| Category | Details |
|---|---|
| Threat Actors | Socks5Systemz botnet, PROXY.AM proxy service, Gafgyt botnet, NSOCKS. |
| Campaign Overview | Socks5Systemz turns compromised systems into proxy exit nodes, enabling cybercriminal activities; Gafgyt targets Docker API servers for DDoS attacks. |
| Target Regions (or Victims) | High infection rates in India, Indonesia, Ukraine, Algeria, Vietnam, Russia, Turkey, Brazil, Mexico, Pakistan, and 12 others; Docker instances globally. |
| Methodology | – Proxy malware (e.g., Socks5Systemz, Ngioweb) turns infected systems into proxy servers. – Gafgyt exploits weak SSH passwords and misconfigured Docker APIs. |
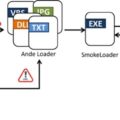
| Product Targeted | PrivateLoader, SmokeLoader, Amadey (Socks5Systemz loaders); Docker remote API servers (Gafgyt). |
| Malware Reference | Socks5Systemz V1 and V2, Gafgyt botnet, Ngioweb. |
| Tools Used | – Loaders: PrivateLoader, SmokeLoader, Amadey (Socks5Systemz). – Gafgyt botnet leveraging Alpine Docker containers. |
| Vulnerabilities Exploited | Misconfigured Docker remote APIs, weak SSH passwords, sensitive cloud credentials in misconfigured services. |
| TTPs | – Rebuilding botnet with new C2 infrastructure (Socks5Systemz V2). – Leveraging cloud misconfigurations for cryptocurrency mining, data theft, and DDoS. |
| Attribution | Threat actors leveraging Socks5Systemz and Gafgyt botnets; research teams: Bitsight, Lumen’s Black Lotus Labs, and Trend Micro. |
| Recommendations | – Strengthen system administration and oversight. – Fix cloud misconfigurations. – Use strong SSH credentials. – Monitor Docker APIs. |
| Source | The Hackers News |
Read full article: https://thehackernews.com/2024/12/socks5systemz-botnet-powers-illegal.html
Disclaimer: The above summary has been generated by an AI language model



Leave a Reply