The Apos ransomware group surfaced in April 2024 on a well-known cybercrime forum. In the chat-interview, they describe Apos as a company specializing in data security that provides their services to companies that want to restore their data or prevent its publication. The group refers it as a Next Generation (NG) Ransomware-as-a-Service (RaaS) program. It supports all major operating systems (Windows, Linux, ESXi, BSD, NAS) and architectures used in enterprises.
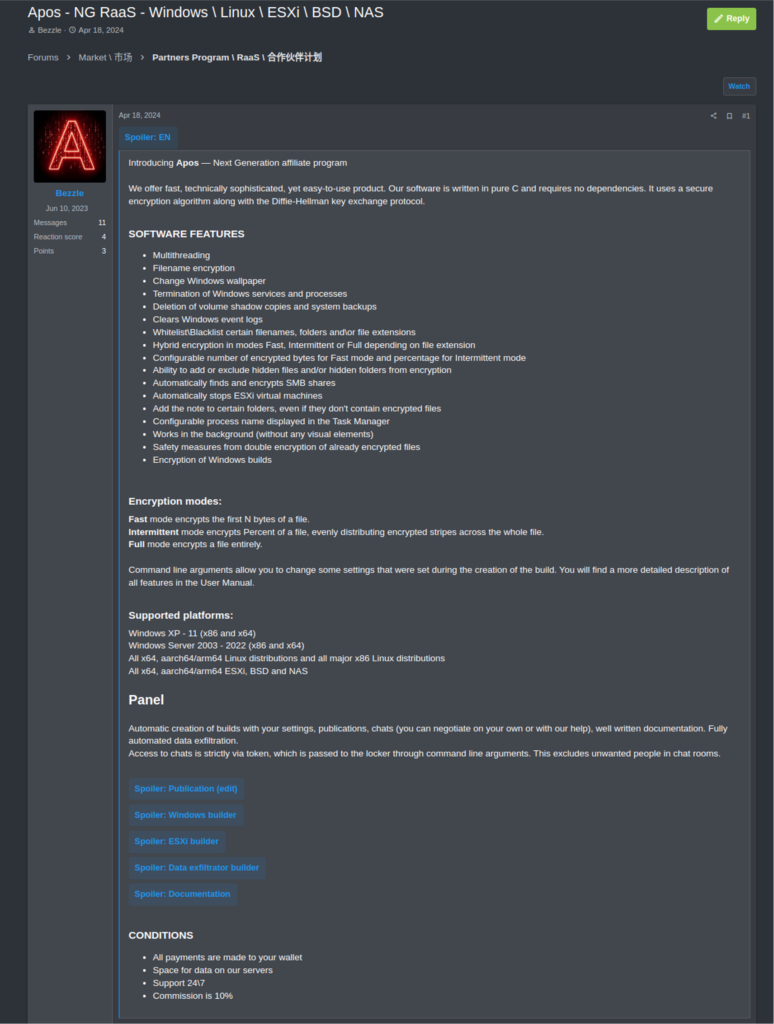
During their initial operation, they listed four victims on their Data Leak Site (DLS) before abruptly ceasing activity. They plan to release a “Lite” version of their software, specifically for Windows users. This version might have fewer features than the full version but is designed to reach a broader audience or use case.
Stay Updated with Our Newsletter
Key Findings:
- Emerged in April 2024
- Next-Gen RaaS program that supports all major operating systems (Windows, Linux, ESXi, BSD, NAS)
- Listed 4 victims on their DLS
- Lowest commission rates (10% for every successful ransom)
- Plans on using AI for faster data analysis and looking for key information
- Looking to partnership with initial access brokers (IABs) to speed up the work
- Discourage targeting critical infrastructure across the globe
- Recommends taking regular backups, use strong passwords and MFA, Antivirus, and timely update software.
We have got an opportunity to interview Apos Ransomware group who talked about their motivations, current RaaS model and future plans. Below we have presented the questions and answers without any modification.
Question: We’re excited to have you here, APOS, for your first interview with osint10x! To start, could you share a bit about yourself? Let the audience know what you do and why did you decide to work in this sector?
Apos: Apos is a company specialized in data security. We provide our services to other companies that want to restore their data or prevent its publication. Some time ago I was looking for a way to earn, and then I saw an article about ransomware. I liked the idea and decided to dive into it. That’s how a plan to create Apos was born. Although, a plan to create Apos didn’t come at once. Quite a lot of time has passed before it.
Question: Before you started your RaaS program, were you former affiliates or developers of any ransomware groups who wanted to go out on your own? Can you tell us your motivations for opening this new RaaS?
