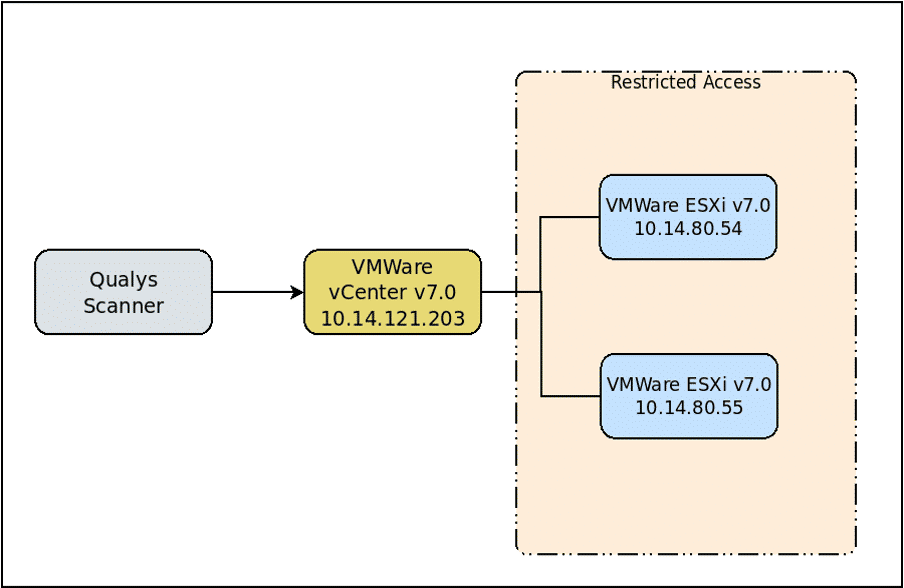
Disconnected ESXi Hosts Scan
Gain visibility into both connected and disconnected VMware ESXi hosts, identify your blind spots by scanning through your vCenter, and obtain an accurate inventory of ESXi hosts that are unreachable from your Qualys appliances.
Using the existing vCenter Authentication, the Qualys scanner will make a single API call to vCenter and gather details such as build, version number, and configuration details of the disconnected ESXi hosts. The scan results will show data for vCenter and associated disconnected ESXi hosts.
With this, you get complete visibility into your connected and disconnected ESXi hosts.
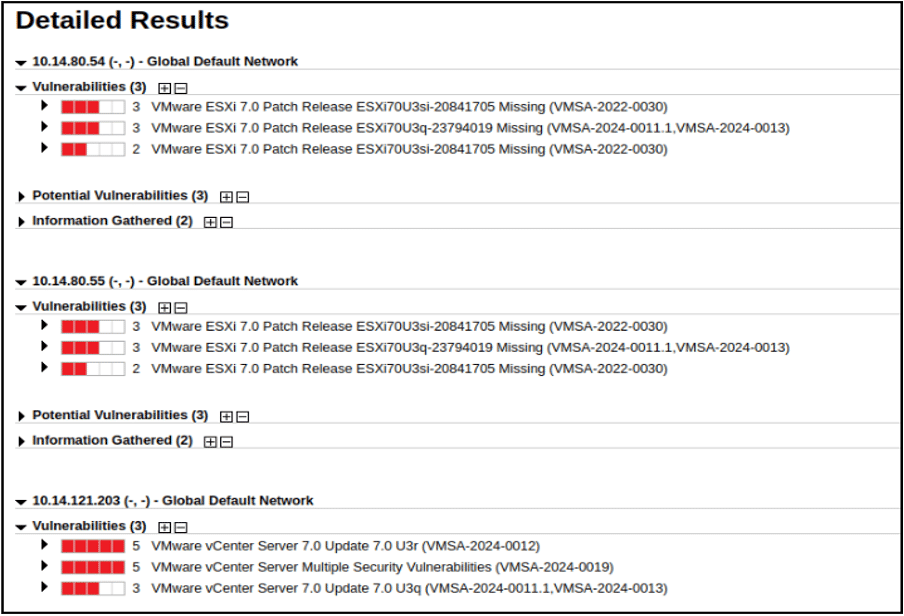
Here is the scan result: The Qualys scanner is able to detect the vulnerabilities of the Disconnected ESXi hosts by scanning the vCenter.
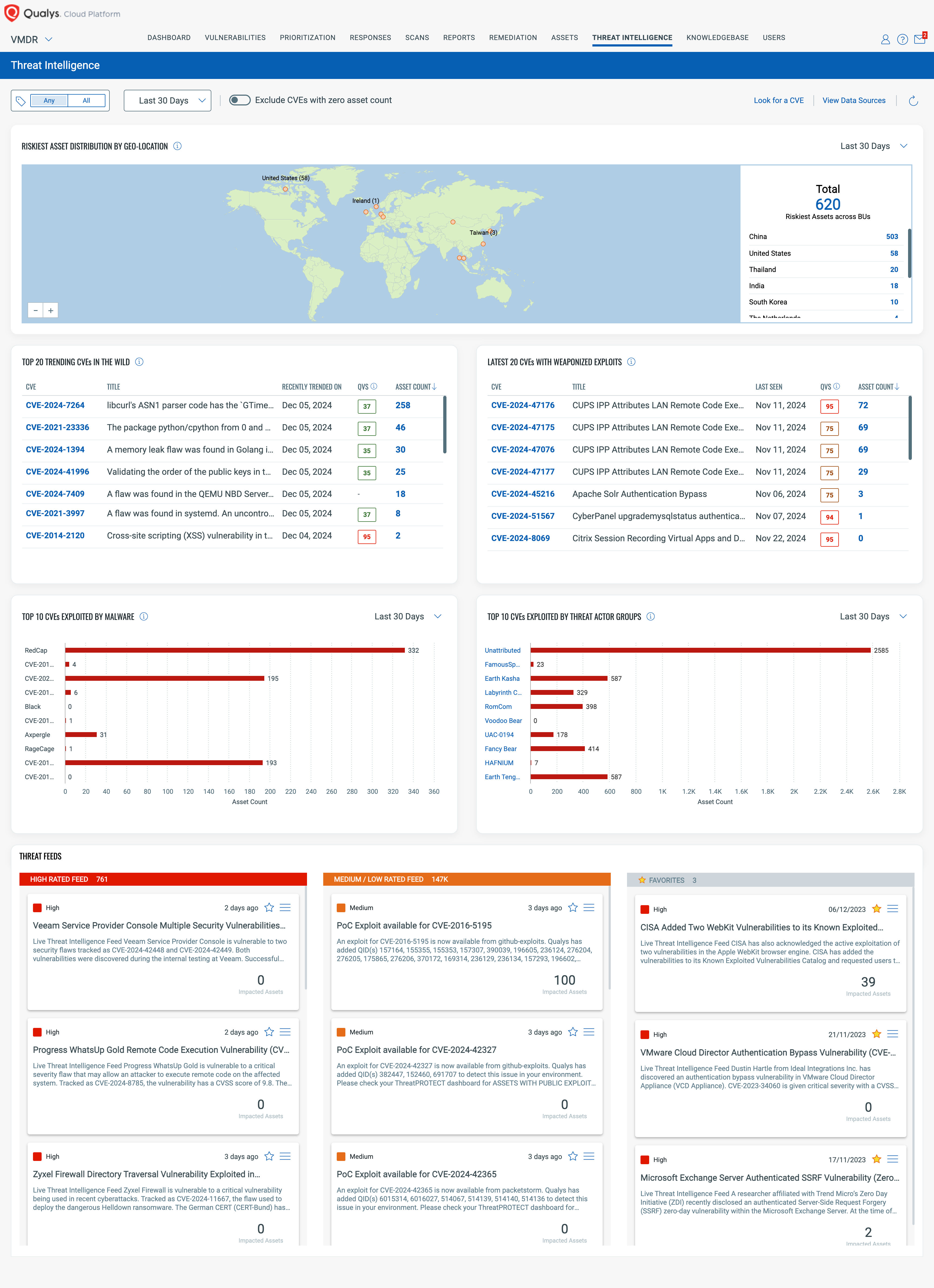
Threat Intelligence in VMDR
With Threat Intelligence, you can access a comprehensive list of cyber threats and prioritize remediation actions more effectively. By leveraging Qualys’ real-time threat intelligence, you can stay informed about top-trending CVEs, widely exploitable vulnerabilities, malware-associated threats, your riskiest assets across geographies, and more, all in real time.
