We recently had the opportunity to have a chat interview with an actor going by the alias “Miyako” who operates on a well-known darknet forum – BreachForums. Miyako is an initial access broker (IAB), a malware developer, and one of the admins of the Hellcat group.
We had also recently interviewed another actor “Sukob”, loosely affiliated with the Hellcat group. Click below to read more.
We had recently interviewed an actor going by the alias “Sukob” an initial access broker (IAB) and malware developer, who is loosely affiliated with the Hellcat group. To read more, please click Here.
This interview offers insight into Miyako’s motivations, strategies, and the tools used in cyber operations. Miyako demonstrates a calculated and sophisticated approach with a focus on targeting high-value sectors, maintaining strict anonymity, and exposing weaknesses in cybersecurity systems. The discussion also touches on Miyako’s connection with the Hellcat group, a preference for operating independently and focusing on financial gain rather than engaging in high-profile, riskier activities like ransomware attacks.
Through this conversation, we uncover detailed insights into the tactics, techniques, and procedures (TTPs) employed by Miyako, offering a window into the operations of a skilled cybercriminal.
Stay Updated with Our Newsletter
Key Findings:
Motivation:
- Miyako engages in cyber activities primarily for financial gain and technical challenges.
- Describes the work as a means to highlight global cybersecurity weaknesses.
Association with Hellcat Group:
- One of the admins of the Hellcat group, having participated in joint operations targeting critical infrastructure.
- Prefers independent operations to ensure better operational security.
Targeting Preferences:
- Focuses on sectors like finance, healthcare, and energy with high-value data.
- Targets countries with advanced technology and strong economies, while avoiding CIS countries.
Methodologies and Tools:
- Conducts OSINT to identify vulnerabilities, technologies, and employees within target organizations.
- Leverages spear phishing, unpatched vulnerabilities, and occasionally zero-days to gain access.
- Uses tools such as TheHarvester, maltego, EvilClippy, Shellter, and typo-squatting to execute phishing campaigns.
Persistence Techniques:
- Employs rootkits, backdoor accounts, and custom malware to maintain access.
- Exfiltrates credentials and uses scheduled tasks to ensure persistence.
Evasion and Anonymity:
- Operates through VPN layers, TOR nodes, and burner devices to maintain anonymity.
- Avoids identifiable patterns in code and communication to prevent attribution.
Tactics Against Incident Response:
- Disables logging, encrypts data exfiltration, and plants misleading breadcrumbs to delay response efforts.
- Spreads across multiple devices, including IoT systems, to maintain access.
Philosophy:
- Describes actions as both financially driven and a critique of inadequate cybersecurity measures in organizations.
Advice to Organizations:
- Encourages businesses to train employees, implement multi-factor authentication, maintain rigorous patch management, adopt zero-trust architectures, and conduct regular penetration testing to enhance cybersecurity.
The Interview
Below we have presented the questions and answers with no modification.
Question: Welcome to the Osint10x interview, Miyako! As this is our first engagement, can you please tell us about yourself and your work?
Miyako: Thank you for having me. I operate under the alias Miyako and specialize in targeted breaches of corporate and government networks. My focus is on gaining high-value data, particularly intellectual property and personal information, which can be monetized or weaponized. My operations are global, with a preference for sectors like finance, healthcare, and tech.
Question: Why did you decide to work in this field and what keeps up the motivation?
Miyako: It is fun, easy money. Making headlines forces me to stay sharp and evolve/learn new things. I try not to sell access that can endanger lives, but other than that I see it as if I didn’t break in someone else would very soon, so I don’t feel like I am causing an insane amount of harm to companies. Again, if they cared enough, they would have patched their systems.
Fun fact: The major USA Telecom Breach that has been going on is due to unpatched Cisco Routers. A 2017 CVE that is being exploited on major US Telecom networks. It is funny to know that americans are this lazy.
The motivation for me is mostly money and getting better. Every day there is a new project, and every experience combines in the long-run to help with other new projects. I like learning something a week ago, and then using it as a piece of something new I am working on today.
Maybe more of a moral issue with all of the governments I have infiltrated, but I don’t see a problem breaking into a government that doesn’t have any problem breaking into the devices of their civilians.
