Key Points
- Phishing incidents rose during the reporting period (August 1 to October 31, 2024), accounting for 46% of all customer incidents. This increase is likely driven by high employee turnover and easy access to phishing kits.
- “SocGholish” and “LummaC2” are the most frequently observed malware in customer incidents.
- Cloud services alerts increased by 20% due to rising cloud account usage, while malicious file alerts in phishing attacks remain high, exploiting users’ tendencies to open files.
- Despite a slowdown in “LockBit” ransomware activity due to law enforcement actions and a loss of affiliate trust, it remains a key player. Meanwhile, “RansomHub” is rising rapidly due to its attractive ransomware-as-a-service (RaaS) model. The US, manufacturing sector, and professional, scientific, and technical services (PSTS) sector are primary targets amidst an overall increase in ransomware attacks.
- Initial Access Broker (IAB) activity increased by 16% during the reporting period, heavily targeting US-based organizations due to perceived financial capability from cyber insurance. The proliferation of cybercrime guides on forums and a 7% rise in insider threat content, driven by significant financial incentives, highlight the growing complexity of cybersecurity challenges.
- We saw a 6% increase in impersonating domain digital risk protection alerts, highlighting the ongoing reliance on simple techniques to capture credentials and data.
ReliaQuest recently completed a thorough analysis of customer incident data and scoured cybercriminal forums to identify threat actors’ top tactics, techniques, and procedures (TTPs) from August 1 to October 31, 2024 (“the reporting period”). Using the MITRE ATT&CK framework, we’ll provide a comprehensive overview of the key cyber threats you need to know about to keep your environment protected.
Our findings highlight that cyber threats can impact any organization, no matter its size, sector, or location. Ransomware attacks, in particular, pose a significant risk, though some sectors and regions are more vulnerable than others. In this report, we’ll explore the reason behind this susceptibility, as well as notable shifts in MITRE techniques since our last analysis and key comparisons from our GreyMatter Digital Risk Protection (GreyMatter DRP) alerts.
Gain the necessary knowledge you need by reading about our insights on the most observed malware, indicators of compromise (IoCs), GreyMatter DRP alerts, the latest ransomware trends, and the hottest discussions on cybercriminal forums. We also provide practical mitigation steps to help you better anticipate and defend against the outlined threats.
Top MITRE ATT&CK Techniques
In this section, we’ll take a close look at ReliaQuest customer incidents to uncover the most common adversary tactics and techniques seen in true-positive alerts from the reporting period.
Top Techniques: A Closer Look
Phishing Techniques: The Evergreen Threat in Cybersecurity
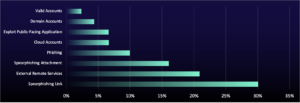
Initial access methods were the most common MITRE ATT&CK techniques between May and July 2024. Our latest investigation revealed the same trend. Spearphishing with links (T1566.002) and attachments (T1566.001) remained among the top three techniques, featuring in a combined 46% of true-positive incidents during the current reporting period—a 16% increase from our last investigation. Month after month, cybercriminals turn to phishing for initial access because it’s simple, effective, and reliable. Unsurprisingly, threat actors prefer to “work smart, not hard” to achieve their goals. In addition, phishing kits that are readily available on cybercriminal forums enable even less sophisticated hackers to infiltrate systems successfully. It’s realistically possible that the rise in phishing attacks during the current reporting period stems from the time of year. Cybercriminals might be looking to capitalize on the start of the new academic year, which brings high employee turnover and a busy period for sectors like hospitality and retail trade.
Even if employees are properly trained to recognize the signs of phishing, the constant influx of untrained new hires creates opportunities for cybercriminals. Phishing often serves as the gateway to cyber attacks, opening the door to impactful follow-on activity like malware and ransomware deployment or access to internal networks, ultimately causing substantial financial losses. Despite the importance of employee training, sometimes it just isn’t enough. As attacks evolve and become more sophisticated, tools like GreyMatter Phishing Analyzer add an extra layer of security by boosting defenses. By automatically validating and managing an organization’s abuse mailbox, you can significantly reduce the likelihood of being caught out by a phishing attempt.
