Many times we have come across phishing attempts. Many of us received phishing links via mail and messages on social media. Accidentally we clicked on those links also. One of the reasons behind that audacity is that those links seem genuine to us. Yes, you heard it right! Domain names can be easily manipulated by replacing characters, adding additional characters, or swapping letters. Threat actors can exploit this feature by creating malicious domain names that look similar to the legitimate ones. They trick the user to visit the fraudulent web page, and sometimes users get caught in their attempts at fraud also.
Here Comes an Useful Tool called Dnstwist. Dnstwist is a powerful tool used in the passive Reconnaissance of Domain Name Systems. It takes the target domain name as an input and generates permutations of the target Domain Name based on key parameters, allowing us to identify Phishing Domains early on. The tool also presents additional features like GeoIP resolution, domain availability, etc.
How to Install or Setup Dnstwist ?
Make Sure You have Python Installed . Copy the link from the Github Page of Dnstwist .
Github Page – https://github.com/elceef/dnstwist/blob/master/docs/demo.gif
Open the Terminal –
Step -1
Type – Git clone https://github.com/elceef/dnstwist.git
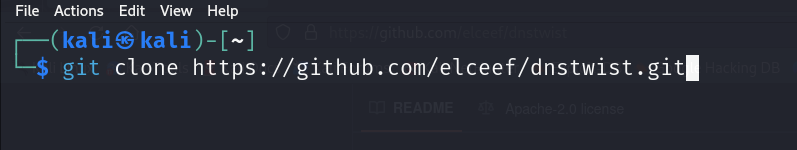
Step – 2
Type – Cd Dnstwist
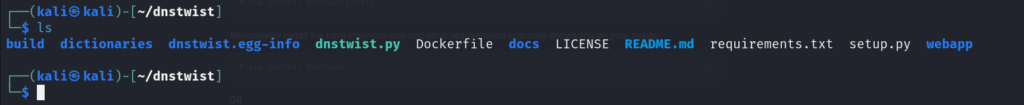
Use the “ls” command to list the files under the Dnstwist Directory .
Step – 3
Type – ./Dnstwist.py
It will list the Available flags for Dnstwist .
