Attack Behaviors | Huntress
In the cybersecurity community, we may hear analysts say, “Oh, threat actors change their tactics…”,…
The Rise of Social Engineering Across Healthcare | Huntress
Understand the impact of human error across healthcare, and discover how Huntress’ managed solutions can…
Smuggler’s Gambit: Uncovering HTML Smuggling Adversary in the Middle Tradecraft | Huntress
CategoryDetailsThreat ActorsUnknown; potentially a new Phishing-as-a-Service framework.Campaign OverviewMass phishing campaign combining HTML smuggling, Iframe injection,…
Insights from Our 2024 Cyber Threat Report | Huntress
Explore the interesting changes in the world of ransomware and more key findings from Huntress'…
Time to Act: Gaining the Edge with Huntress Response Capabilities | Huntress
Discover how Huntress MDR can respond swiftly to cyber threats and give you the critical…
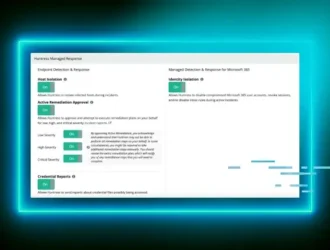
Active Remediation: Proactive Response with Huntress Managed EDR | Huntress
Learn how you can streamline incident response with Huntress Managed EDR's Active Remediation. Sleep soundly…
From South Park to Curriculaville: Meet Jeff Gill, Emmy Award Winner and Huntress SAT Animator | Huntress
Get to know Jeff Gill, Emmy award-winning storyteller and Huntress Security Awareness Training animator. Read…
Healthcare Held Hostage: Fighting the Plague of Ransomware | Huntress
Ransomware is spreading like wildfire. Learn about its growing threat to healthcare, its impact on…
LOLBin to INC Ransomware | Huntress
Huntress has observed INC ransomware deployed in the past but recent activity indicates a possible…
LightSpy Malware Variant Targeting macOS | Huntress
Category Details Threat Actors Unknown actors using LightSpy framework Campaign Overview Analysis of a macOS…