The Power of Force Multiplication
“Threat intelligence is like the Force: it should flow through everything.”
-Andy Pendergast, Co-Creator of the Diamond Model of Intrusion Analysis and Co-Founder of ThreatConnect

“Remember, a Jedi can feel the threat intelligence flowing through them.”
-Obi-Wan Kenobi (probably)
ThreatConnect is launching a new product to complement our Threat Intelligence Operations (TI Ops) platform. It provides real-time, contextual access to threat intelligence across every tool security analysts use. Read on to learn more.
Close your eyes and reach out with your feelings: imagine a SOC analyst, buried under alerts, struggling to connect the dots: “Is this a threat? Do I need to escalate? Do I need to take action? Is it a wild goose chase?” The answers are there, but the needed intel and insights are spread across so many different intelligence sources that it feels impossible to find the right context to make a decision. Now imagine if, instead, the intelligence the analyst needed flowed as easily through them as the Force for a Jedi Master.
Making threat intelligence an essential part of the cybersecurity organization has been at the heart of ThreatConnect since our founding; CTI should flow through everything: reducing false positives in the SOC, speeding MTTR in Incident Response, and helping threat hunters stay on target. It’s part of why we introduced the Evolved Intelligence Cycle.
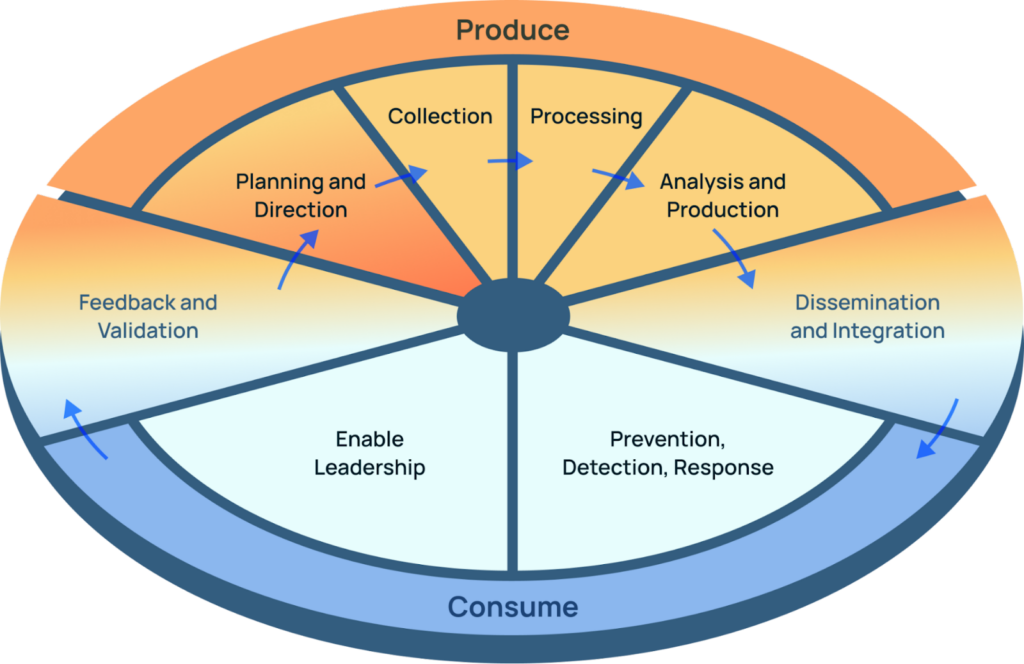
Intel production is the beginning of cyber defense, not the end.
Threat intelligence exists to inform action: it’s as much about the Consumers of intel as historically it’s been about the Producers. For a long time, the critical “Dissemination and Integration” bridge step has been a challenge. How does an intel analyst get the right intel into the right hands at the right time? How does a SOC analyst receive that intel where and when they need it? How do you let the threat intelligence flow through you?
That’s where the new Polarity Intelligence Edition comes in. Unlike legacy TIPs, which focus primarily on feed aggregation, the pairing of our TI Ops platform with the new Polarity Intelligence Edition makes it easier for the entire cybersecurity organization (SOC, IR, threat hunting, etc.) to access intelligence when and where it’s needed – without even needing to log in to a separate platform!
Bridging Intel Producers and Intel Consumers
What good is intelligence if it can’t be operationalized? Unused intelligence wastes time and effort and does nothing to improve organizational security posture. Traditional threat intelligence platforms (TIPs) focus on feed aggregation, which provides a single view of the truth, but it often sits there unused. That intel can be deployed to tools like SIEMs, but not every analyst works inside the SIEM, or the information in the SIEM doesn’t give them fast enough answers. Further, as highlighted below, it’s not always presented in an easily actionable way. The result is that smart, valuable analyst resources are wasted, and threats fall through the cracks.