This new view offers a comprehensive collection of widgets, including CVEs, a count of impacted assets, and CVE search with auto-suggestion threat intelligence widgets.
Below are the Threat Intelligence widgets that customers can leverage:
- Riskiest Asset Distribution by Geo-Location
- Top 20 Trending CVEs in the Wild
- Latest 20 CVEs with Weaponized Exploits
- Top 10 CVEs Exploited by Malware
- Top 10 CVEs Exploited by Threat Actor Groups
Vulnerability Alerting – VMDR Responses
The Responses tab in the VMDR application allows customers to create rule-based alerting for resources that might fail certain critical evaluations and thus helps in fixing resource misconfigurations. The Responses tab allows you to trigger alerts using alerting tokens in the Rule Query. You are notified about these alerts via the actions you select while creating the alerts.
This serves the purpose of quick communication to multiple stakeholders for any critical vulnerability detections on crown jewel/internet-facing assets.
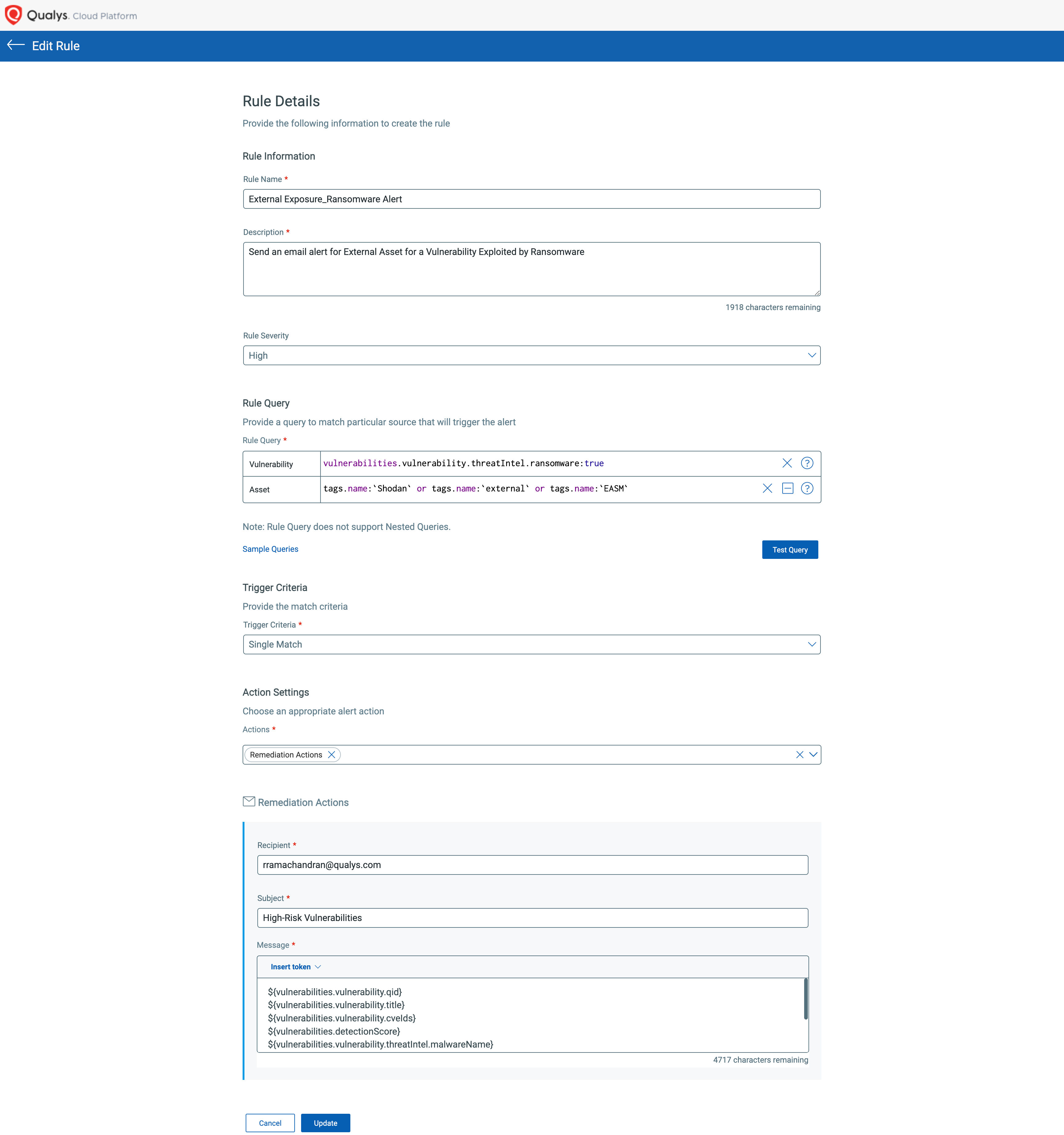
Use the Vulnerability and Asset QQLs/Tokens to trigger alerts to multiple resolver groups/security teams that need immediate attention for critical vulnerability findings. Receive alerts. These alerts can be sent as Emails, PagerDuty messages, or Slack Messages or ServiceNow – VMDR for ITSM integration.
