| Category | Details |
|---|---|
| Key Takeaways | – Arctic Wolf observed intrusions involving Palo Alto Network firewall devices. – Affected devices downloaded payloads such as Sliver C2 and coinminer binaries. – Threat actors exploited PAN-OS vulnerabilities CVE-2024-0012 and CVE-2024-9474 for initial access. – Monitoring firewall logs for unusual usernames aids early detection. |
| Summary | – Palo Alto Networks disclosed vulnerabilities CVE-2024-0012 and CVE-2024-9474 in PAN-OS on November 18, 2024. – watchTowr published technical details enabling threat actor exploitation. – Arctic Wolf observed multiple intrusions shortly after, involving data exfiltration, malware deployment, and C2 activity. |
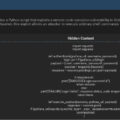
| Exploitation Details | – CVE-2024-0012 exploited for authentication bypass; CVE-2024-9474 for privilege escalation. – Logs showed Panorama console logins with bash commands in the username field. – Downloaded files included watchTowr.js, vicidial_sign.js, and others. |
| Command and Control | – Threat actors used curl or wget commands to download payloads from IP-based URLs. – Sliver C2, an alternative to Cobalt Strike, was retrieved and executed. – Scripts modified timestamps, cleared bash history, and created cron jobs for persistence. |
| Data Exfiltration | – Threat actors exfiltrated configuration files, credentials, and other sensitive data. – Used tar commands to archive files before exfiltration. – Attempts included dumping /etc/passwd, /etc/shadow, and SSH keys. |
| PHP Webshell | – An obfuscated PHP webshell was deployed. – It decrypted POST parameters, executed payloads via eval, and encrypted output. – Used MD5 padding for further obfuscation. |
| Coinminer Activity | – XMRig was deployed on compromised devices to mine cryptocurrency. – Network traffic to known XMRig addresses was observed. |
| Indicators of Compromise | – Various IPv4 addresses (e.g., 104.131.69[.]106, 46.8.226[.]75) served as payload and C2 servers.– Payloads included PHP scripts, Sliver C2 frameworks, and coinminer binaries. – URLs like 46.8.226[.]75/1.txt hosted malicious files. |
| Remediation | – Monitor firewall logs for unusual username patterns. – Restrict access to management interfaces to trusted internal IPs. – Apply patches for CVE-2024-0012 and CVE-2024-9474 immediately. |
| Detection Opportunities | – Look for bash commands in the username field of Panorama logins. – Flag files downloaded over HTTP from unexpected IPv4-based URLs. – Monitor for automated file modifications and timestamp changes. |
Read full article:https://arcticwolf.com/resources/blog/arctic-wolf-observes-threat-campaign-targeting-palo-alto-networks-firewall-devices/
Disclaimer: The above summary has been generated by an AI language model



Leave a Reply