5 Practical Techniques for Effective Cyber Threat Hunting
Addressing cyber threats before they have a chance to strike or inflict serious damage is…
How the Cyber Essentials Certification Can Help Your Business
Cybersecurity is a vital concern for organisations, but many security strategies fall short: recent research…
London’s CNI is Under Threat
London is one of the smartest and most interconnected cities in the world. Digital infrastructure…
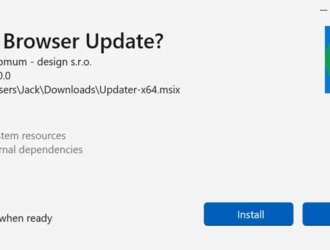
Hackers Exploit Webview2 to Deploy CoinLurker Malware and Evade Security Detection
Bogus software update lures are being used by threat actors to deliver a new stealer…
Download a banker to track your parcel
In late October 2024, a new scheme for distributing a certain Android banking Trojan called…
CISA and FBI Raise Alerts on Exploited Flaws and Expanding HiatusRAT Campaign
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added two security flaws to…
Using CAPTCHA for Compromise: Hackers Flip the Script
Key Points In our investigations, we identified malware campaigns using fake CAPTCHA pages that mimic…
Critical Apache Struts File Upload Vulnerability (CVE-2024-53677)—Risks, Implications, and Enterprise Countermeasures
Apache has announced a critical vulnerability affecting Apache Struts (CVE-2024-53677), a widely used Java-based web…
Earth Koshchei Coopts Red Team Tools in Complex RDP Attacks
APT group Earth Koshchei, suspected to be sponsored by the SVR, executed a large-scale rogue…