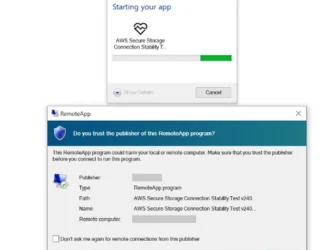
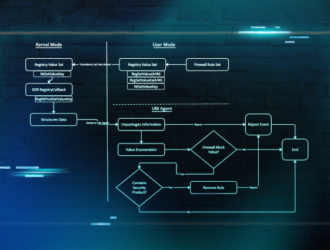
Security Brief: Actor Uses Compromised Accounts, Customized Social Engineering to Target Transport and Logistics Firms with Malware
Category Details Threat Actors Not currently attributed to a specific threat actor. Infrastructure overlaps with…
NVIDIA shader out-of-bounds and eleven LevelOne router vulnerabilities
Category Details Threat Actors Not specified. Campaign Overview Discovery of five Nvidia out-of-bounds access vulnerabilities…
Midnight Blizzard conducts large-scale spear-phishing campaign using RDP files
SectionDetailsThreat Actors- Midnight Blizzard (also known as APT29, UNC2452, Cozy Bear)- Attributed to the…
Silencing the EDR Silencers | Huntress
Discover how adversaries are using tools like EDRSilencer to tamper with EDR communications and learn…
Protect Yourself from Political Donation Scams | Huntress
Don’t let fraud disrupt your civic duty. Learn how to spot and avoid political donation…
Ransomware: Threat Level Remains High in Third Quarter
Recently established RansomHub group overtakes LockBit to become most prolific ransomware operation. Read More
Inside Adversary-in-the-Middle Attacks | Huntress
Discover how Adversary-in-the-Middle attacks silently hijack your sessions, and learn how to spot and prevent…
Top 3 Cybersecurity Threats of 2024 (So Far) | Huntress
Get to know 2024’s three biggest cyber threats—RMM abuse, BYOVD attacks, and WebDAV abuse—and learn…
Stonefly: Extortion Attacks Continue Against U.S. Targets
CategoryDetailsThreat Actors- Stonefly group (also known as Andariel, APT45, Silent Chollima, Onyx Sleet)- A…