In late October 2024, ReliaQuest responded to a customer incident involving a phishing attack that impersonated the customer organization’s CEO. The email was flagged by GreyMatter’s “Allowed Phishing Email” rule, designed to catch phishing attempts that evade initial security measures. During our investigation, we identified related incidents, pinpointed the source IP address and location, and found a phishing email with a malicious PDF attachment. Despite already having security measures in place, we recommended the customer refine their filtering rules to better detect and block similar attempts in the future.
This incident shows that while security tools are essential, phishing emails can still slip through. This underscores the importance of having additional compensating controls and educating employees on the risks associated with phishing and other social engineering attacks. Acting swiftly in these situations is also key to preventing further attacks such as business email compromise (BEC) or internal phishing attacks, which are harder to detect.
Remote Service Exploitation a Growing Threat in the Hybrid Work Era
Targeting vulnerable external remote services (T1133) remains a significant threat, ranking second following a 12% rise from July. While the exact reasons behind this recent increase are unclear, adversaries increasingly taking advantage of the widespread shift to remote working and the growing use of remote service tools likely contribute to the trend. These tools include virtual private networks (VPNs) and Remote Desktop Protocol (RDP), and are popular for their cost-effectiveness, user-friendly interfaces, and integration capabilities. As remote work becomes more common—with over 32 million Americans projected to work remotely by 2025 and 16% of companies already fully remote — this threat is expected to intensify. Another likely explanation is the rise in VPN vulnerabilities, as highlighted by the Cybersecurity Infrastructure Security Agency (CISA), meaning more opportunities of attack for threat actors to exploit.
However, increased use of remote service solutions also means increased numbers of weak or default credentials, granting attackers easy access. Moreover, RDP ports are often exposed to the internet, which allows threat actors to easily scan for open ports and launch brute-force attacks. To enhance security, organizations should block direct internet access to RDP services using firewalls and restrict access to internal networks and VPNs. Implementing strong password policies, enabling Network Level Authentication (NLA), and configuring rate limiting can significantly reduce the risk of unauthorized access. Additionally, deploying monitoring tools to detect suspicious activity and enforcing account lockout policies after multiple failed login attempts can thwart brute-force attacks and improve response times.
Public-Facing Application Abuse: What Goes Up Must Come Down
While many techniques are on the rise, exploiting public-facing applications (T1190) dropped by 45% compared to the previous reporting period. This could be due to natural fluctuations, but it’s also realistically possible that even more threat actors are turning to simpler methods like phishing (reflecting the increase observed in phishing attacks). Our internal data also shows a 12% decrease in mentions of Common Vulnerabilities and Exposures (CVEs), implying there are fewer mentions of vulnerabilities across sources like cybercriminal forums.
Exploiting public-facing applications has a more significant impact on sectors with highly accessible, customer-facing websites, such as retail trade, finance, health care, manufacturing, and professional, scientific, and technical services (PSTS). Such abuse can lead to data loss, unauthorized access to critical systems, and ultimately operational disruptions. Organizations with limited cybersecurity budgets or outdated legacy and end-of-life systems are prime targets for threat actors. Enterprises should prioritize patching software and adopt a risk-based approach, focusing on vulnerabilities with the greatest potential impact.
Top Sub-Techniques to Watch
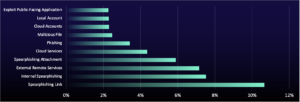
Cloud Services Alerts Up 20%
During the current reporting period, alerts for cloud services (T1021.007) rose by 20%, while the prevalence of malicious file (T1204.002) and email hiding rules (T1564.008) decreased, with email hiding rules even dropping out of the top ten. This increase is likely linked to the growing use of cloud accounts and may increase further with global spending on cloud services projected to reach $805 billion, according to the International Data Corporation (IDC) WorldWide Software and Public Cloud Services Spending Guide.
