| Category | Details |
|---|---|
| Threat Actors | Inc. ransomware |
| Campaign Overview | Multi-extortion ransomware operation emerged in July 2023; steals and threatens to leak victim data unless ransom is paid. |
| Target Regions | Global, including healthcare, education, government, and technology industries. |
| Methodology | Initial access via spear-phishing or exploiting CVE-2023-3519 in Citrix NetScaler; uses COTS and LOLBINs for lateral movement. |
| Product Targeted | Healthcare, education, government, technology sectors. Victims include organizations across these industries. |
| Malware Reference | Inc. ransomware (uses specific command-line arguments for encryption and target selection). |
| Tools Used | NETSCAN.EXE, MEGAsyncSetup64.EXE, ESENTUTL.EXE, AnyDesk.exe. |
| Vulnerabilities Exploited | CVE-2023-3519 in Citrix NetScaler for initial access. |
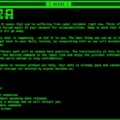
| TTPs | Data encryption, file/folder encryption commands, deletion of shadow copies, ransom note generation in .TXT and .HTML. |
| Attribution | No direct attribution mentioned. |
| Recommendations | Use anti-malware tools, monitor network traffic, conduct security audits, train employees, implement backup & recovery plans. |
| Source | SentinelOne |
Read full article: Inc. Ransom – SentinelOne
Disclaimer: The above summary has been generated by an AI language model.



Leave a Reply