Problems with other traditional solutions include:
- Sharepoint, Google Drive, email, and even legacy threat intelligence platforms create massive gaps in consistency and accuracy
- RFIs and other “pull” style implementations take time to fulfill and require active participation from the consumer.
- Threat Intelligence Browser Extensions can provide context on IOCs, CVEs, and other intelligence but are often focused on the intelligence from a single provider and are always limited to operating within the browser and thus cannot help when working in other desktop applications.
- SOAR tools are designed to automate, not disseminate, and leveraging them to provide threat intelligence requires a tremendous amount of configuration. Plus, they offer limited access to more targeted, relevant intel.
- Federated search tools that purport to solve this problem require considerable setup and investment in large data lake infrastructure.
On top of that, users may need CTI insights whenever and wherever they work – none of those solutions can do that. The end result is that:
- Traditional methods of disseminating threat intel leave gaps,
- Manual processes slow down and complicate intel production,
- Response times are slowed down, and
- Existing tools require complex setups and only provide partial solutions.
This is not the way.
Introducing Polarity Intel Edition
ThreatConnect offers the only TI Ops platform that effectively streamlines all steps in the Evolved Intel Cycle. With Polarity Intel Edition, we now offer new capabilities dedicated to usable dissemination that are able to fully close the loop.
Thanks to ThreatConnect’s recent acquisition of Polarity, we’re excited to announce Polarity Intel Edition: a low-friction way to consume intelligence when they need it, literally while doing their analysis on their screen. In CTI terms, Polarity Intel Edition allows our customers to fully close the intel cycle with minimal effort. It’s specifically designed to smooth the way for intel consumers like SOC analysts, incident responders, and threat hunters to take advantage of what is produced by CTI teams. It integrates seamlessly with our TI Ops Platform so the intel can flow freely and easily. It delivers real-time insights, access to many popular intel integrations, and a lighting-fast setup right out of the box.
Specifically, Polarity Intel Edition provides:
- Federated Search across your essential threat intelligence and enrichment data for insights and contextualization (e.g. ThreatConnect, Premium Intel Providers, VirusTotal, Shodan, etc).
- Frictionless access to the aggregated intel in our TI Ops platform, including our AI-powered Automated Threat Library, which brings in hundreds of blogs and government bulletins and turns them into human- and machine-readable threat intelligence.
- Ground truth inside our Collective Analytics Layer includes data like reported false positives, measures of analyst interest and real-world observations, malware classification, DNS, historical geolocation, and more. Paired with the Automated Threat Library, it’s the perfect way to get started with intelligence or supplement a mature program.
- The AI Assistant in Polarity interfaces with approved GenAI LLMs to gain insights faster and generate summaries on intel.
- Directly add new and update existing threat intelligence inside our TI Ops platform.
Let’s dive a little deeper into the specific capabilities.
It’s Real Time
Polarity: Intel Edition provides a real-time data overlay of in-context intelligence that flows to your analysts wherever, whenever, and to whomever it’s needed. This saves time, allows for on-demand searching and correlation, and ensures that no one misses out on impactful CTI. This works whether you’re on the web or using desktop or native applications. It also means there’s no need to go through multiple interfaces to access popular intel sources like Flashpoint, Recorded Future, VirusTotal, Silent Push, Greynoise, Mandiant Threat Intel, and many more.
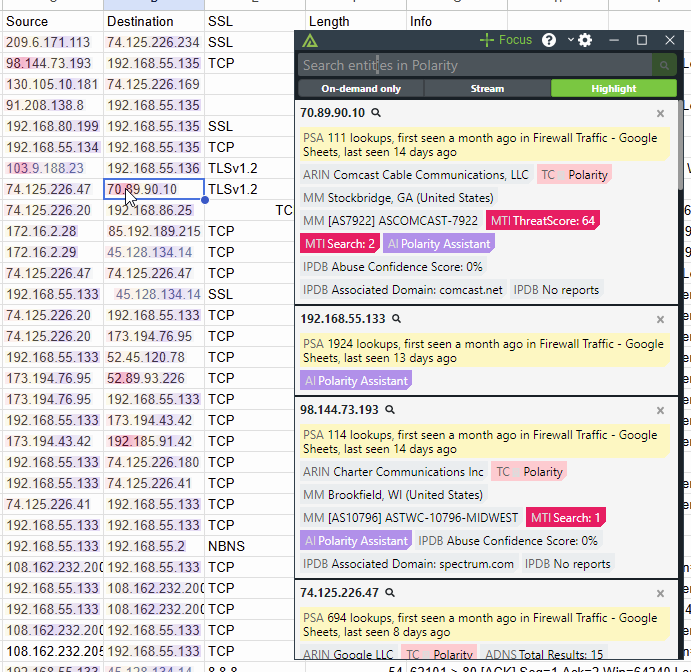
Our real-time overly highlight indicators of compromise with the most relevant intelligence.