Attackers exploiting cloud accounts pose significant risks, targeting virtual machines (VMs) for activities like cryptocurrency mining, leading to unexpected costs for organizations. Compromised cloud storage can result in account breaches, data theft, or extortion in which attackers exploit reputational damage to demand ransoms. Once inside the accounts, attackers can escalate privileges, move laterally within the cloud, and exploit APIs to expand control. Email services, such as Simple Email Service (SES), can be hijacked to send convincing phishing emails disguised as legitimate company communications, damaging relationships with third parties and customers. High-privileged accounts enhance attackers’ ability to access unauthorized data, potentially causing data breaches and operational disruptions.
Organizations should ensure that cloud management is performed with isolated cloud-only accounts. Organizations should also implement the priniciple of least privielge (PoLP) to restrict user access to only necessary data, resources, and applications.
Malicious Files Gain Ground in Phishing Attacks
Malicious files remain in the top ten, with a significant increase in activity. Threat actors favor this technique for its simplicity and high success rate, exploiting the tendency among users to open files, which triggers the execution of malicious code. Often coming after a spearphishing attack, malicious links are increasingly being incorporated into phishing emails. The increase in these malicious file alerts is likely due to heightened online presence and phishing activity during this period, driven by online shopping trends.
Malicious files can prompt users to enable maliciously embedded macros, install malware like infostealers, or deploy malicious droppers. For organizations, this can result in account compromise, data loss, data breaches, and operational disruption. Organizations should implement attack surface reduction (ASR) rules to limit entry points for attackers by restricting user permissions and network access to only what’s necessary and segmenting networks to contain potential breaches. Additionally, application control can block suspicious executables, and user training can raise employee awareness of phishing techniques.
In the Spotlight: Top Malware

To identify the top malware variants affecting our customers, we analyzed a wide range of true-positive incidents that involved extortion, espionage, custom malware, hands-on-keyboard operations, and common threats.
Continuing the trend from our previous report in the series, “SocGholish” (aka “FakeUpdates”) and “LummaC2” (which we explore further below) remain the two most frequently observed malware in critical customer incidents. SocGholish once again came out on top, appearing in 18% of cases. It maintains its dominance by posing as a fake browser update, targeting high-ranking websites to appear legitimate and ultimately increasing download success rates. This persistence highlights its enduring effectiveness and success, emphasizing the need for organizations to be vigilant and implement effective defenses against the risks that it poses.
LummaC2’s Impact Spans Continents and Industries
LummaC2, also known as “Lumma Stealer,” is a sophisticated infostealer written in C, available to threat actors through malware-as-a-service (MaaS)—a business model where malware developers sell access to malware to other cybercriminals. LummaC2 appeared in 14% of all customer incidents during the current reporting period, an increase from the previous reporting period. This is likely linked to a new tactic used by the malware that was first observed in late August 2024. The new tactic involves obfuscating PowerShell, which downloads and executes payloads using living-off-the-land binaries (LOLbins) such as mshta.exe and Dllhost.exe.[i] There are many other reasons why threat actors continue to utilize LummaC2, including its regular updates, vendor support, simplicity for even less skilled threat actors, high success rate of system infiltration, and ability to exfiltrate sensitive data undetected.
In August 2024, we responded to an alert triggered by a rule designed to detect suspicious lateral movement within customer networks. The alert was activated after an attempt to communicate with the LummaC2 Stealer Command and Control Traffic Detection signature was detected. This detection blocked all communication between the internal and destination IP addresses, allowing our teams to recommend response actions such as conducting endpoint forensic analysis using the IP address to ensure no signs of compromise or malware. This proactive defense effectively prevented LummaC2 from infiltrating the customer’s system and extracting credentials. Organizations must stay informed about threats most relevant to them, and implementing detections like the one in this case study is crucial to effectively stopping and mitigating threats.
LummaC2 commonly propagates via cracked or counterfeit versions of popular software and is distributed through phishing emails containing attachments or links that impersonate reputable companies. It also has other rare methods of distribution such as fake updates, where the targeted individual visits a website that contains JavaScript code to redirect to a browser update page. This makes LummaC2 more likely to successfully bypass standard security measures.
