We recently had the opportunity to have a chat interview with an actor going by the alias “Sukob” who operates on a well-known darknet forum – BreachForums. Sukob is an initial access broker (IAB) and malware developer loosely affiliated with the Hellcat group.
In this exclusive interview, Sukob reveals how the actor balances a seemingly ordinary IT job with a passion for hacking and delves into his associations with the enigmatic Hellcat group.
Through our conversation, Sukob sheds light on the sophisticated tools and strategies employed in modern cyberattacks, such as his innovative ShadowPOS malware and TanakaBuilder. The actor discusses the intricacies of maintaining anonymity, evading law enforcement, and the collaborative nature of cybercriminal networks. Additionally, Sukob provides a glimpse into his approach to targeting high-revenue sectors while avoiding high-risk areas that could attract intense scrutiny.
Stay Updated with Our Newsletter
Key Findings:
Motivation:
- Primarily financially motivated but has a genuine passion for hacking, willing to continue even without monetary gain.
Association with Hellcat Group:
- Loosely affiliated with the Hellcat group, contributing occasionally without deep involvement.
- Maintains friendships with group members and hints at future collaborative projects.
Development of ShadowPOS Malware:
- Created ShadowPOS to innovate beyond typical bootloader or C2 agent malware.
- Enhanced efficiency by optimizing memory scan times from hours to minutes using C++ and regular expressions.
Creation and Functionality of TanakaBuilder:
- Developed TanakaBuilder to facilitate email phishing and malware delivery through shortcut files (.lnk).
- Emphasizes fileless operations and uses techniques like “living off the land” to evade detection.
Preference for Selling Network Access Over Ransomware:
- Chooses to sell network access to avoid attracting significant law enforcement attention that ransomware operations might invite.
- Finds selling access to be a simpler and more secure method for single individuals or small groups.
Evasion Tactics During Incident Response:
- Utilizes strategies like side-loading implants into critical services to maintain persistence.
- Employs long sleep times for beacons and spreads across multiple machines, including IoT devices, to avoid detection.
Group Structure and Onboarding Practices:
- Hellcat group operates with a zero-trust, terrorist cell-like architecture to minimize exposure if a member is compromised.
- New members are vetted through trusted referrals and small, functional group sizes ensure security and operational integrity.
Targeting Strategies and Avoidance of High-Risk Sectors:
- Focuses on high-revenue targets from wealthy countries, avoiding direct attacks on governments and critical infrastructure to reduce the risk of severe legal repercussions.
- Targets sectors with significant business infrastructure, such as telecommunications and technology companies, for maximum financial gain.
The Interview
Below we have presented the questions and answers with no modification.
Question: Welcome to the Osint10x interview, Sukob! As this is our first engagement, please tell us about yourself and your work.
Sukob: I am Sukob. I am a young hacker who is primarily financially motivated as most are but I just love hacking and malware development, I would do it even if it made no money. I deal mostly in malware and initial access. Most of my sales are privately agreed upon, but I occasionally make threads (on forums).
Question: What does your day look like away from the keyboard? Like do you go for a run, surf, or yoga or do you always in the Twilight Zone?:-)
Sukob: It’s hard to answer this question without endangering yourself, but I can tell you it’s a normal day like any other. I have a job and I am a productive member of society. After enough years, you get used to living a kind of “double life” and you don’t feel that way anymore. I’ve come to terms with it and I know I can’t tell anyone about it, but it doesn’t bother me anymore, it’s completely assimilated into my life. I usually wake up in the morning before work, I prefer to conduct all the negotiations and check on the projects I’m involved in. If I need to hack something, it’s going to happen when I get home from work. I have an ordinary inconspicuous low-paying job in IT. Only immature kids will come out and show their illegal money and pretend to be gangsters, I know who I am and I try to remain professional. A glance at my life seems like an ordinary paid slave. I’m still sometimes surprised to realize that instead of regular problems like paying for rent and women, I’m plagued by internal arguments about how best to launder my money, how I’m going to fix a bug in a malware project, or what are the best decisions I should make in my OPSEC model to avoid unwanted attention from law enforcement.
Question: What’s your association with the Hellcat group and how do you contribute?
