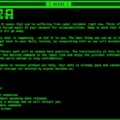
Tracking various indicators associated with different attacks, Huntress analysts have been able to identify specific indicators (threat actor workstation names, passwords associated with new user account creation or current account modification, CloudFlare tunnel tokens) that are associated with Akira ransomware infections. By detecting these indicators much earlier in the attack chain, organizations can inhibit or even obviate file encryption malware deployment. Read More


Leave a Reply