No sector is safe from LummaC2, which casts a wide net across industries such as basic resources, construction, food and beverage, health care, industrial goods, media, and technology. Its global reach is just as extensive, impacting regions including the US, UK, Ecuador, Nigeria, and Japan. LummaC2 targets diverse sectors and organizations, driven by the profit from selling stolen credentials on cybercriminal forums, Telegram channels, and marketplaces like Russian Market. Following the takedowns of popular infostealers “RedLine” and “Meta” in October 2024, it’s anticipated that those who relied on these tools may shift to other variants, including LummaC2, to continue their operations.
How You Can Defend Against LummaC2
Understanding the threat landscape and staying informed about the most widely used infostealers can help organizations pinpoint the biggest risks to their operations. To protect against LummaC2, we recommend several key actions. For instance, disable password-saving in web browsers via Group Policy Management to prevent credential theft. Encourage employees to avoid using personal devices for work, as these often lack robust security measures. If compromised credentials are detected, promptly initiate password changes and add inactive accounts to a denylist to thwart spearphishing attempts.
Top GreyMatter DRP Alerts
ReliaQuest’s GreyMatter DRP helps organizations identify, monitor, and mitigate online threats by safeguarding their digital assets, brand reputation, and sensitive information from cyber risks across the internet. GreyMatter DRP generates alerts that are categorized by risk type and provides context that can allow organizations to take proactive remediation responses. This helps security teams make informed decisions on potential threats to their environments.
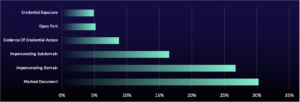
Alert Landscape Shifts: Exposed Credentials Down, Impersonating Domains Up
The proportion of exposed credential alerts decreased by 19% since the previous reporting period. This is likely from a recalibration in the method used to classify and quantify GreyMatter DRP alerts for more accurate reporting, rather than an actual real-world decrease in credential targeting. Nevertheless, it’s realistically possible that the takedown of RedLine and Meta stealers in late October 2024 may have contributed to a reduction in stolen credentials, particularly as RedLine was the second most prevalent infostealer that we identified in 2023, with a 44% rise in listings from Q3 to Q4 2023. Exposed credentials can have detrimental impacts, leading to unauthorized access to systems, internal phishing attacks, and lateral movement and persistence.
Slight Rise of Impersonating Domains—Continuing to Dominate GreyMatter DRP Alerts
Impersonating Domain alerts are still the second most common alert type, with a 6% increase since the last reporting period. Threat actors likely continue to favor this technique due to its simplicity and effectiveness in capturing credentials and data by tricking users into entering information or downloading malware through deceptive links.
We observed hundreds of domains mimicking hurricane relief sites during Hurricane Milton and Hurricane Helene in September and October 2024. This demonstrates how threat actors are willing to exploit even the most sensitive of events for malicious purposes. For example, on September 27, 2024, we observed roughly 50 impersonating domains related to Hurricane Helene, such as hurricaneheleneadjuster[.]com and hurricaneheleneclaimhelp[.]com. This activity is also common during events like Black Friday, where adversaries create fake domains to trick users and employees into logging into accounts on fake websites or downloading malware, leading to further attacks.
Recommendations
Organizations should adopt digital risk protection (DRP) solutions like GreyMatter DRP to monitor for exposed credentials and impersonating domains, alerting them for quick remediation. Additionally, securing internal documents with encrypted storage and using safe file-sharing platforms is crucial, especially when sharing externally. Implement strong password policies and regular rotation to prevent exploitation and enhance security with data loss prevention (DLP) and watermarking to better identify and protect sensitive documents.
Inside Look at Dark Web Activities
In this section, we’ll take a deep dive into the rise in initial access broker (IAB) activity on cybercriminal forums, the proliferation of freely shared and sold guides and manuals for conducting various cybercrimes, and the growing threat of insider activity.
IABs Boost Activity by 16%
IABs are financially motivated threat actors who are highly active on cybercriminal forums, consistently advertising access to corporate networks. The prominent Russian-language forum XSS, for instance, has a dedicated section that’s updated daily with new listings targeting various sectors and regions.
While listings from the reporting period span the globe, US-based organizations are disproportionately targeted, with 55% of all observed IAB listings offering access to unnamed US-based entities. This is likely because threat actors perceive US-based organizations to be more financially capable of paying ransoms due to well-developed cyber insurance. Regions with higher adoption of cyber insurance are more attractive targets, as threat actors assume these organizations are more likely to pay to maintain operations.
