In the current cybersecurity environment, organizations face a barrage of alerts concerning suspicious activities that can quickly overwhelm their security teams. CTI Analysts must navigate this complexity while ensuring they can accurately identify genuine threats amidst false positives. This challenge is especially pronounced in industries where the stakes are high and the need for precision is critical. This is where ThreatConnect’s CAL integration with Polarity becomes a valuable asset.
integration with Polarity becomes a valuable asset.
Global, Ground-Truth Insights on Threats in the Wild
None of us is as smart as all of us. The insights an analyst gets at another company or organization can give advance warning of threats targeting you. CAL captures billions of these insights, anonymizes them, and gives you the benefit of experience gained by tens of thousands of analysts.
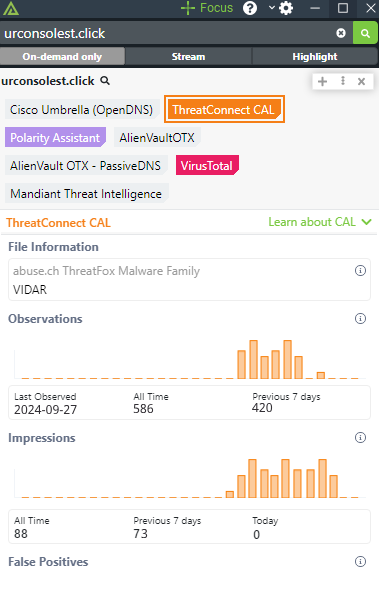
This indicator was recently reported in real SIEMs across the globe, and other analysts have looked at it in the past week. No one has identified it as a false positive. It’s probably worthy of attention!
Timely and Actionable Insights
CAL aggregates large datasets from various intelligence sources and combines them with its own analytics to uncover actionable insights relevant to the analyst’s context. The analyst can quickly identify new areas for deeper investigation, ensuring they focus on genuine threats. This capability enhances their efficiency and allows them to respond more effectively.
CAL also compiles data from hundreds of blogs, intel feeds, government bulletins, and other sources into a single dataset. All of these indicators are made machine-readable and available to analysts through Polarity.
Reducing Alert Fatigue
Alert fatigue is a common challenge in cybersecurity. CAL helps mitigate this by consolidating billions of indicators into a single score, which presents the criticality of each IoC. Using this score, analysts can rapidly assess which indicators need immediate attention and which can be deprioritized, reducing the risk of overlooking significant threats and wasting time on false positives.
CAL has identified this indicator as an active and critical threat.
AI-Based Indicator Classification
CAL uses machine learning and other techniques to automatically classify every indicator that it collects, including insights like:
- Suspicious Host Classification: Identifies hosts that have resolved to known malicious IPs or have shown suspicious activity patterns.
- Dynamic DNS and Tor Exit Node Detection: Flags indicators related to anonymization services, like dynamic DNS and Tor nodes, that are often associated with malicious behaviors.
- Cloud Infrastructure Detection: Distinguishes indicators tied to cloud service providers like AWS, Google Cloud, or Azure to identify infrastructure that might be used for hosting attacks.
- Malicious IP Resolution: Tracks indicators resolving IP addresses known for hosting malware or phishing content.
- Frequency of Resolution: Detects hosts that rapidly resolve to different IP addresses, which can be an indicator of malicious command and control (C2) infrastructures.
- Suspected DGA – The host may have been generated by a domain generation algorithm (DGA), a tactic frequently employed by malicious actors to create multiple domains to leverage during cyber attacks.
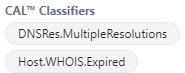
Automatic classifiers can inform whether to investigate, escalate, act, or deprioritize.
A Practical Application
Polarity customers can more quickly and efficiently identify critical threats that could have been missed without ThreatConnect’s CAL integration. CAL enables analysts to respond effectively to evolving threats by streamlining their workflow and providing essential insights. For organizations seeking to enhance their threat intelligence capabilities, ThreatConnect CAL provides efficient and informed cybersecurity operations.
CAL is available to all Polarity customers.
Want to Learn More?
For more information on CAL and Polarity, download the CAL integration solution brief. Want to learn more about Polarity by ThreatConnect? Take an interactive tour or request a demo to see how Polarity modernizes security operations.
The post ThreatConnect CAL™: New, Unique Intelligence for Polarity appeared first on ThreatConnect.


Leave a Reply