Apos: I worked with other groups before, mostly as a developer. I wanted to create a RaaS of the next generation, which would automate some tasks such as data exfiltration, encryption and data analysis. You know that sometimes there is a lot of information in the exfiltrated data, sometimes in languages that affiliates don’t speak. So I plan to add AI that will analyze it. I’m sure it is possible to implement, but the problem comes when there is too much data, for example, 100s of gigabytes or terabytes. Though I think it won’t take too much time to finish it. I should make it easier to find valuable information and save time.
Question: Now let’s talk about your solution. If you were to say, how does your program differ from other ransomware such as the popular LockBit 3.0 or Akira?
Apos: It supports all major operating systems (Windows, Linux, ESXi, BSD, NAS) and architectures used in enterprises. It’s very easy to use, you configure parameters in the builder and then get an executable that you can launch on all machines in the target’s network. Settings structure is universal for all versions.
Question: If you had to explain to a potential affiliate why to start a partnership with you, what would you say from a technical point of view regarding your solution?
Apos: Our commission is one of the lowest on the market – just 10%, we also provide storage for data exfiltration, affiliates don’t need to buy their own storage.
Encryptor can propagate in the network, it can encrypt all files except excluded (by extension, filename, or directory filter), or it can only encrypt selected files (same filter logic). Some embedded settings can be overwritten on launch. Encryptor deletes all logs and restore points, and automatically stops virtual machines. Encryptor changes filenames for encrypted files (this feature is present on all versions), which makes even partial restoration of a file impossible. This works great with hybrid encryption scheme – we can encrypt (fully of %) of actually important files (like databases, virtual machine files), and encrypt only the headers of other files. It saves a lot of time and does not compromise security. If a company wants to see how much encrypted their files, it would need to inspect every single file in a hex editor. Apparently it is not an option when you have thousands of such files. You can encrypt hundreds of gigabytes in a couple of minutes.
Question: Talking about collaborators, how are you organized?
Apos: Right now we don’t provide accesses for affiliates, but in the future we will partner with access providers to speed up work for everyone.
Question: What is the selection process for the Apos affiliation program?
Apos: We are looking for results. If a potential partner can show us that he has skill, then we accept him. But if during some period of time he’s inactive, then we may worn him about potensial account suspension.
Question: And, what would you say to convince potential new collaborators join your group?
Apos: All payments are made to affiliate’s wallet first. We don’t scam people. We listen to feedback and make appropriate adjustments in our platform.
Question: What’s your approach on Initial Access into victim network? I know you have mentioned that you currently have no access providers for your partners. In general, do you rely on credential broker (and similar) or you prefer do it by yourself?
Apos: Right now this decision is left to an affiliate. Some buy them, some use CVEs, others do brute force. We will buy them.
Question: How do you select targets – revenue/geo/industry? Do you have any rules for selecting targets?
Apos: Affiliates target who they want, but we will notify if a target is off limit. Off limit maybe critical infrastructure or CIS countries.
Question: Critical Infrastructure across the globe or just for CIS countries?
Apos: Globe
Question: Based on your experience, how is security implemented within companies network? What should professionals focus on to elevate industry standards?
Apos: Smaller companies tend to have lower security (probably due to lack of funding), but sometimes even mid-size to big companies make mistakes. Professionals should follow basic cybersecurity: make backups, use strong passwords, MFA, use Antivirus, update software.
Question: Your job comes with high risk and high stakes, how does Apos keep with ransomware activity and at the same time stay safe? Is it worth the risk?
Apos: It is worth the risk. Follow OPSEC practices, don’t make stupid mistakes, like sending your coins directly to your Binance without cleaning them; use disposable emails, VPN/proxy/VPS, don’t leave traces.
Question: You probably know what happened between Lockbit and Operation Cronos, are you worried that law enforcement would put always more efforts on takedown groups like yours? You saw some changes/reaction after Operation Cronos?
Apos: I’m not worried, but we will try our best to secure our operation from such unfortunate events.
Question: Have you ever failed one of your attacks? What was the point of failure?
Apos: Not every attack will be successful. A company’s SOC team may notice the intrusion and kick us out.
Question: Apos, thanks a lot for your time! Is there anything you’d like to say that we haven’t asked you?
Apos: We plan add new features in the future, and a Lite version for Windows that will have a business model like Phobos. And we are always glad to accept experienced pentesters. Thanks for interviewing us as well.
Disclaimer
This interview is provided for informational purposes only and does not express approval, support or agreement with any actions mentioned in the text. The author of the publication is not related to the activities described in the interview and is not responsible for any consequences of using the information provided.
The interview materials are intended to raise public awareness of modern cyber threats and the methods of cybercriminal groups. The publication of this text does not constitute propaganda of illegal activity and does not encourage violation of laws.
Readers are advised to always observe legal regulations and consult with the appropriate authorities if they have questions about the topics covered in this interview.




Leave a Reply