Google Cloud Platform (GCP) – Perimeter Scans
Leverage GCP Cloud Perimeter Scanning to identify vulnerabilities in public-facing virtual machines and enhance the security of your Google Cloud Platform environment.
Utilize Qualys Connectors for comprehensive scan coverage of your cloud workloads. These connectors provide visibility into your instances and cloud resources. Additionally, enhance your scanning strategy with FlexScan, which offers a multi-dimensional approach, including Zero-Touch API-based and Snapshot-based scans.
With this, VMDR is compatible with scanning the perimeter devices for the top three Cloud Service Providers.
With this release, customers can scan the Internal Assets and instances hosted at the Perimeter level. With the GCP Connector, you will be able to see the Instances and Resources hosted in the Cloud.
Gain end-to-end visibility of your cloud infrastructure and stay ahead in the game to detect and prioritize the vulnerabilities with the remediation owners.

Containerized Scanner Appliance
The Qualys Containerized Scanner Appliance (QCSA) enables customers to scan containerized environments effectively for vulnerabilities, ensuring the security of containerized applications and infrastructure. This scanner appliance helps deploy the same network scanning capabilities of virtual and physical scanners on a Docker container.
The QCSA can Scale up and down dynamically based on the increase in the scan targets increases, and can be scaled up or down according to the requirement.
The QCSA will save virtualization platform costs. Instead of spending on expensive virtualization platforms for your on-premises scanners, you can leverage the Linux + Docker + QCSA stack and get the same standardization benefits and more!
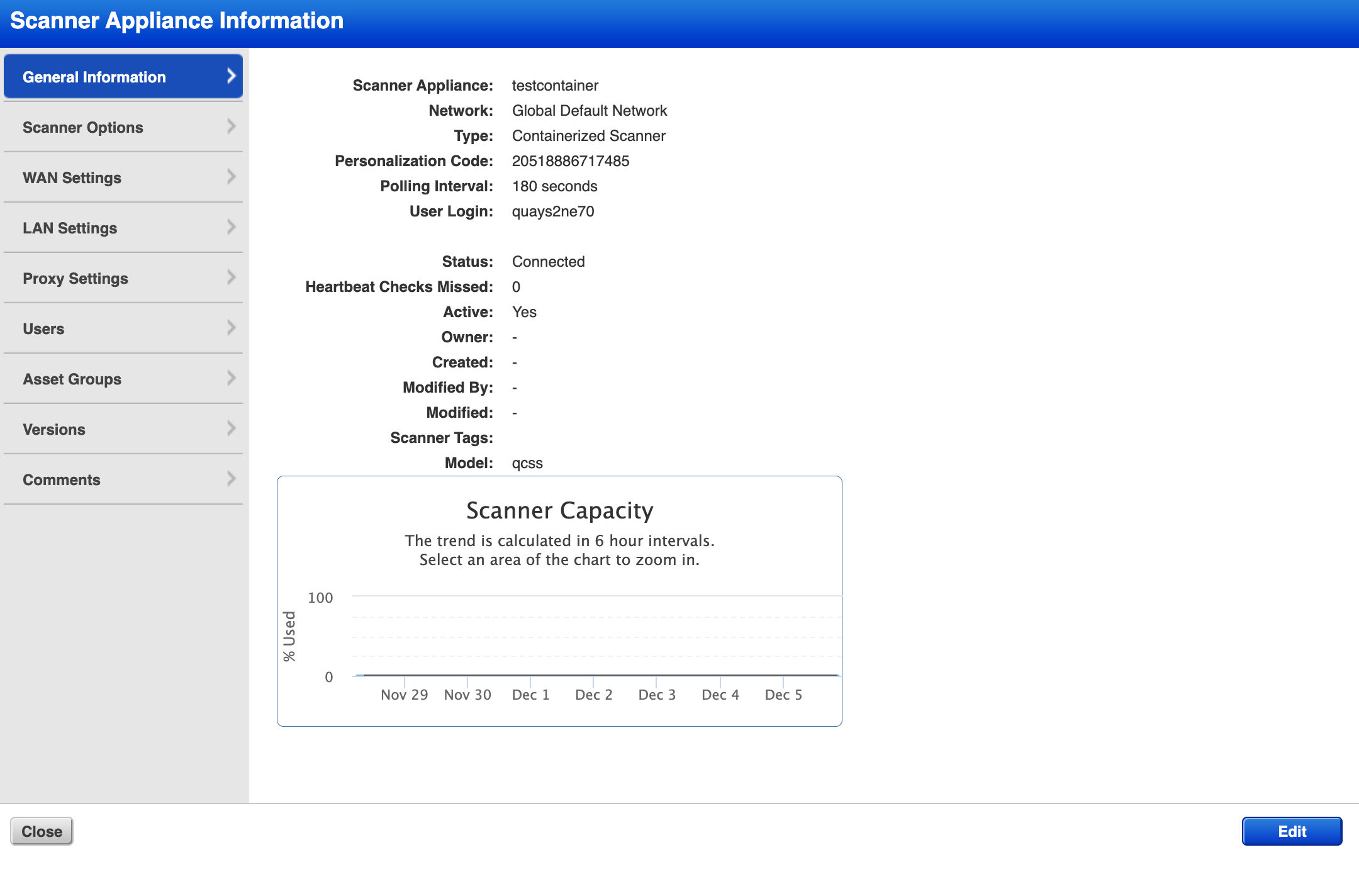
Recommended Option Profile
Qualys has introduced significant improvements to our Option Profiles and the default settings that are applied when creating new option profiles; this will align the default settings applied to option profiles with those that are recommended by the Qualys Security Solution Architects in collaboration with the VMDR Product Management team.
