| Category | Details |
|---|---|
| Threat Actors | Bootkitty creators (unknown); proof-of-concept UEFI bootkit targeting Linux |
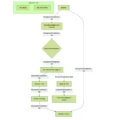
| Campaign Overview | First UEFI bootkit targeting Linux systems, specifically Ubuntu; designed to bypass UEFI Secure Boot and preload ELF binaries during system startup |
| Target Regions (Victims) | Linux systems (Ubuntu versions) |
| Methodology | Patches Linux kernel functions, hooks GRUB, disables kernel signature verification, and deploys ELF binaries |
| Product Targeted | Linux (Ubuntu) systems |
| Malware Reference | Bootkitty (UEFI bootkit for Linux), related BCDropper kernel module |
| Tools Used | Bootkitty bootkit, GRUB hooking, UEFI Secure Boot bypass, ELF binaries |
| Vulnerabilities Exploited | UEFI Secure Boot bypass, kernel signature verification disabling |
| TTPs | Patching GRUB and kernel functions, ELF binary preload, UEFI Secure Boot bypass, memory patching |
| Attribution | Uncertain; considered a proof of concept, not active malware |
| Recommendations | Be cautious of UEFI bootkits, maintain UEFI Secure Boot, monitor systems for abnormal memory patches and GRUB modifications |
| Source | WeliveSecurity |
Read full article: https://www.welivesecurity.com/en/eset-research/bootkitty-analyzing-first-uefi-bootkit-linux/
Disclaimer: The above summary has been generated by an AI language model



Leave a Reply