Cleo File Transfer Vulnerability Under Exploitation – Patch Pending, Mitigation Urged
Attribute Details Threat Actors Termite ransomware group (potentially linked to Cl0p/Lace Tempest) Campaign Overview Mass…
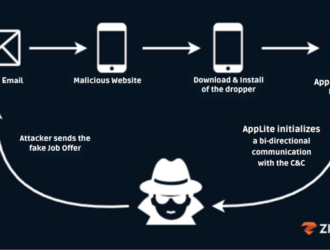
Hackers Target Job Seekers with AppLite Trojan Using Fake Job Emails
Attribute Details Threat Actors Unnamed threat actors posing as recruiters/HR teams from reputable companies Campaign…
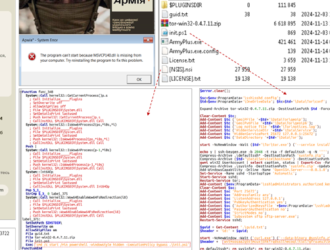
Fake Recruiters Distribute Banking Trojan via Malicious Apps in Phishing Scam
Attribute Details Threat Actors Not attributed to a specific group; possibly financially motivated adversaries Campaign…
Widespread exploitation of Cleo file transfer software (CVE-2024-50623)
Attribute Details Threat Actors Financially motivated adversaries Campaign Overview Exploitation of Cleo file transfer software…
PROXY.AM Powered by Socks5Systemz Botnet
CategoryDetailsThreat Actors- BaTHNK: Original creator of Socks5Systemz.- Boost: Reseller of BoostyProxy linked to Socks5Systemz.- Alexey…
Termite Ransomware Attack on Blue Yonder: What You Need to Know
Category Details Threat Actors Termite ransomware group, an emerging variant of Babuk ransomware. Campaign Overview…
Hackers Weaponize Visual Studio Code Remote Tunnels for Cyber Espionage
Category Details Threat Actors Suspected China-nexus cyber espionage group; no specific attribution to a known…
OpenWrt’s Attended SysUpgrade (ASU) Vulnerability Exposes Routers to Malicious Firmware Attacks
Category Details Threat Actors Not applicable (vulnerability exploitation by any malicious actors possible). Campaign Overview…
Ongoing Phishing and Malware Campaigns in December 2024
Category Details Threat Actors Not specified (multiple cybercriminal groups using different attack methods). Campaign Overview…
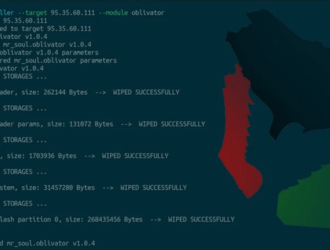
CERT-UA Warns of Phishing Attacks Targeting Ukraine’s Defense and Security Force
Category Details Threat Actors UAC-0185 (also known as UNC4221), a Russia-linked threat actor. Campaign Overview…