| Category | Details |
|---|---|
| Threat Actors | Unnamed actors exploiting CVE-2024-0012 and CVE-2024-9474; activity includes manual/automated scans, web shells, and C2 tools. |
| Campaign Overview | Operation Lunar Peek; targets Palo Alto Networks PAN-OS management web interfaces via authentication bypass and privilege escalation vulnerabilities. |
| Target Regions (Victims) | PAN-OS devices globally, with specific targeting of internet-exposed management web interfaces. |
| Methodology | – Exploitation of CVE-2024-0012 for admin access. – Privilege escalation through CVE-2024-9474. – Dropping obfuscated web shells and malware. |
| Product Targeted | Palo Alto Networks PAN-OS management interfaces. |
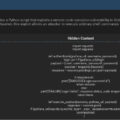
| Malware Reference | PHP web shell (SHA256: 3C5F9034C86CB1952AA5BB07B4F77CE7D8BB5CC9FE5C029A32C72ADC7E814668). |
| Tools Used | – Exploits for CVE-2024-0012 and CVE-2024-9474. – Web shells. – Open-source command-and-control (C2) tools. – Crypto miners. |
| Vulnerabilities Exploited | – CVE-2024-0012: Authentication bypass. – CVE-2024-9474: Privilege escalation vulnerability. |
| TTPs | – Scanning internet-facing devices. – Exploitation of management web interfaces. – Dropping malicious payloads. – Use of anonymous VPN services. |
| Attribution | High confidence that functional exploits are publicly available, enabling broader exploitation. |
| Recommendations | – Apply patches for CVE-2024-0012 and CVE-2024-9474. – Restrict management interface access to trusted internal IPs. – Monitor for suspicious activity. – Investigate potential compromises. |
| Source | Unit42 by Palo Alto Networks. |
Read full article: https://unit42.paloaltonetworks.com/cve-2024-0012-cve-2024-9474/
The above summary has been generated by an AI language model



Leave a Reply