Sukob: I am loosely associated with the group. I do not want to go to the extent that I contribute. I recently collaborated on some work with them which we will maybe see in the news soon. Other than that I am just a friend of some of the members, they are trustworthy people. We do have big plans in the works.
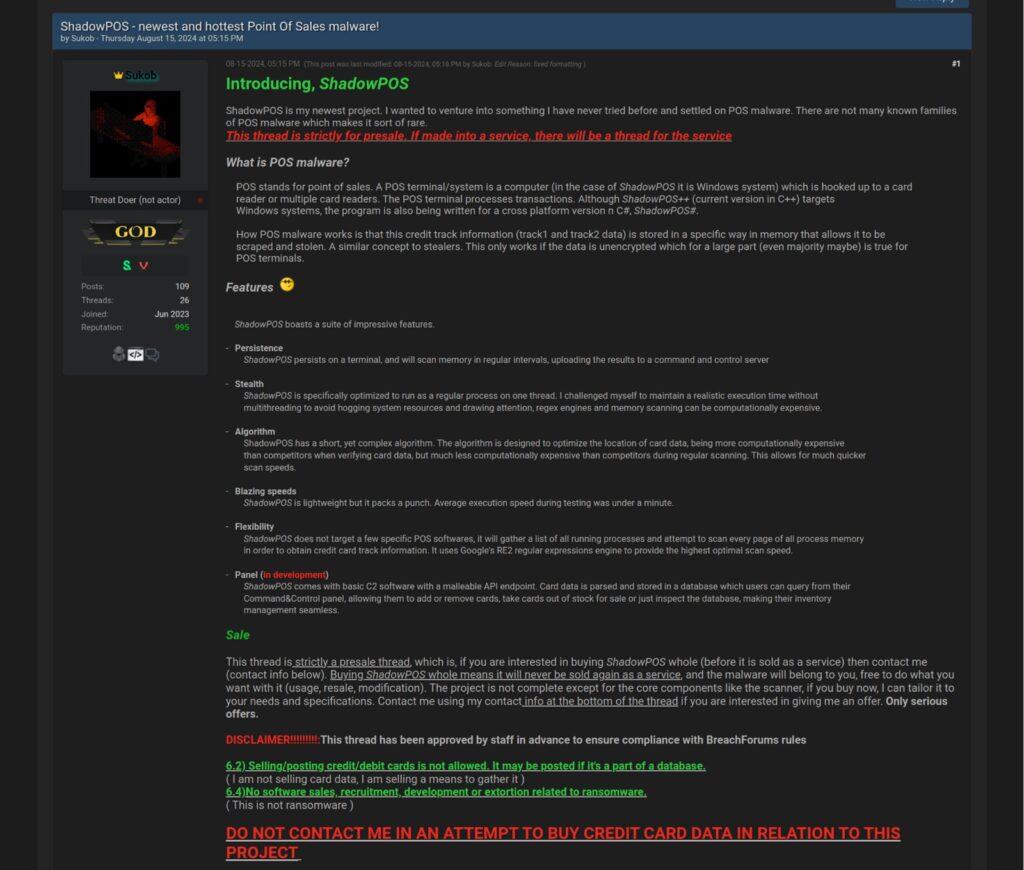
Question: Can you explain the functionalities and advantages of your ShadowPOS malware compared to other Point of Sale malware?
Sukob: I was bored and wanted to create something other than a bootloader type or a C2 agent. I thought of the easiest way to monetize malware and scams came to mind. It’s pretty simple, it works like most POS malware, and it cleans up memory using regular expressions. I think this is a good thing since it’s written in C++ and I’ve added optimization features that have reduced the memory scan time from hours to minutes.
