Dark Web Profile: Ymir Ransomware
AttributeDetailsThreat ActorsYmir ransomware group; RustyStealer malware as initial infection vector.Campaign OverviewGlobal ransomware campaign targeting organizations…
9th December – Threat Intelligence Report
Category Details Top Attacks and Breaches - Romania Election Interference: Russian-backed TikTok campaign and cyberattacks…
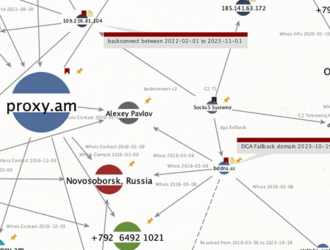
Socks5Systemz Botnet Powers Illegal Proxy Service with 85,000+ Hacked Devices
Category Details Threat Actors Socks5Systemz botnet, PROXY.AM proxy service, Gafgyt botnet, NSOCKS. Campaign Overview Socks5Systemz…
Story of the Year: global IT outages and supply chain attacks
Category Details Threat Actors APT actors targeting space industry, attackers exploiting supply chain vulnerabilities in…
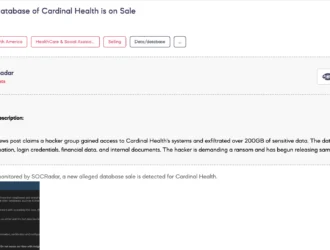
Renault India Breach, 147M Stealer Logs, Cardinal Health Leak, University ESXi & Saudi Company Access Sales
Category Details Threat Actors - Actors selling stealer logs, Renault India customer data, ESXi access,…
Cleo Software Actively Being Exploited in the Wild | Huntress
Category Details Threat Actors Not explicitly named, utilizing Cleo software vulnerabilities for exploitation. Campaign Overview…
AI Tools for OSINT: Modernizing Intelligence Gathering
We have compiled a list of free and paid AI OSINT tools for efficient research.…
New DroidBot Android Spyware Targeting Banking and Crypto Users
Category Details Threat Actors Believed to be a Turkish-speaking group; MaaS operation involves 17 affiliate…
Ultralytics AI Library Compromised: Cryptocurrency Miner Found in PyPI Versions
Category Details Threat Actors Unknown; exploited by an account named "openimbot," claiming association with the…
Hackers Using Fake Video Conferencing Apps to Steal Web3 Professionals' Data
Category Details Threat Actors Threat actors leveraging AI-generated fake companies for scams; malware delivered through…