| Category | Details |
|---|---|
| Threat Actors | UAC-0099 hacking collective. |
| Campaign Overview | Cyber-espionage campaigns targeting Ukrainian government agencies since 2022; latest activity observed in Nov-Dec 2024 using phishing attacks and LONEPAGE malware. |
| Target Regions (Victims) | Ukrainian public sector organizations (forestry departments, forensic institutions, factories, etc.). |
| Methodology | Phishing emails with malicious attachments (double archives with LNK/HTA files), exploiting WinRAR vulnerability (CVE-2023-38831), LONEPAGE malware distribution. |
| Product Targeted | Government agency systems in Ukraine, WinRAR software (via vulnerability exploitation). |
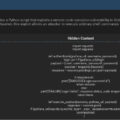
| Malware Reference | LONEPAGE malware (executes malicious PowerShell commands, transmits stolen data via HTTP POST requests, uses 3DES-encrypted files and .NET applications for execution). |
| Tools Used | Phishing emails, LONEPAGE malware, Cloudflare services, WinRAR exploit (CVE-2023-38831), PowerShell. |
| Vulnerabilities Exploited | WinRAR vulnerability (CVE-2023-38831). |
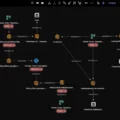
| TTPs | Phishing attachments, client-side exploitation, PowerShell-based attacks, encrypted payload execution, obfuscation of malicious activity, use of Cloudflare for infrastructure resilience. |
| Attribution | UAC-0099 group consistently targeting Ukraine for cyber-espionage; observed shifts in TTPs (e.g., changes in LONEPAGE implementation). |
| Recommendations | Enhance phishing defenses, patch WinRAR vulnerability (CVE-2023-38831), monitor PowerShell activity, apply MITRE ATT&CK Sigma rules, use tools like Uncoder AI for retrospective hunting and IOC conversion, elevate cyber vigilance. |
| Source | SOC Prime |
Read full article: https://socprime.com/blog/uac-0099-cyber-espionage-attacks-detection/
The above summary has been generated by an AI language model

Leave a Reply