The “Qualys Recommended Option Profile” will increase the default TCP ports to 2,800 ports (from 1,900 – 2,800 ports); the additional set of required Ports and Services will be discovered by the scans to ensure that the Standard Ports are adopted during the vulnerability scans.
The changes that will be made include:
- Extending “Additional TCP Ports” from 12,500 to 20,500
- Purge old host data when the OS is changed
During the scans, if we observe the Operating System (OS) vendor is changed in the latest scan, then we will purge the earlier reported vulnerability findings and retain the vulnerability findings for the recent OS vendor. - Authentication Records
Based on the recent mandates by the PCI DSS v4.0—Requirement 11.3.1.2, it recommends performing internal vulnerability scans with authentication where possible. This helps customers reduce false negatives and false positives. Therefore, we will now enable Windows and Unix by default when creating an option profile. - Dissolvable Agent
Many customers have used the Qualys dissolvable agent for many years to help minimize duplicates and allow successful scans of Windows assets. This is also required in environments where remote registry service is disabled. - Asset Discovery Changes
We will be disabling ICMP as a discovery method by default while enabling the option ‘Ignore Firewall Generated TCP-RST and TCP SYN-ACK Packets’.
Changing these settings will help reduce the noise generated when the Qualys scans run their asset discovery scans.
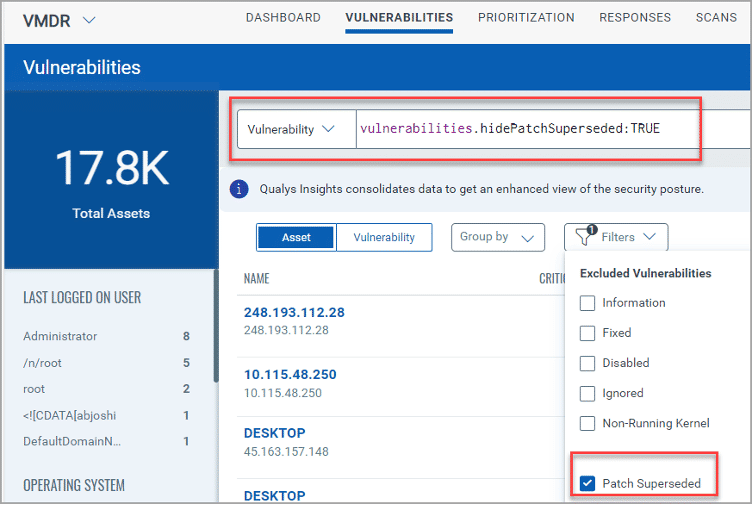
Patch Supersedence in the VMDR
With the Patch Supersedence feature, vulnerabilities addressed by obsolete patches are replaced by those remediated with newer patches. This streamlines the view, providing a more manageable set of vulnerabilities to address.
For example – If QID 2 is patched on a given target host and fixes any instances of QID 1 on the same target host, then QID 2 supersedes QID 1.
When you use the Patch Supersedence token, the vulnerabilities found on the host are analyzed. The token results include the QIDs that are flagged on hosts and not if the patches are installed or missing on the host.
The Patch Superseded filter is also available for widgets in the VMDR Dashboard. The filter is available for only the Vulnerability Management application.
Endless vulnerability patch cycles can be avoided, thus saving time in patching multiple vulnerabilities individually.
The Patch Supersedense is limited to Microsoft, Oracle Java, and Apple MAC vulnerability detections.
Qualys VMDR for ITSM
Based on ServiceNow’s recommendations, the Qualys team has redesigned the Qualys VMDR apps — the “Qualys Core” and “Qualys VMDR App.” These apps are certified and are now available in the ServiceNow Store. They are fully compatible with the latest store versions, including Xanadu, Washington DC, and Vancouver. Included at no additional cost with the Qualys VMDR package, the Qualys Core & VMDR App enables customers to transition from manual vulnerability reporting via Excel or PDF to more effective remediation tracking and measurement.

As part of the redesigned version of the apps, we are transitioning from custom tables to the ITSM-Incident Management tables. This change will allow us to create individual vulnerability tickets and group them effectively within the VMDR app.
For existing customers using the earlier version of the apps (Utha/Vancouver), TAMs/Support will provide a migration script and detailed instructions to ensure a smooth transfer of existing VMDR tasks to the ITSM-Incident table.
Below are benefits that customers can leverage by integrating with these apps:
- Automating Manual Tasks: Streamline vulnerability ticket creation using the ITSM incident table and reduce errors.
- Prioritizing with Precision: Using Qualys TruRisk attributes to focus on the most critical vulnerabilities.
- Improving Collaboration: Connecting Security and IT operations for better teamwork and transparency.
- The VMDR App, paired with CMDB Sync, leverages CI matches to map vulnerabilities accurately to corresponding assets, achieving close to a 100% match rate.
- Simplifying Patching Workflows: Integrating automated change requests and patch deployments.
Refer to the below-mentioned materials to learn more about the apps:
- Qualys VMDR & Core Apps Revamped – Blog Post
- Qualys VMDR for ITSM Redesigned – Video Series
- Qualys VMDR for ITSM – User Guide
- VMDR with ServiceNow Solution Brief
Qualys VMDR Dashboard Updates
The Qualys VMDR Dashboard provides a centralized, real-time view of your organization’s vulnerability management posture. It offers users a comprehensive, intuitive interface to monitor and manage vulnerabilities across their IT environment.
The dashboard highlights high-risk vulnerabilities and provides insights into the potential impact on your business on various parameters, allowing teams to prioritize remediation efforts based on actual business risk.
Key Benefits of Using the Qualys VMDR Dashboard
- Real-Time Vulnerability Insights: The dashboard displays up-to-date information on vulnerabilities, TruRisk Score, Asset Tags, and exposure, helping teams to respond effectively and quickly.
- Customizable Widgets: The dashboard offers customizable widgets that allow you to create a personalized view of your organizations risk posture, trends, and performance metrics, making it easier to focus on what’s most important.
- MITRE ATT&CK Prioritization: Leverage the MITRE ATT&CK Matrix framework to refine your prioritization strategy further.