It’s Fast
While there might be similar solutions out there, Polarity is the only one that requires almost no setup. We offer 50 integrations (with more available in our Enterprise edition!) that can be turned on with a simple “on” switch (literally). This helps analysts integrate large, relevant datasets with a very low learning curve.
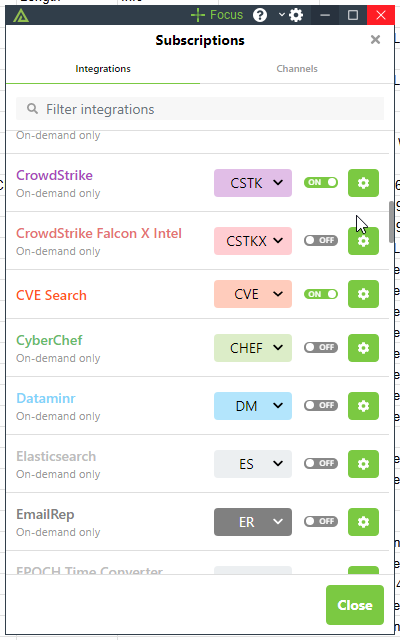
Integrations are ready to go right out of the box.
It Has AI that Actually Does Something Useful
As part of this low-cost offering, we’re also including AI summaries. That means a busy analyst can get a quick report of all the data available on an indicator from all of our popular intelligence integrations. It’s like having an intern run out, collect data from dozens of different sources, come back, and compile it into a report (hopefully without any mistakes) – except this LLM-based intern does it in seconds.
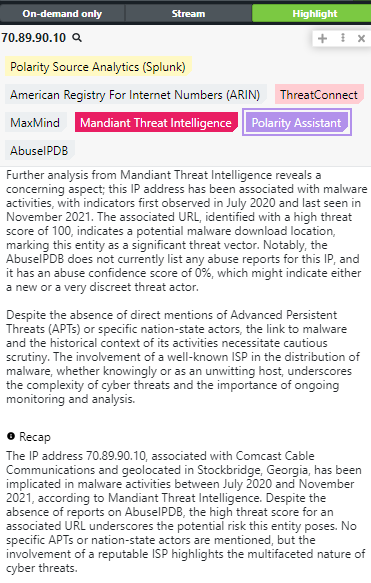
All of the intel sources are consolidated via AI into an easily human-readable summary.
It Closes the Intel Cycle
If you’ve chatted with me over the years, you’ll know that one of my favorite slices of pie in the intel cycle is Feedback and Validation; it’s also one we often hear from customers. As a customer told me once, “Our most valuable intelligence feed is our own SOC and IR teams.” Polarity: Intel Edition allows users to send indicators, insights, tags, and more back into ThreatConnect so that those insights can add ground truth to your single source of truth.
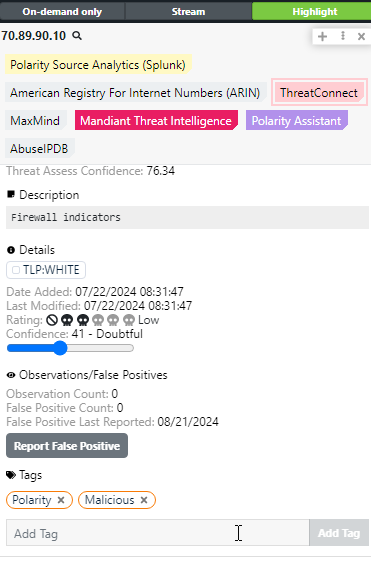
Report false positives, adjust threat ratings, and organize indicators in ThreatConnect’s TI Ops platform directly from the Polarity overlay.
I Want to Learn the Ways of the Force
To sum up, the new Polarity Intel Edition (PIE) revolutionizes how your team consumes and acts on threat intelligence. With real-time, in-context data overlays and AI-powered summaries, PIE ensures that crucial intel flows seamlessly into the hands of those who need it, precisely when they need it.
Whether you’re a CTI analyst producing heroic intelligence but don’t have an easy way to share that story, whether you’re a SOC or IR analyst looking to improve efficiency and reduce false positives, or whether you’re a team leader who wants to help your team improve key metrics like MTTR, sign up for a demo now!
Beyond the Basics
If Polarity Intel Edition has whet your appetite for the industry’s first Contextual Intelligence and Response Platform that does real-time data augmentation across all your tools, then the full edition of Polarity is an easy upgrade. Take a look here to learn more.

Learn More
Polarity Intel Edition is now available as a cost-effective add-on module for all ThreatConnect TI Ops customers and for organizations using legacy threat intelligence platforms. Learn more at https://threatconnect.com/polarity-intel-edition/ or register to attend an informational webinar on October 2, 2024, at 9:00 AM PT / 12:00 PM ET / 5 PM BST.
The post ThreatConnect Launches Polarity Intel Edition to Streamline Intelligence for SecOps Teams appeared first on ThreatConnect.



Leave a Reply