
New day, a new menace for cyber defenders. Recently, security researchers from ThreatLabz have uncovered two novel malicious strains adding to the 100 million count of those already identified in 2024. As per reports, the newly revealed RevC2 and Venom Loader have been making the rounds since the summer of 2024, leveraging Venom Spider’s Malware-as-a-Service (MaaS) platform for deployment.
Detect RevC2 and Venom Loader
Following closely after the SmokeLoader attacks targeting Taiwanese organizations, security experts have identified a new, sophisticated campaign distributing the RevC2 and Venom Loader malware strains. To outscale emerging threats and identify cyber attacks at the earliest stages of development, cyber defenders can rely on SOC Prime Platform for collective cyber defense. The Platform aggregates a dedicated Sigma rules stack aimed at RevC2 and Venom Loader detection accompanied by a complete product suite for advanced threat detection and hunting.
Press the Explore Detections button below and immediately drill down to a relevant set of detections to spot the malicious activity linked to RevC2 and VenomLoader. All the rules are compatible with 30+ SIEM, EDR, and Data Lake technologies, mapped to MITRE ATT&CK®, and enriched with extensive metadata, including CTI links, attack timelines, and triage recommendations.
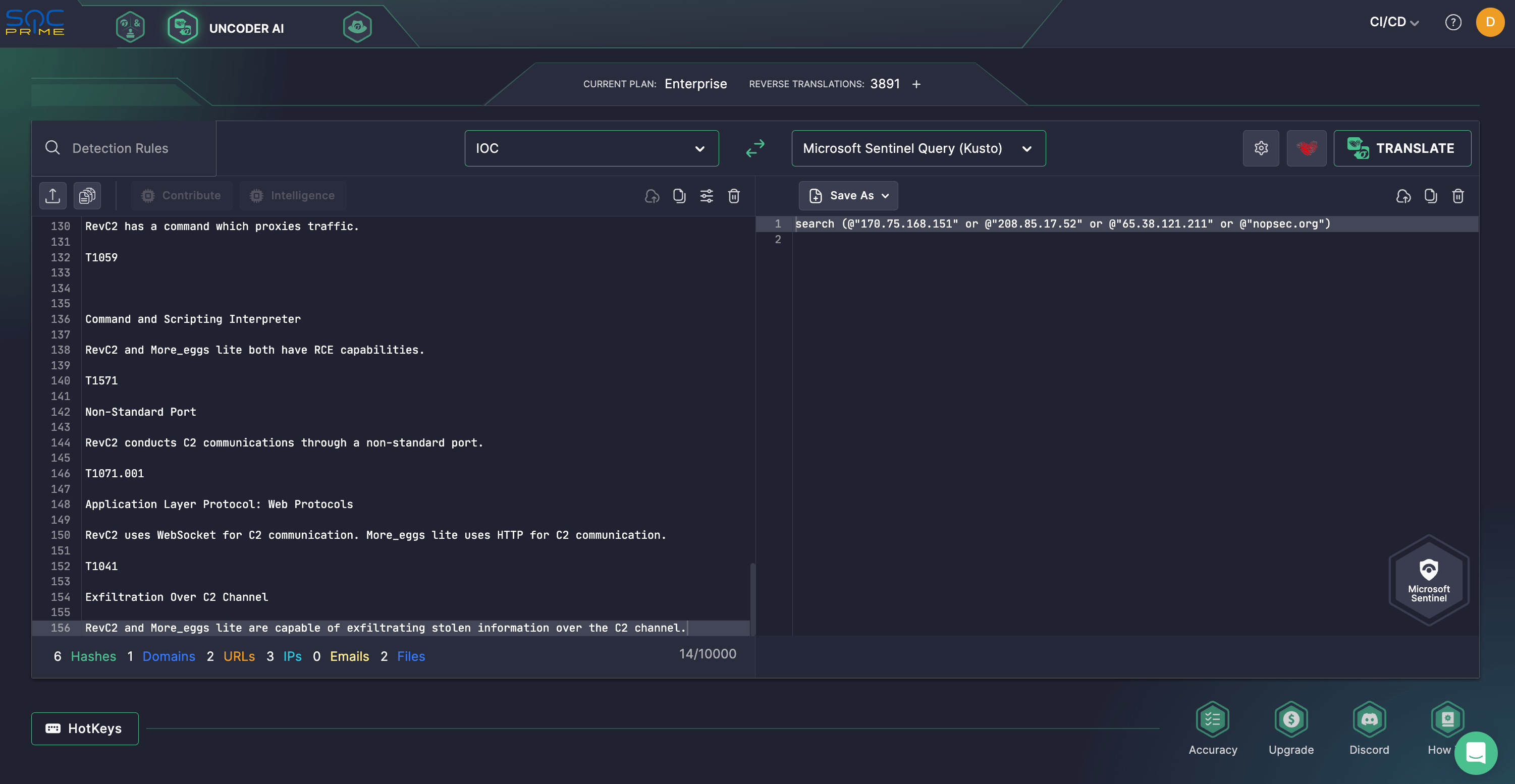
Security engineers can also leverage Uncoder AI to streamline the IOC packaging and retrospective analysis of adversaries’ TTPs seen in revC2 and Venom Loader attacks. Instantly convert IOCs from the corresponding research by Zscaler ThreatLabz into tailored queries compatible with various SIEM, EDR, and Data Lake languages.
RevC2 and Venom Loader Analysis
Zscaler ThreatLabz has recently identified two novel malware families dubbed RevC2 and Venom Loader distributed in two noteworthy offensive campaigns throughout the period between August and October 2024 via Venom Spider MaaS Tools.
RevC2 utilizes WebSockets for communication with its C2 server. The malware can steal cookies and passwords, redirect network traffic, and facilitate RCE. Another uncovered malicious sample from Venom Spider’s offensive toolkit is a newly developed malware loader dubbed Venom Loader, which is uniquely tailored to each target by encoding the payload using the victim’s computer name.