- Interactive Filters: Users can filter vulnerabilities by criteria using QQLs/Tokens such as severity, asset tags, CVE, Vulnerabilities, enabling more focused analysis and response.
- Compliance Assurance: Helps organizations comply with industry standards by offering visibility into vulnerabilities that may impact their compliance posture. This ensures a proactive approach to maintaining security posture while meeting regulatory requirements.
Steps to TruRisk Dashboard
Knowing your inventory is key for any vulnerability management process. It sets the stage for you to determine the most risky vulnerabilities further and actively prioritize these among your remediation owners.
The Steps to the TruRisk Dashboard helps customers identify their crown jewel assets and classify them with an accurate Asset Criticality Score.
- Step 1 – Mind the Gap: Shift to Priority-Driven Strategies
- Step 2 – Take Inventory: Measuring Threats Accurate
- Step 3 – Get Started: Identifying and Prioritizing Business-Critical Assets
- Step 4 – Track Progress: Monitor and Quantify Risk Over Time
- Step 5 – Communicate and Eliminate Risk Reduction Tactics
The Steps to TruRisk Dashboard is available – Download the JSON file and to Manage, Communicate and Eliminate Cyber Risks.
VMDR TruRisk Dashboard
The VMDR TruRisk Dashboard enables a shift from traditional vulnerability management to risk-based prioritization, aligning technical efforts with business objectives. By focusing on the core pillars of measurement, communication, and elimination, teams can reduce risk effectively and demonstrate their value to key stakeholders.
This dashboard helps customers Drive Risk Reduction with Qualys TruRisk by shifting to a priority-driven strategy, identifying business-critical assets, tracking progress through regular validation and verification of risk assessments, and eliminating risk from the environment.
Key Benefits
- VMDR with TruRisk is ready to provide a practical, business-oriented pathway to risk-based prioritization.
- Tailor your strategy with traditional scoring, real-time threat indicators, detection age, and attack surface insights.
- To know your Low/Medium CVSS with High Critical TruRisk and to prioritize with your remediation owners.
- Gain insights into tracking vulnerabilities, CISA KEV, and risk factors, and compare CVSS vs. QDS, providing real-time risk tracking and recalculation as assets check in.
The Qualys VMDR TruRisk Dashboard is available – Download the JSON file and Prioritize the risk and not just vulnerabilities.
Subscription Health Dashboard
Optimize your security operations! The enhanced Subscription Health Dashboard:
- Provides clear deployment insights
- Identifies misconfigurations and gaps
- See stale trends while catching access and depth issues
- Ensure full asset coverage and awareness
5 Steps – Use Patching to De-Risk Your Assets Dashboard
The Subscription Health Dashboard is available – Download the JSON file and take actions
Stay five steps ahead of cyber risk! The 5-Steps Remediation Dashboard empowers you to: The 5-Steps Remediation Dashboard empowers you to:
- Step 1 – Unlock the Power of Automation: Automation speeds up the fixing of non-critical third-party apps,
- Step 2 – Elevate Your Microsoft Patching Process: Address Microsoft vulnerabilities faster
- Step 3 – Unmasking the Unpatchable: Address complex vulnerabilities by adjusting configurations or blending patches with configuration
- Step 4 – Overcoming the Challenge of Server-Side Application Patching: Server-side applications, critical to business operations, pose unique patching challenges
- Step 5 – Taking Control of Mac Security: A proactive stance on Mac security and the effectiveness of patching solutions in mitigating these risks are essential.
The 5 Steps – Use Patching to De-Risk Your Assets Dashboard is available – Download the JSON file and transform your vulnerability management.
VMDR API Updates/Changes
Introduced API Versioning Standards
APIs serve as the backbone of modern software ecosystems, enabling diverse applications to interact with each other and share data seamlessly. However, as platforms evolve, managing changes without disrupting existing systems becomes a challenge.
API versioning is our strategic response to this challenge, offering substantial benefits:
- Backward compatibility where existing integrations will continue to operate without any interruptions, ensuring operational continuity.
- Clear updates on new features and improvements are introduced in a controlled, transparent, and predictable way.
- Choice and flexibility to choose which API version best fits the customer’s operational needs and compatibility requirements.
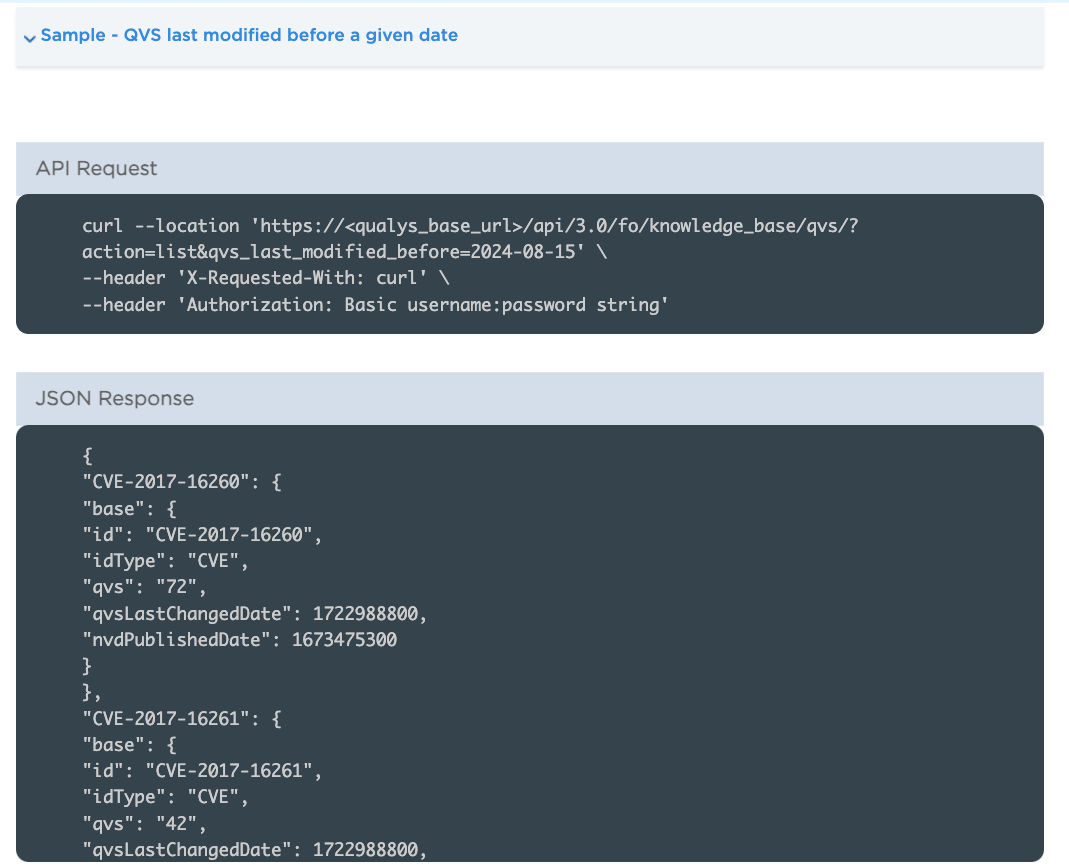
KB API – QVS Endpoint Retrieve the Last 15 Days’ CVEs
The Knowledgebase QVS endpoint has been improved; customers can now view the list of CVEs for which the QVS score was recently updated or published in the last 15 days and fetch QVS data for CVEs.