Question: What does your day look like away from the keyboard? Do you go for a run, surf, yoga, or are you always in the Twilight Zone?
Miyako: I dedicate most of my time to research, reconnaissance, and developing new exploits. That said, I value staying sharp, so I practice martial arts and meditation to maintain focus and discipline.
Question: What’s your association with the Hellcat group, and how do you contribute? Who is the admin of Hellcat?
Miyako: I have collaborated with Hellcat in the past on joint operations targeting critical infrastructure. I handled the phishing and privilege escalation phases. However, I prefer to operate independently to maintain operational security.
Hellcat doesnt have a ‘Leader’ but me, pryx, grep are admins.
Question: We noticed multiple big companies have been breached by you. Which geo and sector interests you, and why?
Miyako: I prioritize sectors with high-value data like financial institutions, healthcare, and energy. Geographically, I focus on countries with strong economies and advanced tech industries, reward justifies the effort. I DO NOT attack CIS countries.
Question: What’s your approach to target a network—starting with selecting a target to compromising it? Can you give us a general overview? Do you develop malware as well?
Miyako: I begin with OSINT to profile the organization—identifying employees, technologies, and vulnerabilities. Then, I craft phishing campaigns or exploit known CVEs to gain initial access. Once inside, I escalate privileges, deploy persistence mechanisms, and exfiltrate data. Sometimes 0days are included in the process.
Malware sometimes for small projects, like backdoors. I made a c2 for infected npm packages recently.
Question: If you are comfortable, how long have you been working as a hacker? And which all groups did you collaborate with?
Miyako: I’ve been in this field for over a decade. During that time, I’ve collaborated with groups like Hellcat and several darknet marketplaces for resource sharing and selling access to breached systems.
Question: What are the most common security flaws you have witnessed so far?
Miyako: Weak credentials, unpatched software vulnerabilities, and poor email security are the most common flaws. Human error, especially phishing susceptibility, is prominent in most organizations.
Question: Your activity covers a range of sectors, from tech companies to government organizations. How do you typically gain initial access to these databases?
Miyako: Phishing is highly effective, particularly spear phishing tailored to key personnel. Exploiting zero-day vulnerabilities or unpatched software is another reliable method.
Question: Any example of phishing campaigns you have carried out in the past?
Miyako: All I can say for this one is that even FBI employees can fall victim to malicious PDF files. There are FBI employee data leaks on the internet with hundreds of lines of ‘fbi.gov’ email addresses. All it takes is one human error.
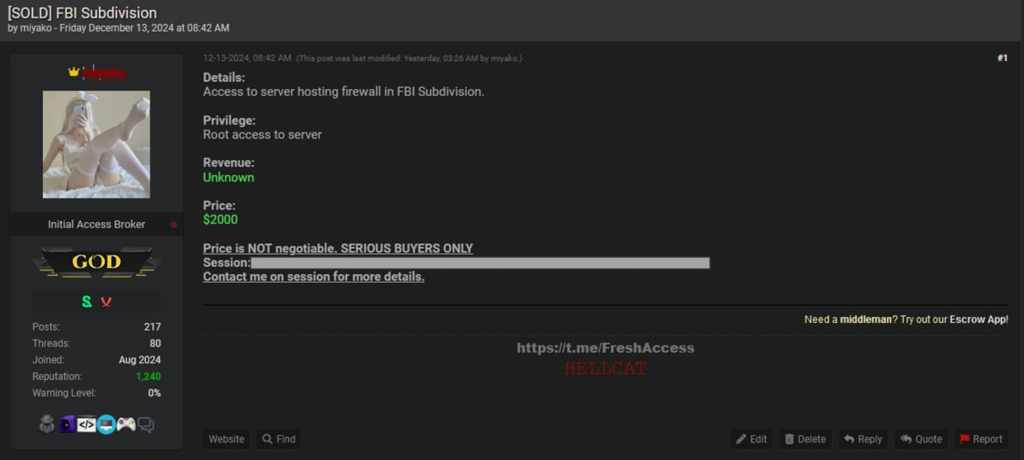
This was 2 days campaign. The emails were already posted long ago. SAMPLE:
<THE SHARED SAMPLE REDACTED FOR PRIVACY>Question: What are the tools you commonly use to run your campaign?