During the reporting period, our collection of IAB posts increased by 16%. This increase in activity on cybercriminal forums is likely driven by two main factors: the emergence of more threat groups in the ransomware landscape and the growing number of threat actors entering the ransomware affiliate market, and the increased use of infostealers, which IABs typically use to obtain accesses to organizations.
Given the indiscriminate approach commonly taken by IABs, organizations across all sectors and locations should remain vigilant. The threat they pose shouldn’t be underestimated, as IABs aim to quickly sell accesses to compromised systems before the targeted organization realizes its information is for sale. In addition, IABs often use their accesses to facilitate ransomware attacks—arguably the biggest threat in 2024—inflicting severe financial damage and harming an organization’s reputation.
Implementing robust DRP measures and keeping assets updated is essential for receiving alerts if your organization is mentioned on a cybercriminal forum. Organizations should also monitor for suspicious activity, especially among users with elevated privileges and access to sensitive systems. This proactive approach helps mitigate potential threats and safeguard critical corporate data. For more comprehensive protection, we also recommend implementing privileged access management (PAM) solutions to categorize sensitive data and restrict exfiltration of sensitive data if an access is purchased by a ransomware group. These measures can prevent threat actors from exploiting stolen credentials and help avoid further damage to the organization.
Cybercrime 101: Manuals and Guides Now Available on the Dark Web
We’ve recently seen a growing trend on cybercriminal forums where manuals and guides for various cyber attacks are being shared more frequently. This rise is largely driven by financially motivated threat actors looking to maximize their profits. For example, the number of shared guides on the prominent English-language forum BreachForums jumped from 106 to 115 in the reporting period.
On October 18, 2024, a user on XSS advertised an “Advanced Office 365 Tutorial” for BEC. This guide offered tools and resources to enhance phishing and social engineering techniques, with price tiers of $500, $1,200, and $2,000, suggesting varying levels of detail. Although the specific content of each tier is unclear, testimonials highlight the guide’s effectiveness, with the guide even providing step-by-step instructions for less skilled threat actors.
The proliferation of these guides enables more individuals to enter the cybercrime arena. While the guides themselves aren’t a direct threat, their availability—sometimes shared freely for anyone to download—can lead to an uptick in cyber attacks. To counter this, organizations should continually educate themselves on emerging trends and forum discussions around techniques. Staying informed allows for proactive adjustments to defenses, helping to better anticipate potential threats.
Beware: Insider Threats Intensify
In September 2024, a ReliaQuest customer faced an insider threat incident. Our Threat Intelligence team engaged with the insider to gain insights into the incident, uncovering the threat actor’s financially motivated objectives. By leveraging our expertise in interacting with threat actors, we gained valuable insights into their intentions.
While insider threat monitoring can be done manually, tools like GreyMatter DRP can automate the process, improving the speed and effectiveness of threat detection. In addition, our threat intelligence capabilities provide customers with unique insights through direct engagement with threat actors, helping organizations better understand the threat landscape. This intelligence supports informed decision-making and helps prevent similar future incidents. A key lesson learned from this incident is the importance of proactive threat intelligence and engagement, which can significantly enhance an organization’s ability to anticipate and mitigate insider threats.
While insider threats are not new, we identified a 7% rise in insider activity and requests for insiders compared to the previous reporting period. On BreachForums, a user offered up to $10,000 per week for insiders with access to systems at major US mobile carriers like Verizon, AT&T, and T-Mobile, indicating the potential for significant profits. Although their exact intentions are unclear, other threads mention services like SIM swaps and eSIM generation. Cybercriminals typically use SIM swapping to steal phone numbers by tricking mobile carriers into transferring them to different SIMs. This grants attackers access to different phones and allows them to intercept calls, SMS messages, and voicemails, which are often used to send one-time passwords (OTP) for accessing financial and other accounts.