If you request a list beyond the 15-day range, you get an error. You can now access the CVEs for which the QVS is modified or updated so that you can get the latest data by using the date filter.
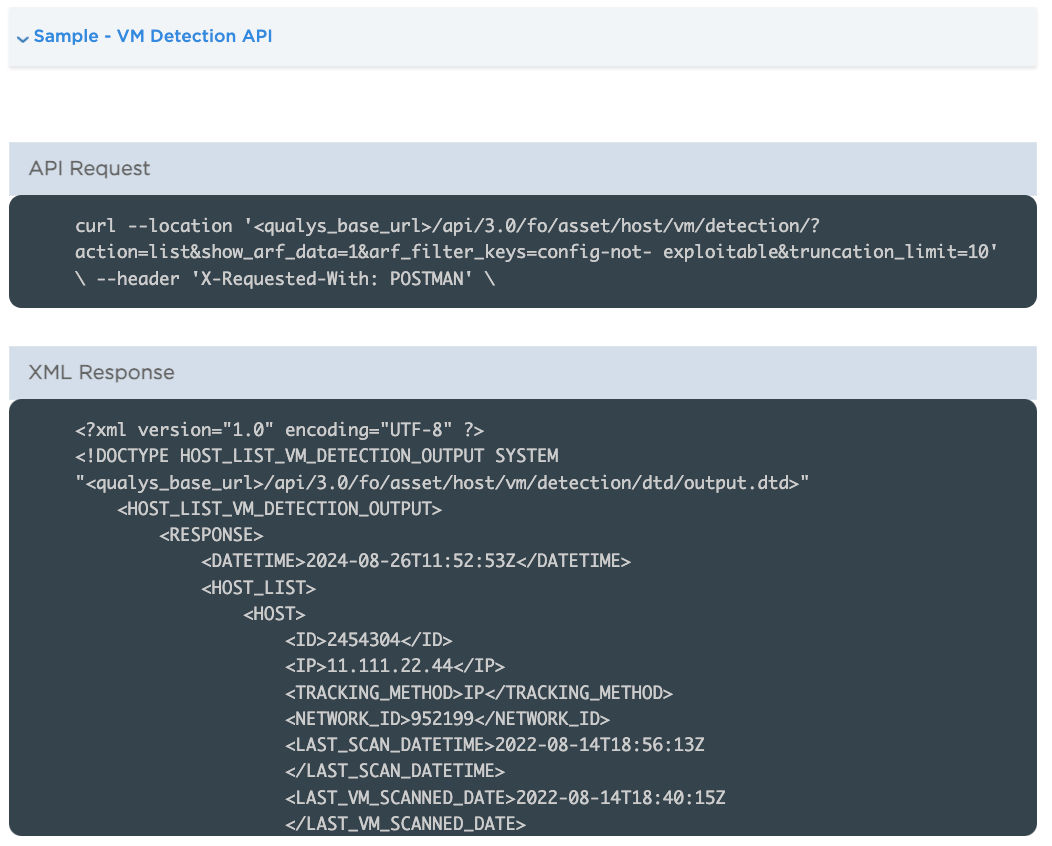
HLD API – Enhanced/Simplified ARF Filters
Simplified ARF Filters in the latest Qualys VMDR release to exclude Non-Running Kernel/Service/Not-Exploitable configuration while importing the vulnerability data using the Host List Detection API. The new design simplifies the filtering process by mapping above ARF filters with non-running kernels, non-running service, and exploitable due to configuration from report templates to API. This enhancement reduces the ARF filter configuration’s complexity, improves enterprise customers’ usability, and streamlines the filtering process.
The Earlier ARF queries were very complex for customers.