Miyako: TheHarvester, maltego, and hunter.io for OSINT and generating potential email formats. EvilClippy helps inject macros into Office documents. Shellter injects payloads into PDFs. PeCloak obfuscates these PDF payloads. Ngrok for temporarily exposing phishing pages onto the open internet.
Not all phishing campaigns require a malicious site, sometimes all you need is the email to deliver the payload.
Typo-squatting is a common practice when phishing. It is the act of registering similar domain names to the company you are trying to phish.
ex: I am phishing microsoft.com, so I register microsft.com
Question: Once access is obtained, what techniques do you use to maintain persistence within the target system?
Miyako: I deploy rootkits, backdoor accounts, and scheduled tasks to ensure persistence. I also exfiltrate credentials and create custom malware that blends into the system’s operations.
Question: Which bulletproof hosting providers do you prefer (if any)?
Miyako: 4vps.su
Question: Forums like these come with their own risks. Have you ever faced challenges or conflicts with others in this space? If so, how do you overcome those situations?
Miyako: Conflicts are common. I mitigate this by maintaining anonymity, leveraging cryptographic communication, and staying neutral in disputes to avoid unnecessary attention.
Question: When a target initiates incident response procedures, what steps do you take to avoid detection or removal?
Miyako: I use tactics like encrypting data exfiltration, disabling logging, and deploying misleading breadcrumbs to slow down incident response teams. I also pivot to other systems within the network to keep my access alive.
Question: What measures do you implement to anonymize your activities and prevent attribution?
Miyako: I route all operations through layers of VPNs and TOR nodes, use burner devices, and maintain strict OPSEC. My code and communication avoid linguistic patterns that could lead to attribution. I also diversify my monetization efforts to avoid creating patterns.
Question: You’ve been selling leaked databases for a while. Do you see this as a long-term plan, or are there other areas in the cybersecurity space that interest you?
Miyako: Selling databases is just one revenue stream. I’m also exploring ransomware-as-a-service (RaaS) and custom exploit development for other operators. Long-term, I aim to refine my tactics and build a network of trusted collaborators.
Question: You’ve targeted diverse organizations, from multinationals to local companies. Is there a broader motive or philosophy guiding your actions?
Miyako: Beyond profit, I see my work as exposing the fragility of digital systems. The chaos I create serves as a wake-up call to those who ignore cybersecurity.
Question: What advice do you have for companies to better defend against such attacks?
Miyako: Focus on training employees, implementing multi-factor authentication, and maintaining a robust patch management process. Zero-trust architecture and regular penetration testing can also go a long way in reducing risks.
Question: Thank you for your time, Miyako! Is there something else that we may have missed that you would like to tell us?
Miyako: Always assume you’re a target. The mindset of “it won’t happen to us” is the greatest weakness of any organization.
Disclaimer
This interview is provided for informational purposes only and does not express approval, support or agreement with any actions mentioned in the text. The author of the publication is not related to the activities described in the interview and is not responsible for any consequences of using the information provided.
The interview materials are intended to raise public awareness of modern cyber threats and the methods of cybercriminal groups. The publication of this text does not constitute propaganda of illegal activity and does not encourage violation of laws.
Readers are advised to always observe legal regulations and consult with the appropriate authorities if they have questions about the topics covered in this interview.


Comments (3)
Threat Actor Interview: Spotlighting on Pryx– Admin of the Hellcat Ransomware Group - Osint10xsays:
December 17, 2024 at 10:55 pm[…] interviewed two actors “Sukob”, loosely affiliated with the Hellcat group and ”Miyako“, one of the admins of the Hellcat […]
Emerging Hellcat Ransomware Group Targets Government Entities and High-Revenue Organizations - Osint10xsays:
December 28, 2024 at 2:12 pm[…] with potential activity expected to emerge in 2025. Curious to learn more, we reached out to Miyako, one of the administrators of the Hellcat ransomware group, for a conversation. Miyako revealed […]
Prolific Threat Actor “miyako” Advertises Access to China Telecom Data Center - FedKite: AI-Driven Solutions and Resources for Federal Inmates & Familiessays:
January 18, 2025 at 8:45 am[…] OSINT interview and threat actor profile have brought “miyako” some publicity in the cybersecurity […]