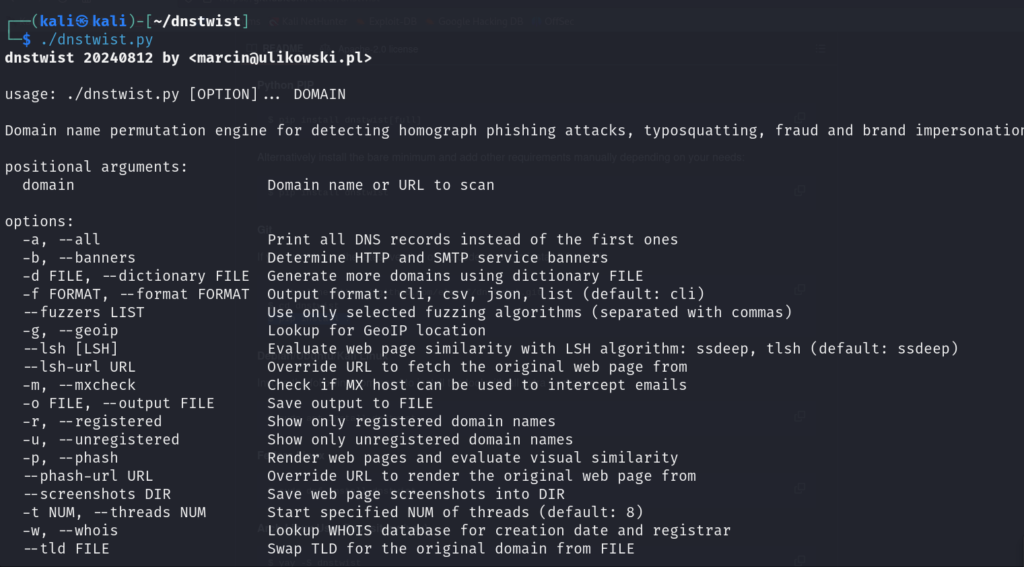
Step – 4
Type – ./Dnstwist.py -all < Target Domain >
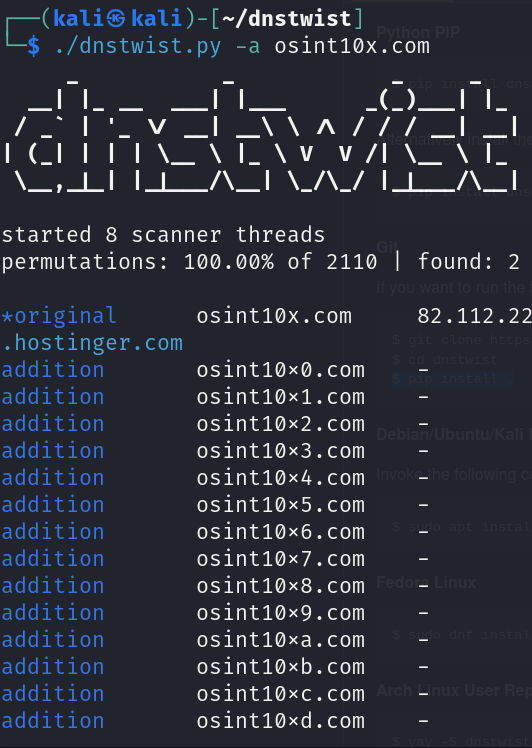
It will list the Additional Domains , Typosquat Domains , Homoglyphs , Bitsquatting Domains etc .
There is a GUI Web Version of Dnstwist also available .
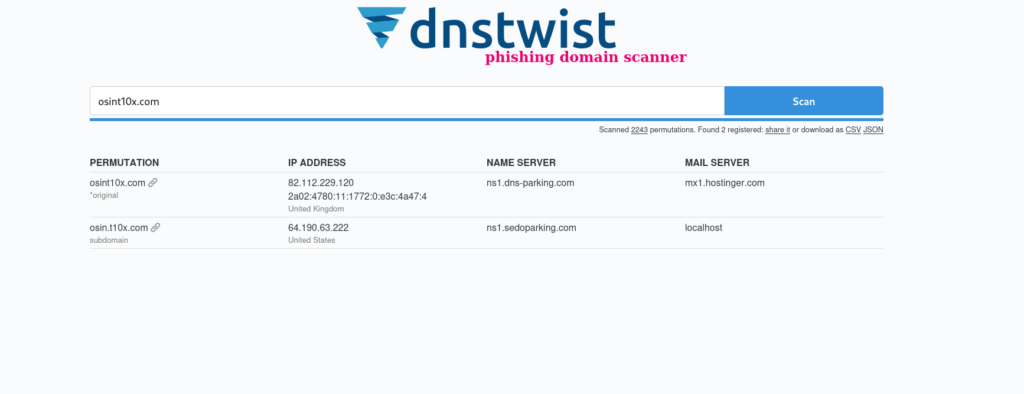
Link – https://dnstwist.it/
Use Cases of Dnstwist :–
Phishing Detection
Phishing links often look like legitimate websites. Threat Actors Manipulate the Domain Names, such as the legitimate link like osint10x.com, which looks like osint1Ox.com. They swap adjacent characters in domain names to create several variations of the original domain name. Dnstwist could be utilized to identify these malicious domains and report them to registrars for suspension or blocking in security tools like firewalls and email filters.
Threat Intelligence Collection
Threat researchers could utilize this tool to search and identify the malicious domains and resolve their IPs to strengthen their organization’s external attack surface. This information would be useful for the detection of phishing campaigns and threats that can cause disruption to business.
Summary :-
In this article, we have explored the possible use cases of the Dnstwist and how we can set it up for our work. Dnstwist is an invaluable asset of a Threat Researchers Arsenal that could give them the potential to increase their Productivity and Capability of Identifying Malicious Domains, Phishing Campaigns, etc.




Leave a Reply