| Category | Details |
|---|---|
| Threat Actors | Unknown (Phishing actors targeting Kaiser Permanente), SocGholish operators. |
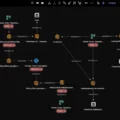
| Campaign Overview | Malicious Google Search Ads targeting Kaiser Permanente employees to steal credentials or infect systems via SocGholish malware. |
| Target Regions (Victims) | U.S.-based employees searching for Kaiser Permanente HR portal. |
| Methodology | Google Search Ads with malicious redirects, compromised websites, phishing templates, and malware-laden scripts (SocGholish). |
| Product Targeted | Kaiser Permanente HR portal impersonation. |
| Malware Reference | SocGholish malware (delivers Update.js script for fingerprinting and potential follow-up attacks, including Cobalt Strike). |
| Tools Used | Google Ads platform, SocGholish malware framework, compromised website hosting phishing templates. |
| Vulnerabilities Exploited | Compromised core JavaScript libraries on the Bellona Software website. |
| TTPs | Ad-based phishing campaigns, compromised websites for phishing and malware delivery, SocGholish malware chain for targeted infections. |
| Attribution | Phishing campaign actors and SocGholish operators acted independently, targeting overlapping victims. |
| Recommendations | Avoid clicking on sponsored ads, use browser protection tools like Malwarebytes Browser Guard, monitor Google Ads transparency reports, update website libraries. |
| Source | Malwarebytes |
Read full article: https://www.malwarebytes.com/blog/news/2024/12/malicious-ad-distributes-socgholish-malware-to-kaiser-permanente-employees
The above summary has been generated by an AI language model


Leave a Reply