| Category | Details |
|---|---|
| Threat Actors | SilkSpecter, a financially motivated Chinese threat actor. |
| Campaign Overview | Phishing campaign targeting e-commerce shoppers during Black Friday in Europe and the USA to steal Cardholder Data (CHD), Sensitive Authentication Data (SAD), and PII. |
| Target Regions | Europe and the USA, targeting online shoppers. |
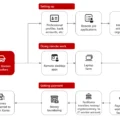
| Methodology | Fake e-commerce websites typosquatting legitimate domains; phishing lures promoting fake discounts; abused Stripe for real transactions while exfiltrating victim data. |
| Product Targeted | Online payment systems (e.g., Stripe); victims’ personal and payment information. |
| Malware Reference | Custom phishing kits leveraging Google Translate API, OpenReplay, TikTok Pixel, and Meta Pixel for tracking. |
| Tools Used | Fake domains (.top, .shop, .store, .vip); phishing kits; infrastructure from Chinese SaaS platform oemapps; Google Translate for localization; legitimate payment APIs. |
| Vulnerabilities Exploited | Abused legitimate services like Stripe for fraudulent purposes; SEO poisoning for visibility. |
| TTPs | Typosquatting; use of Mandarin comments in phishing code; DNS registrars from China; IP masking with Cloudflare; multilingual fake stores; exfiltration of sensitive data. |
| Attribution | High confidence attributed to SilkSpecter, linked to Chinese infrastructure, SaaS services, and language indicators in phishing kits. |
| Recommendations | Monitor Black Friday-themed phishing domains, use IOCs to track suspicious activity, employ virtual cards for online purchases, set transaction limits, and watch for targeted ASNs. |
| Source | EclecticIQ |
Read full article:https://blog.eclecticiq.com/inside-intelligence-center-financially-motivated-chinese-threat-actor-silkspecter-targeting-black-friday-shoppers
Disclaimer: The above summary has been generated by an AI language model



Leave a Reply