| Category | Details |
|---|---|
| Threat Actors | C.A.S (Cyber Anarchy Squad) |
| Campaign Overview | Attacking organizations in Russia and Belarus since 2022 with goals of data theft, financial and reputational damage. Exploit publicly available services. |
| Target Regions (Victims) | Russia, Belarus |
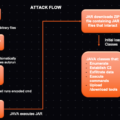
| Methodology | Exploit public-facing applications, use open-source RATs, and deploy multiple attack stages including credential access, discovery, and command control. |
| Product Targeted | Jira, Confluence, Microsoft SQL Server |
| Malware Reference | Revenge RAT, Spark RAT, Meterpreter, LockBit ransomware, Babuk |
| Tools Used | Revenge RAT, Spark RAT, Meterpreter, PowerShell, cURL, MS SQL, WMI, XenAllPasswordPro, BrowserThief, Mimikatz |
| Vulnerabilities Exploited | Unidentified vulnerabilities in publicly available services (Jira, Confluence, MS SQL) |
| TTPs | Initial access via public-facing apps (T1190), use of PowerShell and cURL for execution, persistence through net.exe, RATs, credential access, evasion |
| Attribution | Linked with other hacktivist groups like Ukrainian Cyber Alliance and DARKSTAR. |
| Recommendations | Perform regular testing, updating, integration of security systems, enforce password-protection policies, and configure EPP properly. |
| Source | Securelist by Kaspersky |
Read full article: https://securelist.com/cyber-anarchy-squad-attacks-with-uncommon-trojans/114990/
The above summary has been generated by an AI language model


Leave a Reply