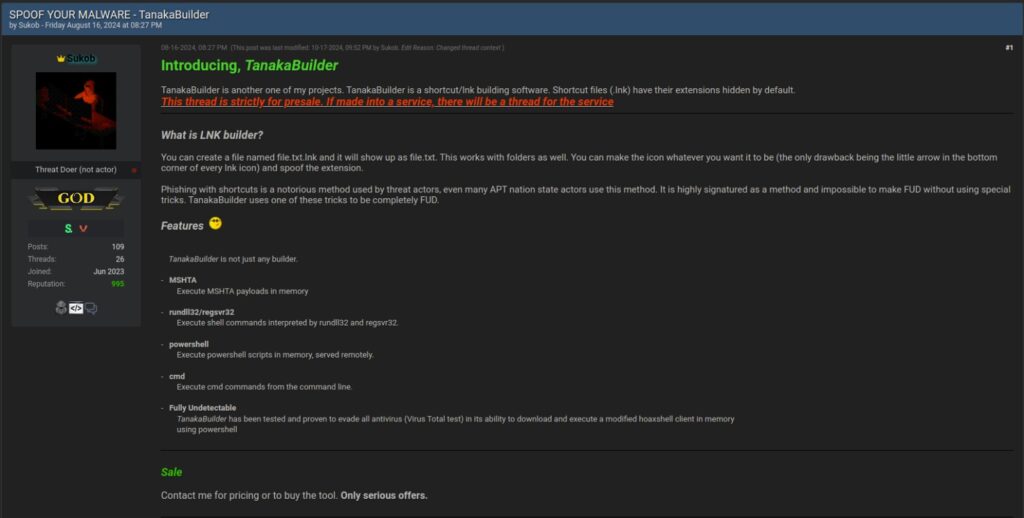
Question: How does TanakaBuilder assist in spoofing malware, and what makes it mandatory for threat actors’ operations and how has it been beneficial to you?
Sukob: If I were an attacker who has public TTPs, then one of them would definitely be doing email phishing. I think a good combination of social engineering and malware is the most effective way to compromise any host. When people think of hackers on a national level, they think of spies in a lab in America or Russia with zero days. In fact, they are easy to burn, they just organize a malicious and targeted phishing operation and exploit people instead of services. Tanaka is good for that. Essentially, it can simply create shortcut files that deliver malware and download malicious modules. I test all antiviruses, and I’m currently working on a very rare, standalone type of encryption loader that is delivered using lnk. This would be a new method. I try to keep all my operations fileless and I used the LOTL technique, or whatever you call it – “living off the land”.
Technically speaking, TanakaBuilder is just a shell that generates a payload of a shortcut file. They appear to the user as a fake file extension because the extension “.lnk” is hidden in Windows. This is a common technique among high-level attackers, although I think the real art lies in the implementation.
Question: Does TanakaBuilder have anything to do with the person operating on BreachForums under the username “Tanaka”?
Sukob: Not directly I just named it after him, I could not decide a good name and he was in chat when I had the idea.
Question: What’s the motive of selling network access to companies instead of making a big profit from ransomware?
Sukob: Ransomware attracts too many eyes and ears, especially Americans. It’s no secret that I’m from the East. Most hackers like me live in the Twilight Zone, our government won’t go after us because we don’t commit crimes against our people, but at the same time, Americans can get you if you make too many mistakes. I think the FBI will only go after you seriously if you make a big mess in the news. As long as you keep your head down, you can make money for a long time. Selling access is a simple and mostly secure job for a single person or a small group. If the crime is investigated, the ransomware group will be the prime suspect, most law enforcement agencies are not even aware of the ransomware industry and the initial access market.
Question: Here are you referring to CIS countries?
Sukob: Yes
Question: What’s your opinion on the proliferation of stealer logs? Give me a rough idea about your use of stealer logs to gain initial access.
Sukob: This is a very popular technique. A lot of major hacks in the last year were related to them, I’m aware of that, but they have a much bigger niche in the market. They can be used for a variety of fraud. I’ve wanted to get into the stealer logs at some point, but the market is already saturated, I think that too many bands already have too many good products. Personally, I’ve never used stealer logs. I like it when hacking is fun, and logs are like a pay-to-win cheat.
Question: When a target initiates incident response procedures, what steps do you take to avoid detection or removal? Can you share examples of successful evasion tactics you’ve employed during active incident responses?
Sukob: I can’t specify the methods I use, especially for Windows, because they tend to be so niche that they can be considered an asset. It’s pretty simple on Linux. As a rule, I use different domains. Maybe if it’s a really good access, I’ll put my temporary SSH key on the server, and steal passwords/SSH keys. DFIR doesn’t usually reset them, or at least in my experience. Last month we were in the network of one company. We were removed 4 times, but we sort of “side loaded” our implant into critical service, so every time the service started, the implant remained healthy. I also use the beacon’s long sleep time for the initial approach. I don’t do any post-exploitation, so the beacon can sleep all day if I want to. Also, it is good to spread to several machines, sometimes hidden in devices that will not be looked at but are also easily exploitable, something like a router or an IoT device like a security camera. Nobody will ever suspect that the hacker is in your security camera.
