| Category | Details |
|---|---|
| Threat Actors | Arcus Media |
| Campaign Overview | Ransomware group known for double extortion; encrypts data and threatens to leak it if ransom isn’t paid. |
| Target Regions | Various sectors globally, including government, banking, construction, IT services, and entertainment. |
| Methodology | Phishing, vulnerability exploitation, RDP access, and living-off-the-land techniques for lateral movement. |
| Product Targeted | Systems and networks in targeted sectors, with no specific software products highlighted. |
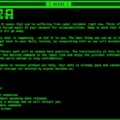
| Malware Reference | Files appended with .arcus extension; ransom note named Arcus-ReadMe.txt. |
| Tools Used | Tox chat for communication, email for backup contact, and unspecified malware payloads for encryption and exfiltration. |
| Vulnerabilities Exploited | Likely exploits unpatched vulnerabilities for initial access; specifics not disclosed. |
| TTPs | Double extortion tactics, use of exfiltration threats, strict escalation timelines, and reputational pressure. |
| Attribution | Linked to Arcus Media group; no specific nation-state ties mentioned. |
| Recommendations | Block malware execution, enable adaptive detection policies (e.g., SONAR, Carbon Black), secure endpoints, monitor RDP. |
| Source | Broadcom |
Read full article: https://www.broadcom.com/support/security-center/protection-bulletin/arcus-media-ransomware
Disclaimer: The above summary has been generated by an AI language model.



Leave a Reply