| Category | Details |
|---|---|
| Threat Actors | Unknown threat actor |
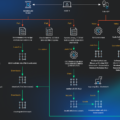
| Campaign Overview | Phishing campaign using Gophish toolkit; delivers PowerRAT and DCRAT; involves modular infection chains requiring user intervention. |
| Target Regions | Russian-speaking users in Russia, Ukraine, Belarus, Kazakhstan, Uzbekistan, and Azerbaijan; phishing emails masquerade as VK social media content. |
| Methodology | Phishing emails with malicious Word documents and HTML files containing JavaScript. |
| Product Targeted | VK (Vkontakte) social media application. |
| Malware Reference | PowerRAT, DCRAT, GOLoader, SFXRAR executables. |
| Tools Used | Gophish phishing toolkit, PowerShell, JavaScript, SFXRAR, GOLoader. |
| Vulnerabilities Exploited | Abuse of Windows NT autorun registry key (HKEY_CURRENT_USER…\LOAD); modification of Microsoft Defender Antivirus settings. |
| TTPs | Phishing, modular payload delivery, PowerShell execution, registry abuse, base64 encoding, reconnaissance, C2 communication, information stealing, DLL injection, keystroke logging, and persistence through file disguise. |
| Attribution | Overlaps with techniques from earlier SparkRAT attacks (April 2024). |
| Recommendations | – Avoid enabling macros in documents from unknown sources. – Regularly monitor and secure autorun registry keys. – Strengthen email filtering to detect phishing. – Update antivirus signatures and block C2 domains. |
| Source | Cisco Talos Blog |
Read full article: https://blog.talosintelligence.com/gophish-powerrat-dcrat/
Disclaimer: The above summary has been generated by an AI language model


Leave a Reply