Venom Spider, also referred to as GOLDEN CHICKENS, is a hacking collective notorious for providing MaaS tools, including VenomLNK, TerraLoader, TerraStealer, and TerraCryptor. These offensive tools have also previously been employed by other adversary groups like FIN6 and Cobalt.
The first malicious campaign delivers the RevC2 backdoor using an API documentation lure. The infection chain starts with a VenomLNK file containing an obfuscated batch script that downloads a PNG file disguised as API documentation.
The script registers an ActiveX control to execute the RevC2 malware, which checks if the first argument ends with dWin.ocx and the executable path matches regsvr32.exe, ensuring activation only in legitimate attack chains and thus facilitating detection evasion. RevC2 uses WebSockets for C2 communication via the websocketpp library. Notably, ThreatLabz researchers have provided a Python script to emulate a RevC2 server, available on GitHub.
Another offensive campaign by Venom Spider uses cryptocurrency transaction lures to spread Venom Loader, which deploys the More_eggs lite backdoor, a JavaScript-based tool potentially leading to RCE. The attack flow begins with a VenomLNK file containing an obfuscated BAT script that writes and executes additional scripts. Those scripts download and display a cryptocurrency transaction image to the victim while fetching a malicious payload (base.zip) in the background. The payload extracts and runs an executable file, which sideloads a custom DLL (dxgi.dll) to initiate Venom Loader.
Venom Loader then launches More_eggs lite, establishes persistence through the Windows autorun registry, and uses HTTP POST requests to communicate with its C2 server. Commands are delivered via JSON responses, decoded, and executed on the compromised system.
As defenders have unveiled multiple campaigns leveraging RevC2 and Venom Loader, which are still under development and are expected to evolve, gain more sophisticated capabilities, and apply more detection evasion techniques, organizations are encouraged to maintain cyber vigilance against growing threats. SOC Prime’s complete product suite for AI-powered detection engineering, automated threat hunting, and advanced threat hunting serves as a next-gen all-in-one solution to ensure proactive cyber defense against evolving threats in a modern fast-paced cyber threat landscape where each second counts.
The post RevC2 and Venom Loader Detection: New Malware Strains Massively Deployed via MaaS in a Sophisticated Campaign appeared first on SOC Prime.


Leave a Reply