| Section | Details |
|---|---|
| Threat Actors | Lazarus Group (North Korea-linked) |
| Campaign Overview | Operation 99 targets freelance Web3 and cryptocurrency developers using fake recruiters and malicious GitLab repositories to deliver malware. |
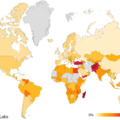
| Target Regions (Victims) | • Italy (primary concentration) • Argentina, Brazil, Egypt, France, Germany, India, Indonesia, Mexico, Pakistan, Philippines, U.K., U.S. (secondary concentration) |
| Methodology | • Fake recruiters on LinkedIn luring developers. • Victims clone malicious GitLab repositories that connect to C2 servers. • Malware is deployed to steal sensitive data. |
| Product Targeted | Web3 and cryptocurrency development environments |
| Malware Reference | Main5346, Main99 (downloader), Payload99/73, Brow99/73, MCLIP |
| Tools Used | Fake LinkedIn profiles, Malicious GitLab repositories |
| Vulnerabilities Exploited | Social engineering tactics (fake recruiters and GitLab links) |
| TTPs | • Fake recruitment tactics via LinkedIn. • Malware embedded in cloned GitLab repositories. • Modular malware design capable of targeting multiple OS platforms. |
| Attribution | Lazarus Group (North Korea) |
| Recommendations | • Avoid clicking links from untrusted recruiters. • Use strong endpoint security to detect and block malicious repositories. • Monitor development environments for unauthorized access. |
| Source | The Hackers News |
Read full article: https://thehackernews.com/2025/01/lazarus-group-targets-web3-developers.html
The above summary has been generated by an AI language model



Leave a Reply