Input parameter is “arf_filter_keys=non-running-kernel,non-running-service,config-not-exploitable”
Features to Expect in 2025
Detection Sources for Vulnerabilities
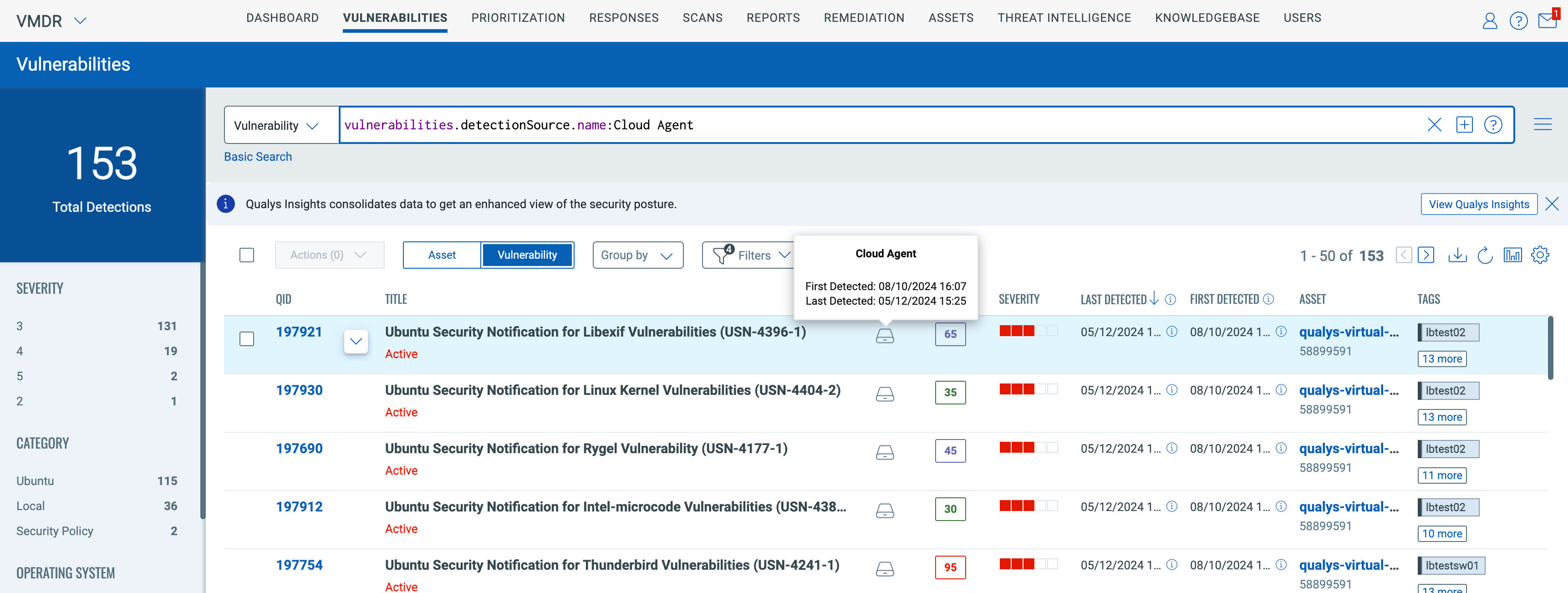
By introducing a Detection Source for each vulnerability detection, customers can distinguish the origin of vulnerabilities, such as Cloud Agent, Internal Scans, External Scans, EC2 Scan, SwCA (Software Composition Analysis), FlexScan, Cloud Perimeter, and many more.
With the VMDR package, customers can take advantage of multiple scanning sensors, including Cloud Agent, Internal Scanner, External Scanner, Cloud Connectors, TotalCloud FlexScan, and SwCA vulnerability findings. Qualys recommends using a combination of sensor methods, such as the Cloud Agent for real-time vulnerability detection and the Internal Scanner to identify remote vulnerabilities, like “Certificate Findings.” Additionally, vulnerabilities detected by an External Scanner are typically critical, and the Detection Source helps customers categorize these findings more effectively, allowing them to prioritize remediation actions accordingly.
For every vulnerability finding, the source will be available, and customers can download the “Vulnerability Detection Sources” and “Latest Vulnerability Detection Source” by using the download options from the vulnerabilities tab.
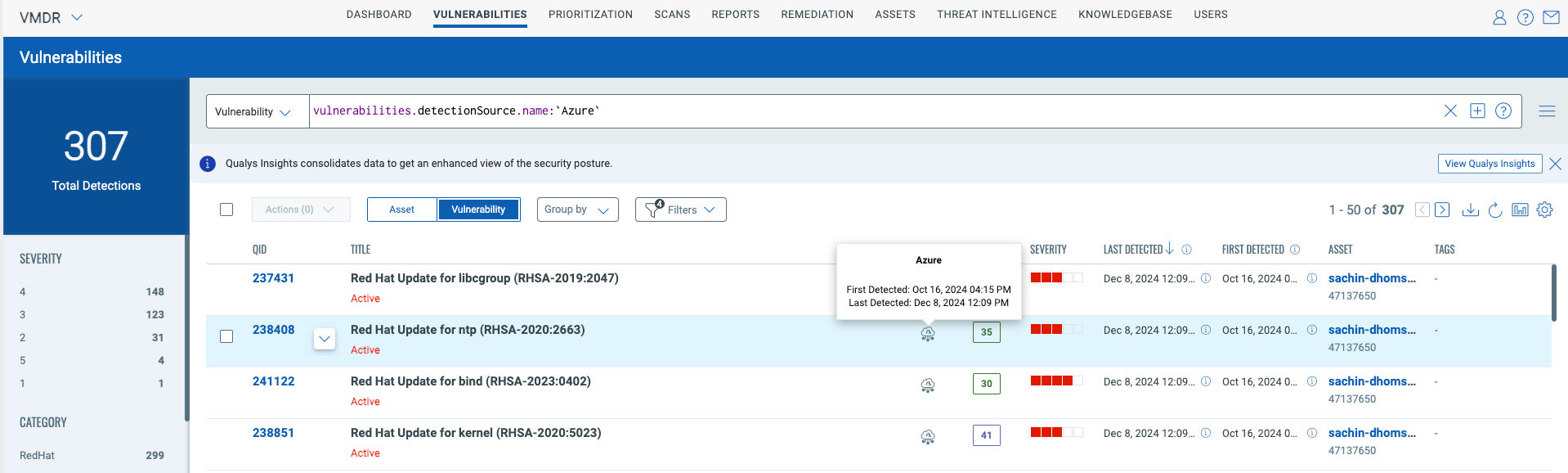
Below are a few examples for the Detection Source – Cloud Agent & Azure:
Here are the supported QQLs for the Vulnerabilities Detection Source:
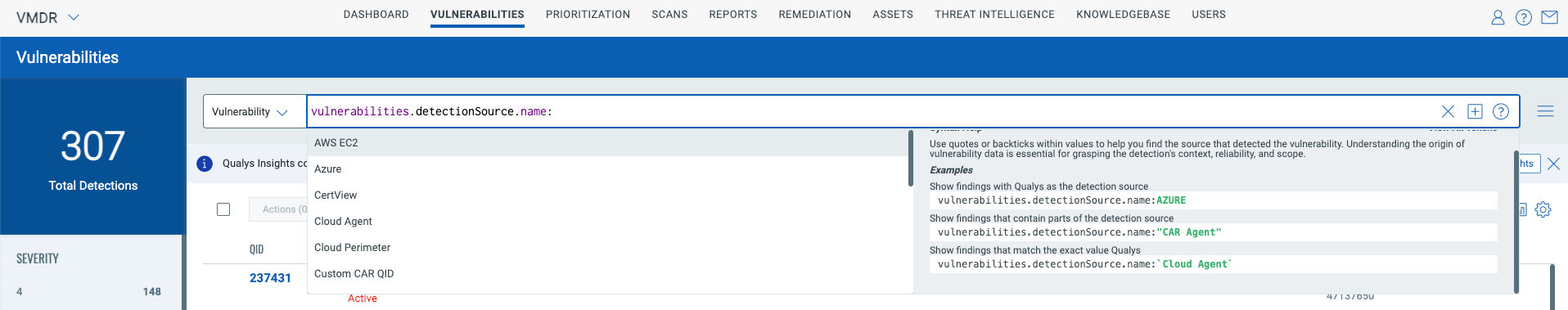
Customers can use Group by the Vulnerability Detection Source, and the same options will be supported in the Dashboard Widgets.