Question: How do you vet and onboard new members to ensure they align with your group’s goals and security protocols?
Sukob: I can’t speak for Hellcat because I’m not responsible for any of that, I play a small role in this band. In the past, there was usually a leader of the group. One of the participants brings someone they trust to the group leader, and it’s up to the group leader to add them or not. The feds are aware of this and will try to infiltrate the groups. It is very important that your groups are as small as possible from a functional point of view, we are organized criminals, not a social technology club. Also, in the past, my groups have used a zero-trust structure, a kind of terrorist cell architecture. So, if one of the participants is compromised, they are likely to know very little about the operation. For example, in the past, we hired a malware developer and told them to create a certain piece of malware. It doesn’t ask questions and will later find out where it was used if it appears in the news.
Question: In businesses, there are often specialized roles like managers, developers, and negotiators. Is it similar in your group, or do people take on multiple roles?
Sukob: Yes, absolutely. In my experience, the best groups are well organized. For example, in a group that covers many of my topics (t[.]me/FreshAccess), we have people in charge of malware, gaining access, and negotiating deals. Sometimes responsibilities overlap. This group is very small, but in the past, more successful operations required different people with different talents. Sometimes someone is a hacker and doesn’t hack at all.
Question: What strategies do you use to stay ahead in the competitive ransomware market?
Sukob: I don’t work in the ransomware market, at least not intentionally. I sell access to someone who wants to pay for it, and it’s a no-questions-asked transaction, especially when it’s done privately. It’s possible that some of my clients are ransomware groups, but they usually exchange messages on temporary accounts. The entire transaction is secure and anonymous. I have a suspicion that many of my clients work in the intelligence community. Only this month, but also 2 years ago, there was a period when I received large offers from a single client who wanted access to a specific type of server, usually targeting a specific country or organization. The money they offer for this is many times the cost of access on the secondary ransomware market, so I have reason to believe that they have other motives.
Question: Are there any specific targets or sectors you avoid when deploying ransomware? If so, why?
Sukob: Depending on the country, I’ll try to avoid the government, unless I have a contract to infiltrate one. I’m not going to directly target the U.S. government. Access to them would pay a decent price, but don’t be an enemy of the Department of Justice. The government is very cheap for most countries and does not respond well to extortion. In addition, they have more options to prosecute you through the military and law enforcement than any other organization you target. I’m also not going to sell access to critical infrastructure (other than telecommunications), healthcare, and anything below average.
Question: Are there any specific targets, sectors, or countries you avoid when deploying ransomware? If so, why?
Sukob: To be clear from the last question, I’ve never dealt with ransomware. In terms of goals or sectors, there are really many. The rule of thumb is that you want to buy big fish with more than $1 billion in revenue and from a rich country like the United States or oil-rich countries in the Middle East, or from Western Europe like Germany or the United Kingdom. As for the sector to target, ransomware clients will buy targets with large budgets and a lot of critical business infrastructure, i.e. It’s like an app development company in Silicon Valley. If you encrypt their servers, they won’t generate any revenue. As for intelligence clients, they will want access to them, such as telecommunications for espionage or universities and technology companies with valuable intellectual property.
This is of course just a theory. I never follow up on access I have sold but in the past I see that it does not make the news.
Question: Do you collaborate with other ransomware groups or cybercriminal entities to share resources, knowledge, or infrastructure? If so, how does this collaboration enhance your operations?
Sukob: Yes all the time. You will succeed anywhere in the community if you do not cooperate with others, especially in the development of malware. I’ll have a problem on one hand and a solution for the other on the other, and when I come across a person with a solution to my problem, I hope I have a solution to one of their problems and we can trade with intelligence. Techniques are usually stored safely because when they are used up, they burn up and you need to make or buy a new one. This, in my experience, is the currency of malware writers. Sometimes you will need infrastructure, so you make trades. It’s rare for me to see a single cybercriminal pay another who is his friend for a favor, usually, trade is acceptable. In the past, I traded loaders for bulletproof servers and so on. Forums such as BreachForums are great for connecting and meeting other people with whom you can share tactics. Some people are really nice, hackers are not like most criminals, many of us have a childlike curiosity that reaches its peak through every insidious façade with which the media can paint us.