As BreachForums’s reputation grows, more insiders are surfacing. Though the exact reason behind this is unclear, it could be fueled by revenge after job loss or financial motivation. Insiders can severely impact organizations by leaking documents, secrets, and intellectual property, leading to competitive disadvantages, data loss, and financial and reputational damage.
To proactively prevent unauthorized access to data, organizations should monitor key cybercriminal forums with DRP tools to detect potential insiders and implement DLP software to help monitor user activity and identify suspicious behavior. It’s also crucial to set up data access management policies such as role-based access control (RBAC), attribute-based access control (ABAC), and discretionary access control (DAC) to limit user access to sensitive information and enforce data security policies.
Trending IoCs
Throughout the reporting period, we identified thousands of IoCs in true-positive incidents. By monitoring these attacker IoCs, ReliaQuest GreyMatter leverages threat intelligence and AI to recommend actions for triggered alerts and execute containment measures, significantly improving our customers’ MTTC.
One to Watch: Supply-Chain Attack Domains
Threat actors persisted in using new infrastructure to launch attacks, as it’s both affordable and easy to implement. New infrastructure is more likely to evade detection as it’s not related to previous campaigns, challenging businesses that depend on reputation-based blocking. To address this, shifting toward behavior-based detection and utilizing hunt packages can help identify threats that aren’t linked to known IoCs.
We continue to observe attackers exploiting older, compromised domains due to their perceived legitimacy, which helps them bypass security measures. Our analysis showed that many of these domains were linked to file-related sites. A notable shift from the previous reporting period is the emergence of supply-chain attack domains. For instance, an attack on Polyfill in July 2024 involved a popular JavaScript library domain injecting malicious code, compromising thousands of sites. An example of a domain we identified associated with such supply-chain attacks is staticfile[.]org. To combat these threats, businesses should proactively block domains that are deemed compromised in supply chain attacks and implement web-filtering solutions to monitor and control traffic to sites associated with terms like freeware or shareware, thereby strengthening their defenses.
The Rise of Deceptive PDF Converters
Executable (.exe) files made up 35% of all identified malicious files, with PDF files following at 21%. Interestingly, while PDFs are typically used by threat actors to bypass standard email security, most of the executable files we discovered were related to PDF converters, for example “FreePDFProConverterInstallationWizard.exe.” Although the exact reason for this tactic gaining traction cannot be determined, our analysis suggests that threat actors likely use executable files to deceive users because they appear as legitimate tools. This, in turn, increases the likelihood of the files being clicked and downloaded.
During the reporting period, trojans were the most downloaded through malicious executable files, which can lead to data theft, additional malware deployment, antivirus deactivation, and system crashes. As such, organizations should train users to avoid installing unverified tools to prevent malware execution.
Remaining consistent with the previous reporting period, 70% of the malicious files we observed during the current reporting period didn’t have valid signatures. This means organizations should prioritize implementing control policies and digital signature verifications that audit trails for modifications. This allows only files with valid signatures to successfully pass through, preventing those without from executing in the network.
Key IP Address Origins and Patterns
Similar to the previous period, we identified 21 IP addresses linked to customer incidents, primarily originating from the US, Russia, and the Netherlands. This ongoing trend highlights the consistent use of IP addresses from these regions by threat actors, emphasizing the importance for organizations to monitor these source locations closely. Our latest analysis confirms a persistent pattern, with IP addresses used for reconnaissance and brute-force attacks accounting for 70% of confirmed incidents. As such, organizations can confidently block these IP addresses to minimize operational disruptions.
Connections to C2 servers also remain a notable threat. Tools like Cobalt Strike, accounting for 13% of activities, and Silver C2 at 4%, are still popular among threat actors for their stealth and effectiveness. Initially designed for legitimate security testing, these tools are now increasingly repurposed for malicious purposes.
Our GreyMatter platform has a specific response playbook to effectively address malicious IP addresses. The playbook can be automated to block IP addresses across all networks upon detection of a threat. It also blocks requests from IPs previously linked to malicious activities. By blocking these IPs, threat actors are prevented from accessing targeted networks, halting any potential malicious actions. Automating response actions, for example through Automated Response Playbooks within GreyMatter, significantly improves organizations’ MTTC, ensuring rapid threat resolution and minimizing the risk of prolonged damage.
