| Category | Details |
|---|---|
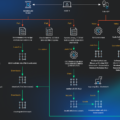
| Threat Actors | TA455 (Linked to Iranian Charming Kitten/APT35) |
| Campaign Overview | Espionage campaign targeting the aerospace industry using fake LinkedIn recruiter profiles and malicious documents to distribute malware. |
| Target Regions | Israel, UAE, Eastern Europe, possibly Turkey, India, Albania |
| Methodology | Impersonation of recruiters on LinkedIn; use of fake recruiting websites; distribution of malicious documents disguised as legitimate job-related files. |
| Product Targeted | Aerospace, aviation, and defense industry systems |
| Malware Reference | SnailResin, SlugResin |
| Tools Used | Fake LinkedIn profiles, fake websites, Cloudflare, GitHub, Microsoft Azure Cloud |
| Vulnerabilities Exploited | Exploitation of human trust via social engineering (LinkedIn profiles and job-related content); no specific software vulnerabilities mentioned. |
| TTPs | Impersonating recruiters; Using trusted platforms to mask infrastructure; Delivering backdoor malware via legitimate-looking documents |
| Attribution | TA455 linked to Iran; potential collaboration or shared methods with North Korean groups Kimsuky and Lazarus. |
| Recommendations | Educate employees about fake recruiter schemes; Strengthen defenses against phishing and social engineering; Monitor traffic from legitimate services like Cloudflare and GitHub. |
| Source | The Record |
Read full article: Read More
Disclaimer: The above summary has been generated by an AI language model.



Leave a Reply