Azure – Instance-Based Scans” for internal assets
Customers can use the Azure Connector and launch Instance-Based Scans for their Azure Instances. Earlier, Qualys supported only perimeter scanning for Azure. Now, we are providing internal cloud support for Azure. Azure Instance-Based for internal scans can be an authenticated or unauthenticated scan. This helps you perform the internal scan on Azure for cloud assets based on location or virtual network.

Customers can scan the Azure Internal Instances and instances hosted at the Perimeter level. With the Azure Connector, you will be able to see the Instances and Resources hosted in the Cloud.
Gain end-to-end visibility of your cloud infrastructure and stay ahead in the game to detect and prioritize the vulnerabilities with the remediation owners.
IPv6 Scan Capability in VMDR
The IPv6 capability has been a topic of discussion for some time, and many enterprise customers, having exhausted their IPv4 address space, are now transitioning to IPv6. At Qualys VMDR, we are actively supporting IPv6 and have already enabled it for multiple enterprise clients.
IPv6, with its 128-bit addressing scheme, offers a vastly expanded address space compared to the 32-bit IPv4 addresses, allowing for a virtually unlimited number of unique IP addresses. This scalability helps accommodate the growing number of internet-connected devices.
Our engineering team is focused on addressing the complexities of IPv6 and is working on enhancing all vulnerability management workflows, including Scans, Reports, Business Units, and API use cases. Ensuring that IPv6 operates at the same parity as IPv4 to support all relevant use cases is a priority, and this is an ongoing effort by the engineering team.
Risk Acceptance – Beta
The Qualys Engineering team is working on defining a new risk acceptance (Centralized exception management) workflow. The new workflow will include options to classify vulnerabilities based on Risk Accepted or False Positive. Customers will be able to use the standard Qualys Query Language (QQL) to classify and use the new upcoming workflows.
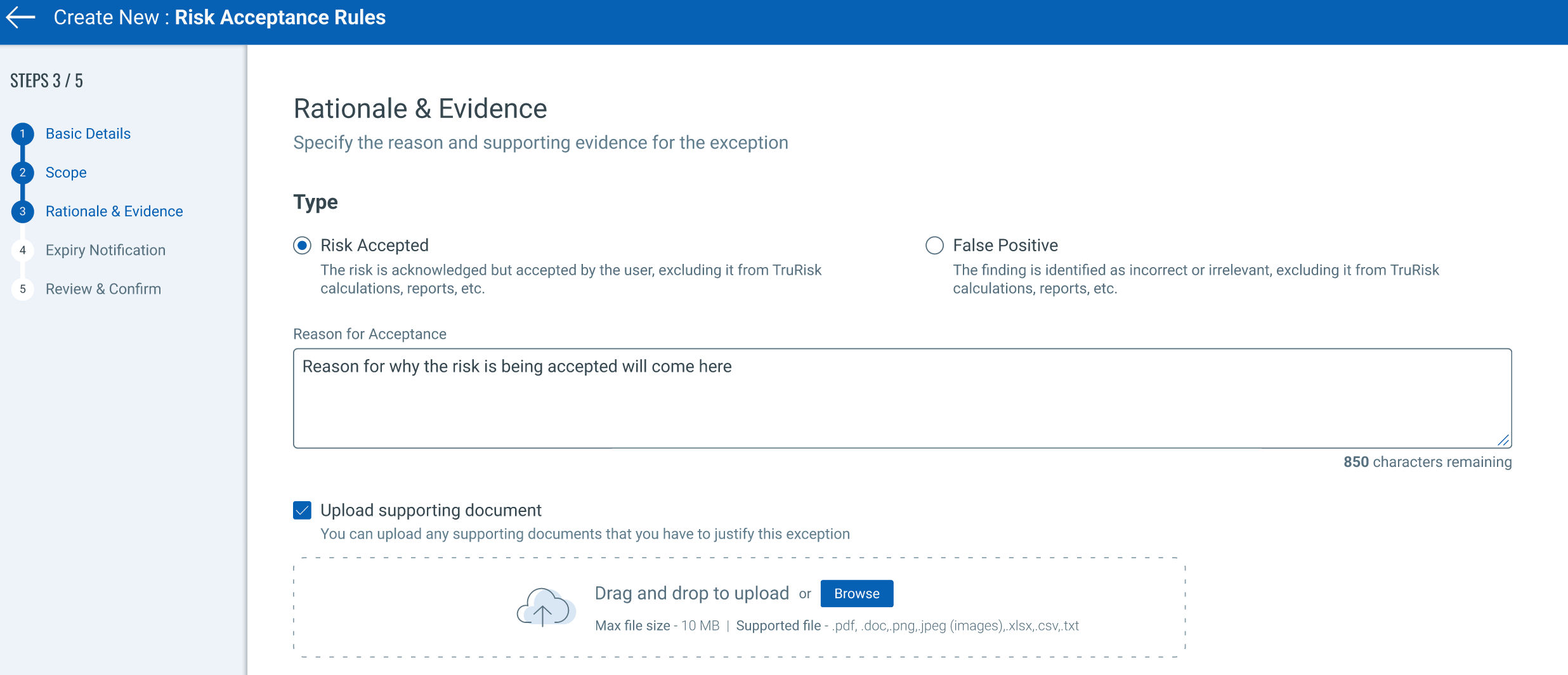
Find out more about the VMDR Product Roadmap
In closing, we’re pleased with the innovations released in 2024, and Qualys Vulnerability Management Detection & Response (VMDR) with TruRiskTM has an exciting roadmap for 2025.
Qualys welcomes customer engagement. If you are curious about the roadmap or would like to share ideas for improvements, please contact your Technical Account Manager to schedule a call.
If you are not a customer but want to learn more about Qualys Vulnerability Management Detection & Response (VMDR), check out this product description and consider a 30-day trial to learn more.
For additional references, please refer to the following VMDR Release Notes:

Leave a Reply