Question: Talking about Bulletproof hosting, what BPHs are the best in your opinion? What features do you look for on such hosting providers to set up your loaders?
Sukob: In fact, I don’t prefer bulletproof hosting. I don’t post illegal content for weeks. All malware that I use will be disconnected from the Internet after a maximum of one month of operation. I’m also connecting anonymously, so I don’t care if the server is hijacked. A good past method is to grab outdated but forgotten sites and have your C2 and staging site set up and running on the site. In the past, I’ve even embedded PowerShell stages into the HTML of a website. Instead of network analysts seeing an implant connecting to a domain that was registered a week ago on a “bulletproof server”, they see a user of their network using a 14-year-old site and searching for endpoints with actual web pages. Another typical method is to use credit card fraud to rent a cheap server temporarily. The only use I can see for BPH is in the case of a botnet or something persistent. Your entire malware operation should be able to be set up and disassembled quietly, clandestinely and in only a matter of minutes.
Question: Do you work on a percentage basis with the Hellcat group?
Sukob: I cannot disclose this. In the past with similar groups, a fair cut is decided before any attacks usually. If only a few members work on one project then only they get a cut. It is standard like any business, with no handouts.
Question: What’s your approach to targeting a network – starting with selecting a target to compromising it? Can you give us a general overview?
Sukob: As I said in another answer, my favorite method is spear phishing. I think the human factor is worrisome. As for exploitation, I know many methods. The most popular ones I see are the use of the stealer logs. I don’t think passwords as a concept are designed with security in mind, because honestly, they protect services terribly. Someone has to invent some new authentication protocol that doesn’t involve remembering the username and password. Something like a standardized wallet with a hardware key, or even a software wallet. Malware can easily steal this, which is the only bad part of the idea, but perhaps biometric authentication will become more widely used in the future, and these wallets can be protected by it.
To protect myself from spear phishing, I can’t tell you because I have to pay rent. I’m just kidding, I honestly can’t think of any way to protect myself from spear phishing. The delivery of malware itself is a constant game of cat and mouse, but if a hacker has FUD malware that uses their methods and has enough motivation and time to research the targets, it’s impossible to protect yourself from it. The best thing they can do is protect themselves from more frequent and bad attempts, pay for the training of their employees, have good rules for detecting all the common malware and payloads that you can see, maintain their systems so that they don’t allow them to hang easily, such as using exploits in the browser. They know it’s a real threat. One thing that makes me angry is that some executives don’t think that social engineering is a real hacking process, and they don’t believe in paying for protection. My message to them is that I’m real as a hacker with an advanced exploit, and with enough persistence I’ll be on your network.
Question: Thank you for your time, Sukob! Is there something else that we may have missed that you would like to tell us?
Sukob: No, I think this is all covered.
We appreciate your valuable time, Sukob!
Disclaimer
This interview is provided for informational purposes only and does not express approval, support or agreement with any actions mentioned in the text. The author of the publication is not related to the activities described in the interview and is not responsible for any consequences of using the information provided.
The interview materials are intended to raise public awareness of modern cyber threats and the methods of cybercriminal groups. The publication of this text does not constitute propaganda of illegal activity and does not encourage violation of laws.
Readers are advised to always observe legal regulations and consult with the appropriate authorities if they have questions about the topics covered in this interview.



Comments (2)
Threat Actor Interview: Spotlighting on Pryx– Admin of the Hellcat Ransomware Group - Osint10xsays:
December 17, 2024 at 10:54 pm[…] had also recently interviewed two actors “Sukob”, loosely affiliated with the Hellcat group and ”Miyako“, one of the admins of the […]
Emerging Hellcat Ransomware Group Targets Government Entities and High-Revenue Organizations - Osint10xsays:
December 31, 2024 at 9:17 am[…] Threat Actor Interview: Spotlighting on Sukob – Affiliated with Hellcat Ransomware Group Threat Actor Interview: Spotlighting on Pryx – Admin of the Hellcat Ransomware Group […]