| Category | Details |
|---|---|
| Threat Actors | – Charming Kitten |
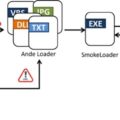
| Campaign Overview | – BellaCiao malware family first surfaced in April 2023 – Combines stealthy persistence (webshell) with covert tunnel creation – New variant, BellaCPP, observed in Asia in 2023 |
| Target Regions | – Asia (specific computer infected) – Entities identified via PDB paths indicating target entity and country |
| Methodology | – Use of descriptive PDB paths for versioning and targeting – XOR decryption for DLL loading – Domain generation for covert tunneling – Exploiting Windows services (e.g., running malware as a service) |
| Products Targeted | – Windows systems (e.g., DLLs in C:\Windows\System32) |
| Malware Reference | – BellaCiao (.NET-based malware family) – BellaCPP (C++ variant) |
| Tools Used | – PDB path analysis for tracking – Encrypted DLLs (e.g., D3D12_1core.dll)– Domain generation: <5 random letters><target identifier>.<country code>.systemupdate[.]info |
| Vulnerabilities Exploited | – Leveraging persistence through Windows services – SSH tunneling for covert communication |
| TTPs | – Iterative malware development with versioning (MicrosoftAgentServices versions) – Covert tunneling via DNS and SSH – Usage of descriptive PDB paths for operational insights |
| Attribution | – High confidence attributed to Charming Kitten – Links to previous domains and infection behavior from older BellaCiao samples |
| Recommendations | – Monitor for unusual domain activity and service behavior – Conduct deep investigations to identify undetected samples – Update detection rules to cover evolving malware family |
| Source | Securelist by Kaspersky |
Read full article: https://securelist.com/bellacpp-cpp-version-of-bellaciao/115087/
The above summary has been generated by an AI language model


Leave a Reply