Ransomware Targeting Patterns

LockBit Activity Persists, RansomHub on the Up
We previously noted ransomware group “LockBit’s” reduced activity following a law enforcement crackdown, placing it fourth among the most active groups in the reporting period. While the operation has impacted its activity, LockBit continues to operate, albeit more slowly. This slowdown is likely due to a loss of trust among previous affiliates, prompting them to join other affiliate programs. However, LockBit’s resilience, still maintaining a strong position, is likely thanks to loyal, long-term affiliates who continue to pull off sophisticated attacks, keeping LockBit on the radar.
Despite the decrease in LockBit activity, ransomware remains a major threat, with “RansomHub” now increasing its attacks. RansomHub targeted 232 organizations during the reporting period—a 130% increase from the previous reporting period—likely due to its ransomware-as-a-service (RaaS) program attracting affiliates from disrupted groups like “ALPHV.” APLHV disbanded in late December 2023 after conducting an exit scam against its affiliates. The RansomHub affiliate program is particularly appealing, allowing affiliates to keep 90% of profits, offering significantly more than other programs.
Little Change in Victimology
As we saw in the previous reporting period, ransomware groups continue to heavily target the manufacturing and PSTS sectors. These sectors remain prime targets because they rely on continuous operations and are perceived by threat actors to be more likely to pay ransoms to avoid major financial and reputational damage. Health care and social assistance (HSA) organizations are also frequent targets, as downtime can lead to financial losses and jeopardize patient safety.
The US remains the primary target for ransomware groups, with a 22% increase in attacks since the last period. Canada follows, with 90 organizations targeted, surpassing the UK and seeing a 43% increase. Most ransomware groups have RaaS rules prohibiting attacks against the Commonwealth of Independent States (CIS). This, along with political tensions, may explain the higher number of attacks on the US. Additionally, the disproportionate number of attacks on the US is influenced by IAB activity; of 1,066 IAB listings identified across top cybercriminal forums, 584 were related to US-based organizations.
Attackers often view US enterprises as lucrative targets, believing they have the financial means to pay substantial ransoms. As discussed earlier, ransomware groups likely target organizations more inclined to take up cyber insurance, such as those in the US and Canada, likely contributing to the increased attacks on Canada. While financial gain is usually the primary aim, there might also be a nationalistic sentiment. Many ransomware operators are based in Russian-speaking regions and may focus on perceived adversaries to Russian interests. However, as seen with the recent RansomHub and “Scattered Spider” collaboration, a shift in targets as more groups potentially collaborate across geographical boundaries for more impactful attacks may be on the horizon.
Mitigations
To minimize the risk of ransomware, organizations should adopt a multi-layered defense strategy. This includes maintaining rigorous backup policies, enhancing endpoint visibility, and ensuring all software is up to date. Organizations should also implement DRP solutions like GreyMatter DRP to detect exposed credentials on cybercriminal forums and configure .JS files to open with notepad.exe instead of wscript.exe to block JavaScript execution.
Conclusion
Attackers stick with what works until it doesn’t. Trends have remained consistent between our previous and current reporting periods, suggesting that while fluctuations may occur, attacker strategies will largely stay the same. We can expect techniques like phishing to remain popular due to their simplicity and success in tricking users into executing malicious files or divulging sensitive data. However, we may see phishing evolve as large language models (LLMs) continue to develop, enabling more automated, sophisticated, and convincing attacks. While there have been minimal changes to the ransomware scene from our last report, activity is expected to continue rising, driven by emerging groups and shifts in affiliate networks.
To ensure robust cybersecurity in any threat landscape, our GreyMatter platform enhances your protection by detecting malicious activities across endpoints and existing security tools. It also offers Hunt packages to proactively identify threats. With Automated Response Playbooks, organizations can automate their response actions, ensuring immediate containment of attacks and safeguarding sensitive data while maintaining operational integrity. By staying in-the-know on the most current threats and implementing the mitigation steps outlined in this report, you can effectively manage risks and strengthen your overall security posture.



Leave a Reply