| Category | Details |
|---|---|
| Threat Actors | Unidentified attackers exploiting CVE-2024-50603 for cryptojacking and deploying backdoors. |
| Campaign Overview | Active exploitation of a critical vulnerability in Aviatrix Controller, enabling unauthenticated RCE. |
| Target Regions (Victims) | Organizations using Aviatrix Controller in cloud environments (global impact). |
| Methodology | Exploitation of improper input sanitization in API endpoints to execute arbitrary OS commands. |
| Product Targeted | Aviatrix Controller versions prior to 7.1.4191 and 7.2.4996. |
| Malware Reference | Cryptocurrency miners and backdoors deployed on compromised systems. |
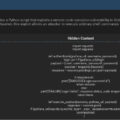
| Tools Used | Malicious commands (e.g., ; rm -rf /, ; download_malware.sh) to exploit the vulnerability. |
| Vulnerabilities Exploited | CVE-2024-50603: Command injection vulnerability due to improper handling of user-supplied parameters. |
| TTPs | Exploiting API endpoints, deploying malware, cryptojacking, lateral movement within cloud environments. |
| Attribution | Observed and analyzed by Wiz Research. |
| Recommendations | Upgrade to patched Aviatrix Controller versions, restrict network access, monitor logs, and conduct API security tests. |
| Source | Hackread |
Read full article: https://hackread.com/hackers-cve-2024-50603-aviatrix-controllers-backdoor/
The above summary has been generated by an AI language model



Leave a Reply