| Category | Details |
|---|---|
| Threat Actors | MUT-1244 (Mysterious Unattributed Threat), targeting security researchers and offensive actors. |
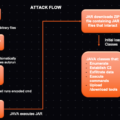
| Campaign Overview | Phishing campaigns and trojanized GitHub repositories were used to exfiltrate over 390,000 credentials and sensitive information like SSH keys and AWS access keys. |
| Target Regions (Victims) | Offensive actors, pentesters, security researchers, and malicious threat actors. |
| Methodology | Trojanized GitHub repositories with fake PoCs for CVEs, phishing emails targeting academics, use of malicious npm dependencies, ClickFix-style attacks on Linux systems. |
| Product Targeted | WordPress accounts (via yawpp tool), credentials stored in ~/.aws directories, SSH keys, and system information. |
| Malware Reference | Malicious npm package “@0xengine/xmlrpc” and “0xengine/meow”; second-stage payloads delivered via backdoored files, PDFs, Python droppers, and malicious npm dependencies. |
| Tools Used | Fake GitHub repositories, phishing emails, XML-RPC API exploitation, malicious npm packages, and second-stage payloads for data exfiltration. |
| Vulnerabilities Exploited | Exploitation of victim trust through fake PoCs, ClickFix-style attacks against Linux, and abuse of npm packages for malware delivery. |
| TTPs | Use of trojanized repositories, phishing with AI-generated profiles, exfiltration of credentials to Dropbox, multi-vector malware payloads, targeting Linux systems with shell commands. |
| Attribution | Based on campaign activity and telemetry, MUT-1244 is a notable threat actor targeting individuals in the cybersecurity community. |
| Recommendations | – Avoid downloading unverified PoCs from GitHub. – Implement strict monitoring of credential usage. – Regularly scan for malicious dependencies in projects. – Train users to recognize phishing and ClickFix-style attacks. – Use endpoint protection tools. |
| Source | The Hackers News |
Read full article: https://thehackernews.com/2024/12/390000-wordpress-credentials-stolen-via.html
The above summary has been generated by an AI language model



Leave a Reply