| Category | Details |
|---|---|
| Threat Actors | Howling Scorpius, the entity behind Akira ransomware-as-a-service (RaaS) and the Rust-based Megazord variant. |
| Campaign Overview | Active since March 2023, employing double extortion tactics with encryptors targeting Windows, Linux, and ESXi systems. Operates a Tor-based leak and negotiation site for ransom demands and victim data. |
| Target Regions/Victims | Small to medium-sized businesses in North America, Europe, and Australia. U.S. is the most affected country. |
| Methodology | Double extortion, spear phishing, exploiting VPN and RDP vulnerabilities, lateral movement via SMB, Active Directory credential harvesting, and VM targeting on ESXi. |
| Product Targeted | Windows, Linux, ESXi systems; virtualization platforms like VMware vCenter. |
| Malware Reference | Akira ransomware (Windows and Linux variants), Akira_v2, Megazord. |
| Tools Used | Mimikatz, LaZagne, Advanced IP Scanner, WinRAR, FileZilla, RClone, and Zemana antimalware driver for defense evasion. |
| Vulnerabilities Exploited | CVE-2020-3259, CVE-2023-20269 (Cisco products), vulnerabilities in VPNs and RDP, and unpatched systems. |
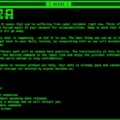
| TTPs | Double extortion, encryption using ChaCha20, AES, and RSA, credential theft (Kerberoasting, LSASS dumping), disabling antivirus and EDR, and creating VMs for ransomware execution. |
| Attribution | Howling Scorpius ransomware group, affiliates possibly connected to multiple operators for different strains like Megazord. |
| Recommendations | – Enable MFA and patch vulnerabilities promptly. – Monitor for anomalous RDP and SMB activity. – Secure virtualization infrastructure. – Deploy advanced endpoint protection like Cortex XDR. |
| Source | Palo Alto Networks Unit 42 research and analysis, 2023-2024. |
The post Threat Assessment: Howling Scorpius (Akira Ransomware) appeared first on Unit 42.
Disclaimer: The above summary has been generated by an AI language model.


Leave a Reply