Does Santa Like NordVPN? | Huntress
Huntress Managed ITDR uncovers risks behind popular VPNs and proxies like NordVPN, Mullvad, and more—helping…
Metasploit Weekly Wrap-Up 12/13/2024
It’s raining RCEs! It's the second week of December and the weather forecast announced another…
4.8 million healthcare records left freely accessible
Your main business is healthcare, so your excuse when you get hacked is that you…
DoJ Indicts 14 North Koreans for $88M IT Worker Fraud Scheme Over Six Years
The U.S. Department of Justice (DoJ) has indicted 14 nationals belonging to the Democratic People's…
Unlocking the Potential of Cyber Threat Intelligence: A Guide to the Threat Intelligence Maturity Model
A rapidly evolving cyber threat landscape demands that organizations adopt more than reactive defenses—they need…
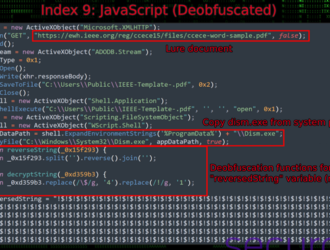
The Good, the Bad and the Ugly in Cybersecurity – Week 50
The Good | Ragnarok Ransomware Operators & DDoS-For-Hire Servers Disrupted by LEAs Law enforcement agencies…
5 Critical Questions to Ask When Evaluating MDR Solutions
With the ever-growing cybersecurity threats companies face today and a shortage of cybersecurity talent, it’s…
AWS re:Invent 2024 Highlights | Empowering Customers Through Innovations & Security in Cloud
Last week marked another action-packed year at AWS re:Invent for the SentinelOne Team. Year after…
How to Generate a CrowdStrike RFM Report With AI in Tines
Run by the team at orchestration, AI, and automation platform Tines, the Tines library contains…
Fluentd: How to Change Tags During Log Processing.
I have a case where I need to drop unnecessary logs. I found a plugin…
-330x250.webp)